251030_dragosCTF learning record
251030_dragosCTF learning record
cvestone- Contact Authors
- Attachments
- EventInfo
- Dragos Trivia
- Phishing & Initial Access
- ICS Windows Event Log Analysis
- ICS PCAP Analysis
- Binary Analysis
- Reverse Engineering & PCAP Analysis
- Forensics Analysis
In the full-stack CTF player program, this article will be continuously updated with recreated learning content
Your Partner in OT Cybersecurity | Dragos
Attachments
Release 251030_dragosCTF · cvestone/cvestone.github.io · GitHub
EventInfo
2025 Dragos Capture the Flag (CTF) Competition Summary & Results | Dragos
Dragos Trivia
Dragos Trivia - Q1
Desc
The 9th Annual Year In Review OT/ICS Cybersecurity Report (2025) report summarizes cybersecurity headlines, the ICS/OT threat landscape, case studies from the Dragos frontlines, and security trends seen at industrial organizations. Dragos tracked 23 threat groups targeting industrial control organizations.
How many threat groups were active in 2024?
▼ View Hint
Head over to the Dragos website and look at the resources.
Dragos Trivia - Q2
Desc
Which Ransomware group was the sixth most active group that Dragos tracked in 2024?
Dragos Trivia - Q3
Desc
Dragos tracked new Threat Groups in 2024. Which new Threat Group has been known to affect the Rail Industry?
Dragos Trivia - Q4
Desc
Investigators found that attackers gained access to ACME’s vendor network through a phishing email targeting a contractor, allowing lateral movement into poorly segmented industrial systems.
What critical security control, as defined by the 5CCs, could have prevented this attack from escalating into an OT compromise, according to Dragos’s guidance on KAMACITE?
▼ View Hint
Open YIR
▼ View Hint
Review the KAMACITE Technical Update
▼ View Hint
Review the SANS ICS 5 Critical Controls
Phishing & Initial Access
Undercover Ops(√)
Desc
Use the attached PCAP to answer the next two questions.
Sophia, a project manager at ACME Corp., just received an email from her “IT team”, informing her that her current Windows 10 host needs to be updated to the latest, approved OS - Windows 11. The “IT team” placed proper instructions in her Downloads directly and asked Sophia to follow the necessary steps to complete the update.
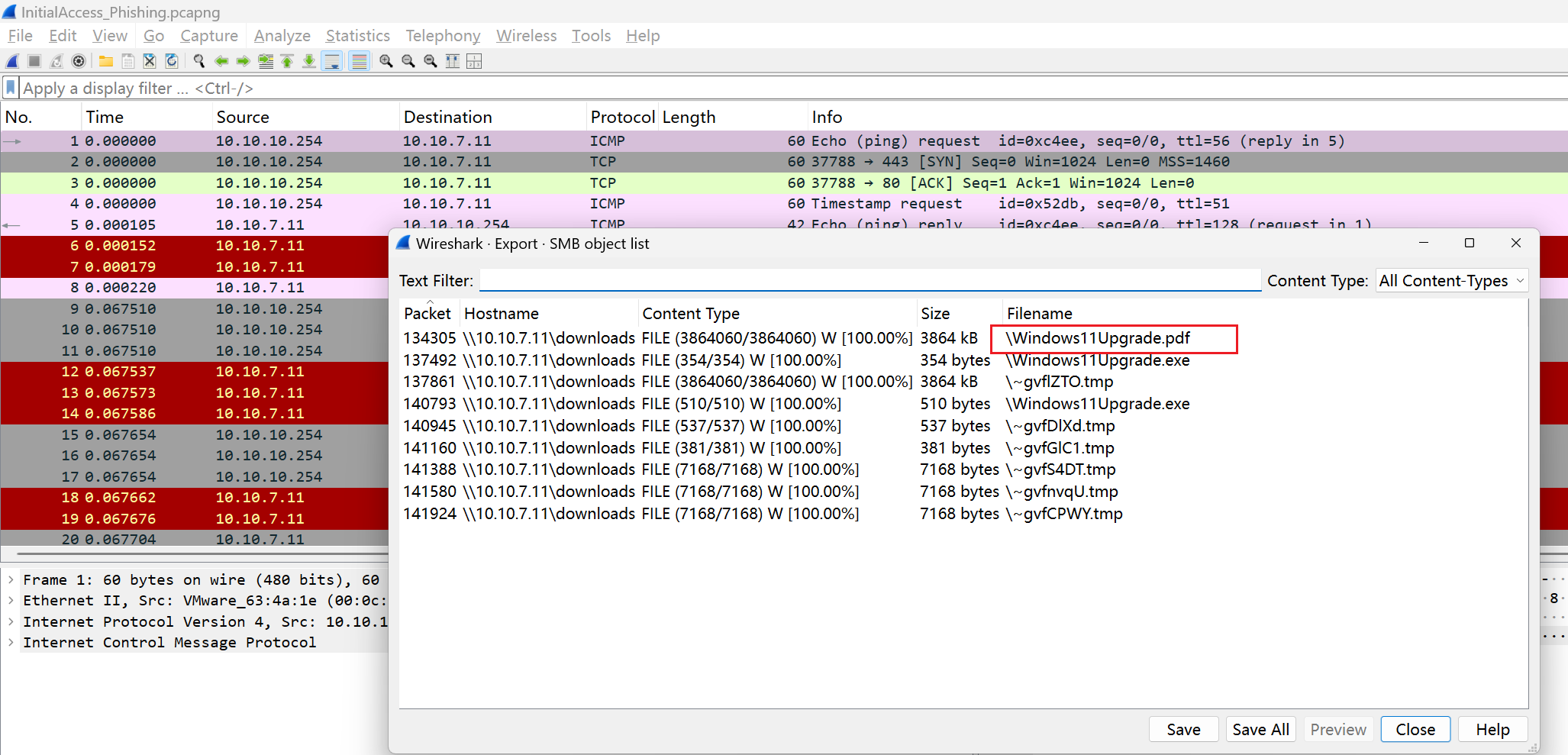
Reviewing the PCAP will show that multiple files were transferred across the network. What was the first filename transferred onto Sophia’s host?
▼ View Hint
Is there a place in Wireshark where we can view transferred files?
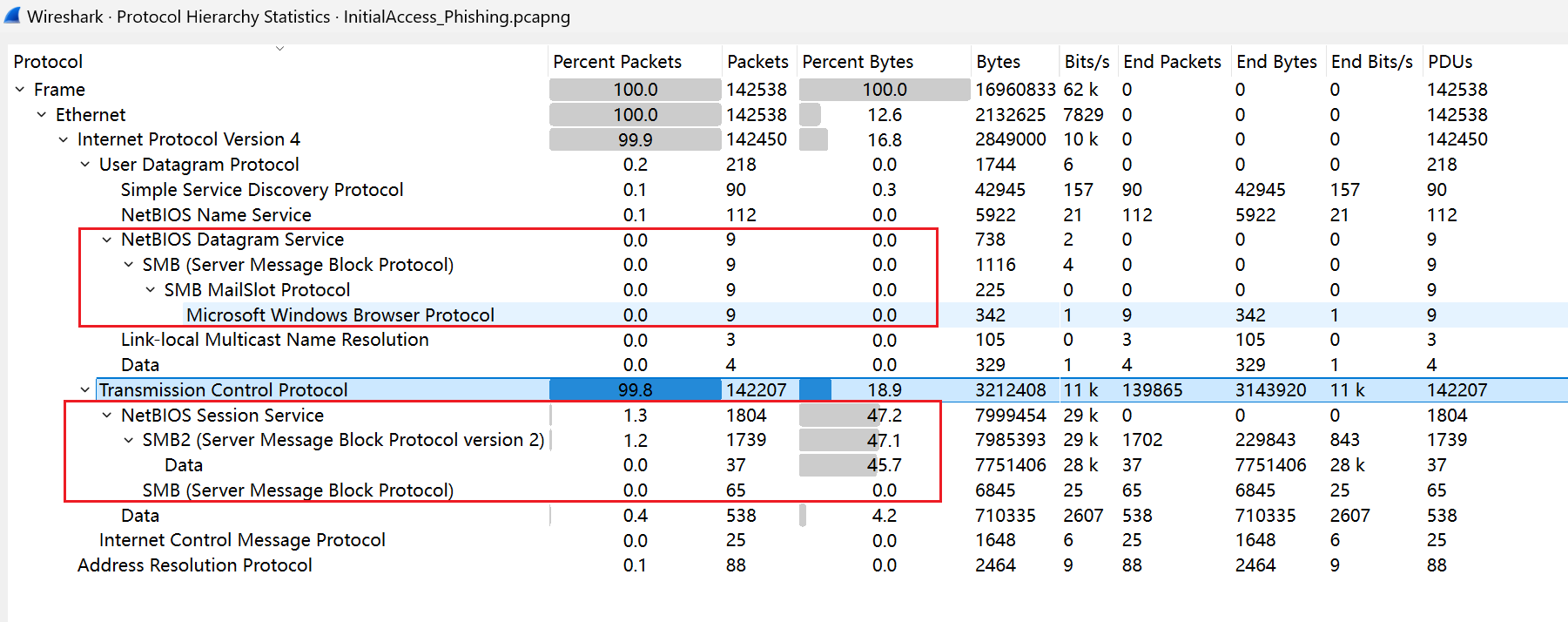
Key Points:SMB Protocol Traffic Analysis (Object Export)
Based on the hint to look for protocols related to network file transfers, the first ones that come to mind are FTP and SMB. Let’s first check the protocol hierarchy:
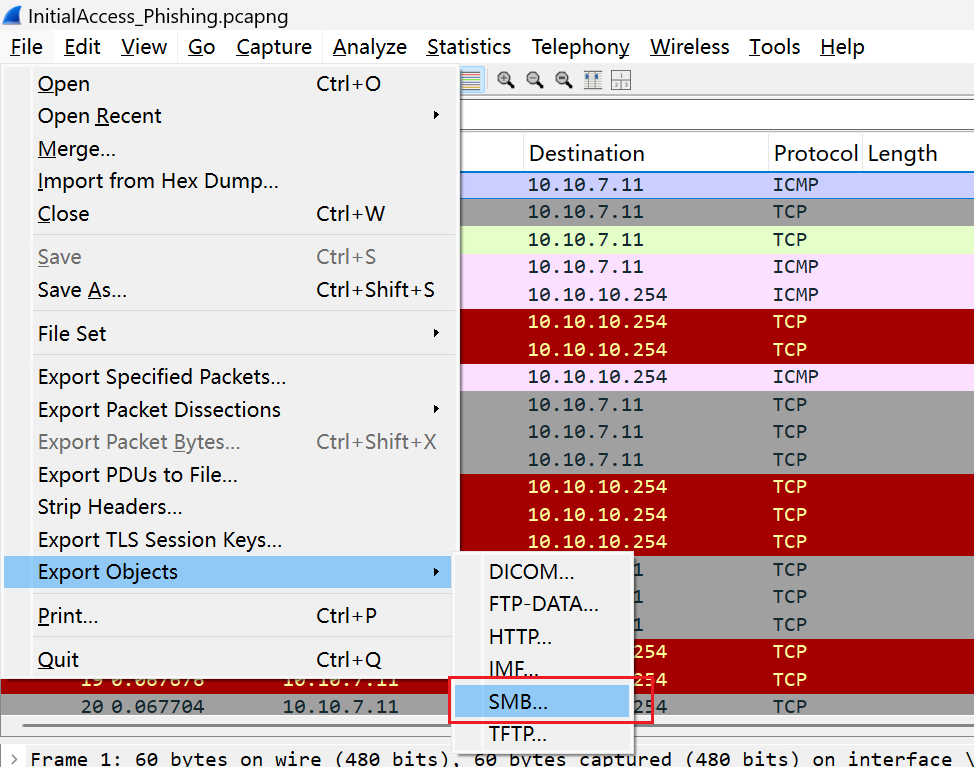
Clearly, only SMB is present. We can directly export the SMB objects:
This already reveals all the downloaded filenames. According to the chronological order, the first file is as follows:
Where are you going?
Desc
During the investigation, the ACME IR team identified that two files were shared with Sophia: the original PDF and an EXE. The EXE was never meant to upgrade the operating system to Windows 11, but rather it hosted a malicious, reverse-shell payload.
What IP Address and Port did this payload call back to?
Flag Format: IPAddress:Port
▼ View Hint
Wireshark supports communication statistics
Key Points:Analysis of Malicious Software Reverse Shell Traffic
Still working with the file from the previous chall.
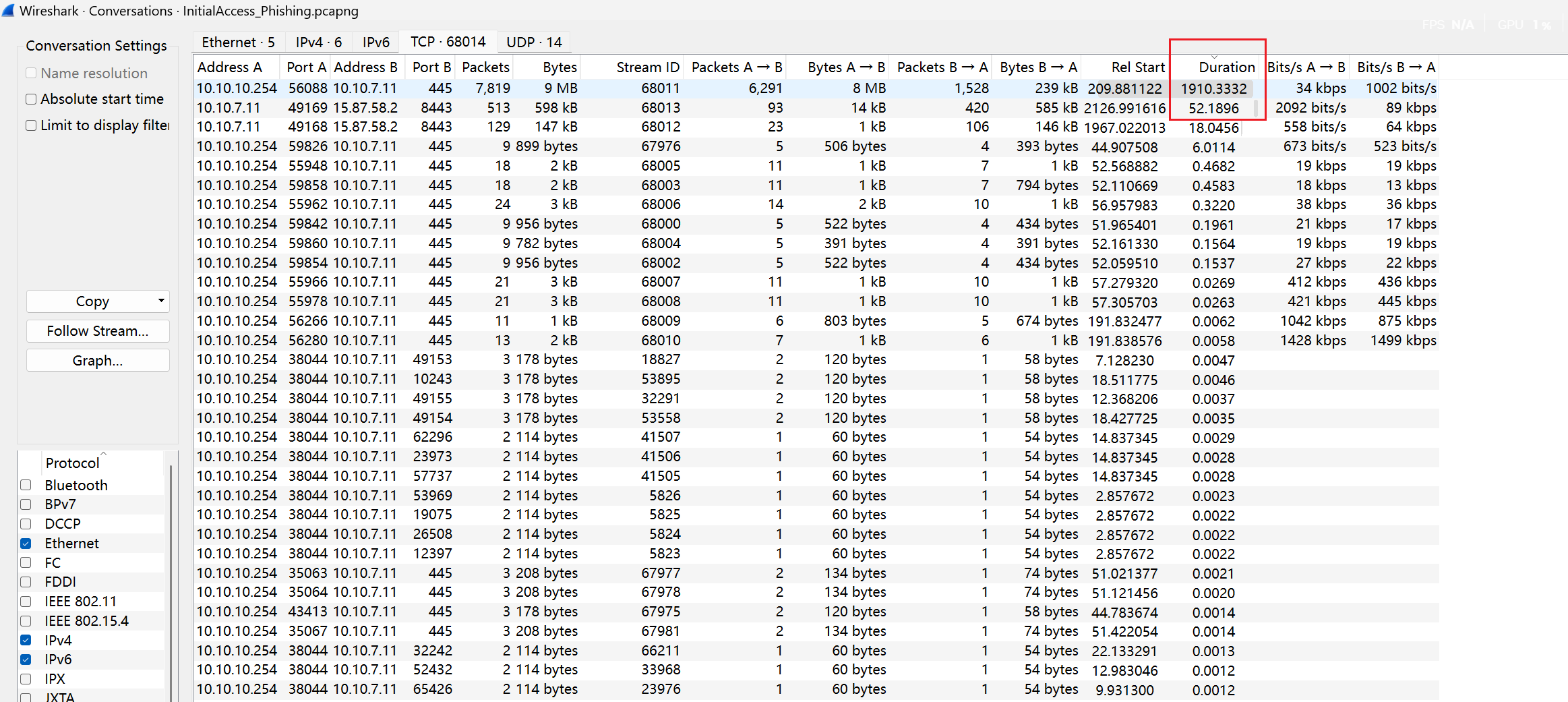
Clearly, this involves malware analysis. Following the hint and conventional approaches, go to Statistics -> Conversations:
You can first sort by the Duration of the conversations. The longest duration might indicate potential malicious activity:
Here, observing Address B, the first row is an internal IP, which is unlikely to be the callback target for a reverse shell. From an attacker’s perspective, it’s usually an external IP. Therefore, the likely candidate is 15.87.58.2:
ICS Windows Event Log Analysis
Home Improvement
Desc
A victim organization provided two Windows Event log files that they believe contain crucial logs containing information that shows how the adversaries brought offensive tools into the environment. They have provided you with these files for analysis.
What living-off-the-land tool did the adversary use to help bring a tool into the environment?
flag format: flag[xxxxxxxxxx] or xxxxxxxxxx
▼ View Hint
SABLOL
Key Points:
College, it ain’t easy
Desc
After identifying the technique the Ember Jackals used to transfer an offensive tool into the environment, we still don’t know what the tool is or what it does. Adversaries often rename or obfuscate tools to evade defenses.
However, there’s a way to recover the tool and identify its true name and function. Use the Security.evtx, PowerShellLogs.evtx, or PowerShellLogs.csv files to identify the tool.
What is the codename of the tool the adversary transferred into the environment?
Flag Format: flag[lots of strings]
▼ Unlock Hint for 1 point
The adversary already used the command to reassemble the executable. You just have to replicate it.
▼ Unlock Hint for 1 point
This problem can be solved manually, but that will be an incredibly tedious task with 1009 sections. Try automating your analysis.
Key Points:
ICS PCAP Analysis
Network Capture INT
Desc
Would you kindly identify the full Operating System name, version, and build number of the client machine that this PCAPNG was captured on?
Flag Format: xx-bit Windows xx (xxxx), build xxxxx
Free Hint: There are more than one interface and there are multiple builds in the attached PCAP.
▼ View Hint
Every packet is captured from a specific Interface id.
▼ View Hint
Each Interface device has its own Interface Description Block.
Key Points:
First of Many
Desc
The Ember Jackals have corrupted a.txt file that was retrieved over the network by one of our admins.
We need to identify the .txt file and extract out any hidden messages the Ember Jackals have graffitied inside.
Flag Format: LONGSTRINGALLTOGETHER
▼ View Hint
There is a way to extract files detected by Wireshark in the UI.
▼ View Hint
Finding the file transfer in Wireshark may be helpful to see what is going on.
▼ View Hint
The file extension of the file in question is “.txt”.
▼ View Hint
Concatenate multiple messages together, if any.
Key Points:
Corrupted Network Capture
Desc
Ember Jackals have corrupted a network capture file that may contain information on when they first began gathering info about our network. Help us restore the file to working order and recover the response data in the protocol capture.
What is the timestamp of the response packet?
Flag Format: Mmm DD, YYYY HH:MM:SS
▼ View Hint
It looks like the beginning portion of the file is corrupted
▼ View Hint
Recover or recreate a Section Header Block
▼ View Hint
The timestamp must be set to the correct epoch (What epoch value does the TIME protocol use?)
Key Points:
Silly Jackals, PCAPs are for Kids!
Desc
Ember Jackals have been probing some of our other servers. I have been able to capture some of their traffic but I think I messed up the capture somehow.
Please help make sense of the data and retrieve the ‘Originate Timestamp’ field from the ICMP packet so we can identify the time of day this scan occurred.
Flag Format: dddddddd
▼ Unlock Hint for 1 point
Network captures record the LinkType the frames were captured on
▼ Unlock Hint for 1 point
ICMP packets only operate on Ethernet network links
▼ Unlock Hint for 1 point
The LinkType field for the correct Interface ID needs to be fixed
Key Points:
Binary Analysis
Mortimer’s Admin Utility 1
Desc
Note: Use this attachment to solve the next three challenges.
In a strange turn of events, the Ember Jackals hired a young Mortimer Smith as an intern and ACME found a utility he left behind on one of the systems.
First, we need to do some static analysis to make sure there’s no flag-nanigans going on here…
▼ Unlock Hint for 0 points
Running it may be dangerous… you should just look at it.
▼ Unlock Hint for 0 points
This is way simpler than string theory.
Key Points:
Mortimer’s Admin Utility 2
Desc
In a strange turn of events, the Ember Jackals hired a young Mortimer Smith as an intern and ACME found a utility he left behind on one of the systems.
Yeah it’s definitely shady, and you should definitely not run it on your work computer… but you need the flag so… YOLO!
Note: A successful run of the tool will create a new local user (if run in Admin prompt). Creation of a new user, nor Admin privileges are required to solve the flag.
Flag Format: flag{strings here}
▼ View Hint
Hey, uh, uh, 1995 called! They want their “certain year called wanting its blank back” formula back.
Key Points:
Mortimer’s Admin Utility 3
Desc
In a strange turn of events, the Ember Jackals hired a young Mortimer Smith as an intern and ACME found a utility he left behind on one of the systems.
Oh geez… I really need to get Morty’s password. Can you retrieve it?
Flag Format: flag(datahere)
▼ Unlock Hint for 1 point
Good luck bruteforcing it…. we’ll check back with you at DISC 2030.
Key Points:
Reverse Engineering & PCAP Analysis
Desc
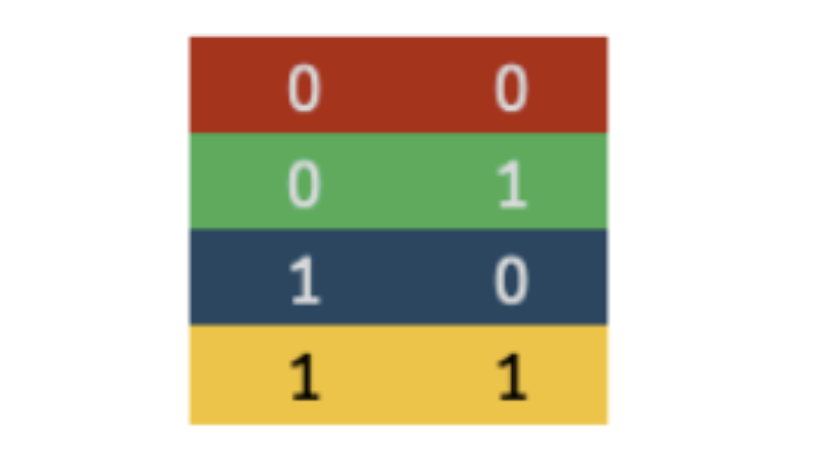
A security researcher alerted ACME Corp about proprietary information circulating on the dark web. You received a sample and immediately recognized the items. But that doesn’t make sense—why would Ember Jackals want that BIG piece of information? Unless … very very odd …
Assuming that you need 8 bits for each … hmmm …. item …. what is EJ really communicating?
Flag format: flag{XXXXXXXXXXX}
Free Hint: think of the absolute min number of bits.
Free (BIG) Hint:
View Hint
An image is worth 1000 words (or less, sometimes)View Hint
Only four colours (RGB+Y) .. that is very old-schoolView Hint
You can send bits via pulses, waves …. or colours?
Key Points:
Desc
Kiddy 1 is tough, but your team believes in you, and you are now receiving more artifacts to analyze. This time, it’s a PCAP from a corporate workstation—pretty standard. However, something feels off. It’s time to take a closer look.
Can you find the configuration file?
Flag format: flag{XXXXXXXXXXXX}
▼ View Hint
Protocol statistics are pretty useful to understand PCAPs: You can easily spot bytes!
▼ View Hint
I wonder if you can extract the components of the slide. I mean, the real components … the original ones.
Key Points:
Desc
Wow, you are making good progress. Your boss decides that you would be the lead investigator for the next issues. And just in time, you received another PCAP with more data to analyze. Seems like our alloys research was getting some unwanted attention. Have fun!
Can you find the message hidden in the data?!
Flag Format: flag[XXXXXXXXXXX]
▼ Unlock Hint for 0 points
Everytime I heard research I think of DNS, I mean, DNA.
▼ Unlock Hint for 0 points
Research, R&D … I am pretty sure I saw something linked to R&D somewhere.
Key Points:
Forensics Analysis
δραπετεύω
Desc
Note: Use the attached artifacts for the following four challenges.
We found our HMI for the heating system with an open browser Window, making a lot of noise. Someone or something has opened this. http://nyan.cat does not seem to be malicious itself, our research at http://http.cat also shows nothing weird. We successfully captured a triage collection from the system.
Can you investigate what might be off with this browser? Can we identify if someone left a “calling card”?
Flag format: flag{text}
▼ View Hint
What artifacts would a browser produce? We don’t have the full pcap.
▼ View Hint
Have you looked at the screenshot?
▼ View Hint
Does anything stick out? Maybe it needs some rotating.